Welcome
Red Seer Labs: Unleash Your Potential in Penetration Testing
Are you a student or professional eager to master the art of penetration testing and excel in the cybersecurity field? Red Seer Labs is your ultimate gateway to success. Explore our free and open-source offerings designed specifically for aspiring penetration testers.
Why Red Seer Labs?
Realistic Testing Scenarios: Step into the world of real-world attacks with Red Seer Labs. Experience immersive virtualized environments that mirror diverse network architectures, operating systems, and applications. Sharpen your skills by tackling lifelike scenarios without risking actual systems.
Advanced Threat Simulations: Red Seer Labs offers unparalleled opportunities to simulate advanced cyber-attacks. Test your mettle against network intrusions, social engineering exploits, and malware infections. Uncover vulnerabilities in a controlled environment and gain practical insights into remediation techniques.
Collaborative Learning Platform: Red Seer Labs provides a dynamic and interactive learning platform where aspiring penetration testers like you can engage in secure communication, knowledge-sharing, and peer collaboration. Exchange ideas, insights, and strategies with fellow students, fostering continuous growth and improvement as you navigate your penetration testing journey.
Partnership with Build Cyber: Red Seer Security proudly partners with Build Cyber, a respected non-profit organization, to offer you exclusive benefits. As part of this partnership, you gain access to Build Cyber's Apprentice and Mentorship Program, which provides invaluable guidance, mentorship, and hands-on experience in the cybersecurity field. This partnership also aligns with their Cybersecurity Certification Pathway Program, enabling you to advance your skills and knowledge on a structured certification track. Unleash Your Potential with Red Seer Labs! Empower yourself with the tools and experiences you need to become a proficient penetration tester.
Red Seer Labs offers realistic testing scenarios, advanced threat simulations, a collaborative learning platform, and a partnership with Build Cyber, enabling you to accelerate your growth and excel in the cybersecurity field. Take the first step towards a successful career in penetration testing. Join Red Seer Labs today and unlock your potential! Red Seer Labs - Your Path to Penetration Testing Excellence
Overview of the Lab Environments:
- GOAD v2 on Proxmox
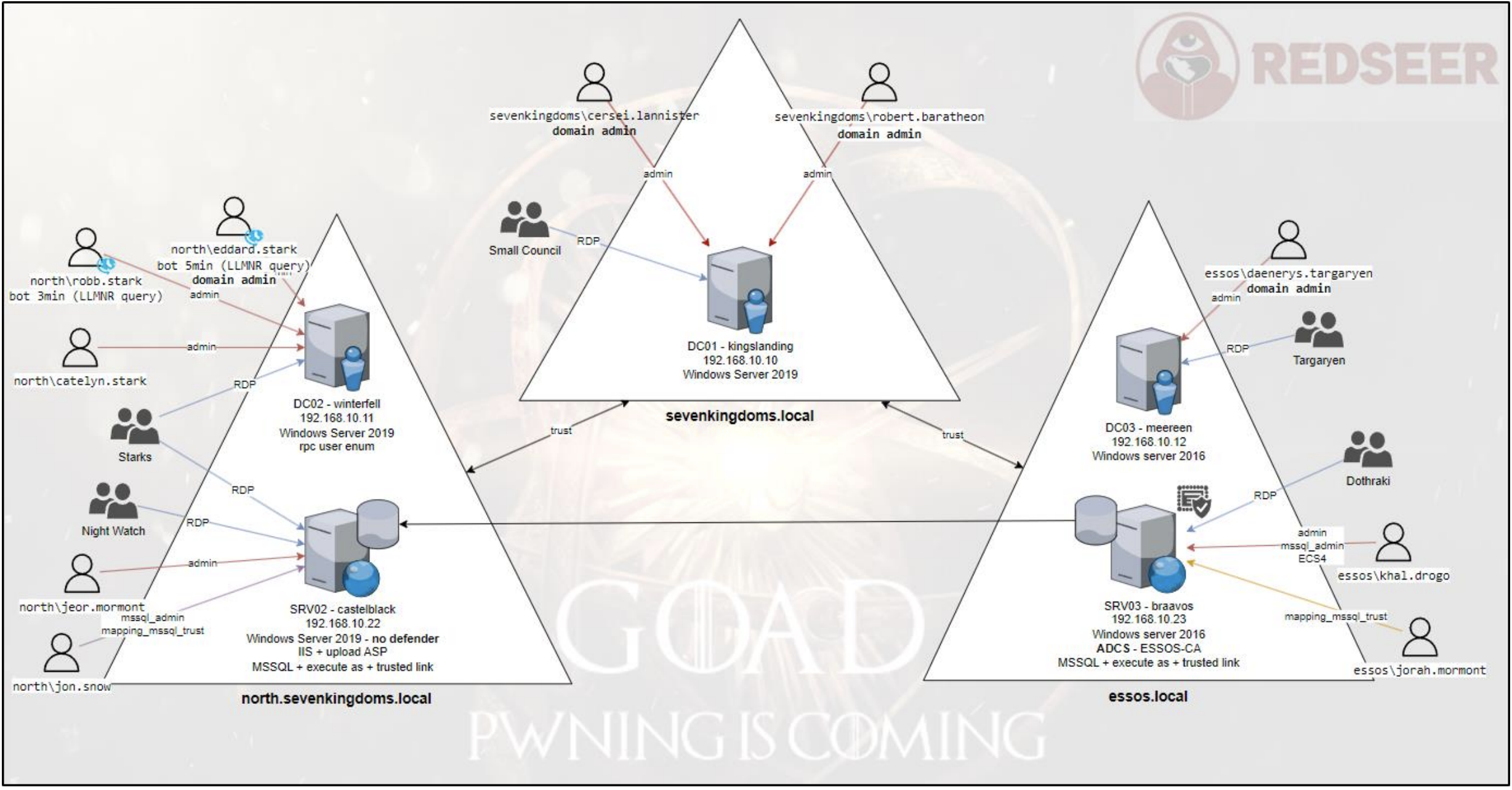 Special thanks to the creator of the original Game of Active Directory project. @M4yFly
Special thanks to the creator of the original Game of Active Directory project. @M4yFly
Red Seer Labs includes the following additional features, vulnerabilities, and exploitation paths:
- Password Reuse between Computers (PTH): Explore the impact of password reuse across multiple computers within the lab environment.
- User Password Spray: Perform password spraying attacks using the common password "Password" against user accounts.
- Password in Description: Investigate the security implications of passwords stored in user account descriptions.
- Anonymous SMB Share: Analyze the vulnerabilities associated with anonymous access to SMB shares.
- SMB Signing Disabled: Learn about the risks and consequences of SMB signing being disabled.
- Responder: Understand and simulate attacks using the Responder tool for network poisoning and credential theft.
- Zerologon: Explore the vulnerabilities and exploit techniques associated with the Zerologon vulnerability.
- Windows Defender: Assess the effectiveness and limitations of Windows Defender as a security solution.
- ASREPRoast: Exploit the ASREPRoast vulnerability to extract password hashes of service accounts.
- Kerberoasting: Perform Kerberoasting attacks to extract and crack Kerberos ticket hashes.
- Active Directory ACL Abuse: Investigate the impact of abusing Active Directory ACLs to gain unauthorized access.
- Unconstrained Delegation: Understand the risks associated with uncontrolled or misconfigured delegation in Active Directory.
- NTLM Relay: Simulate NTLM relay attacks to gain unauthorized access to targeted systems.
- Constrained Delegation: Explore the configuration and vulnerabilities related to constrained delegation in Active Directory.
- MSSQL Installation: Set up and configure Microsoft SQL Server (MSSQL) within the lab environment.
- MSSQL Trusted Link: Utilize trusted links in MSSQL to establish connections and explore associated risks.
- MSSQL Impersonation: Learn about and simulate impersonation attacks within MSSQL.
- IIS Installation: Install and configure Internet Information Services (IIS) for web application testing.
- ASP App Upload: Practice uploading malicious webshells and explore associated security implications.
- Multiple Forests: Experience and navigate scenarios involving multiple Active Directory forests.
- Anonymous RPC User Listing: Assess the risks and consequences of listing RPC users anonymously.
- Child Parent Domain Relationships: Explore the relationships and potential security implications between child and parent domains.
- Certificate Generation and LDAPS: Generate certificates and enable LDAPS (LDAP over SSL/TLS) for secure communication.
- ADCS - ESC (Enterprise Subordinate Certification Authority) 1/2/3/8: Work with and understand the features and functionalities of ADCS Enterprise Subordinate Certification Authorities.
- Certifried: Utilize Certipy tool for certificate-related operations and analysis.
- SamAccountName/NoPac: Investigate the security implications and risks associated with SamAccountName/NoPac configurations.
- PetitPotam Unauthenticated: Explore and understand the attack techniques and impact of the PetitPotam vulnerability.
- PrinterBug: Learn about and simulate attacks leveraging the PrinterBug vulnerability.
- Drop the Mic: Assess the risks and consequences of "dropping the mic" attack technique in Active Directory.
- Shadow Credentials: Investigate and exploit shadow credentials left behind in the environment.
- MITM6: Simulate and understand Man-in-the-Middle (MITM) attacks using the MITM6 tool.
- LAPS Integration: Add and explore the functionalities of Local Administrator Password Solution (LAPS) within the lab environment.
- GPO Abuse: Understand and exploit Group Policy Object (GPO) misconfigurations and abuse.
- WebDAV Integration: Set up and explore the functionalities and vulnerabilities of WebDAV within the lab environment.
- RDP Bot: Deploy a bot to simulate multiple RDP connections and analyze associated risks.
- Full Proxmox Integration: Leverages the capabilities of Proxmox for full integration and virtualization within the lab environment.
- OpenVPN Access: Lab environment is fully accessible from any remote internet connection.
-
Command & Control: Integration with various C2 Frameworks, including Metasploit, Cobalt Strike, Sliver & Havoc.
-
More lab scenarios and vulnerable environments under development and coming soon.
Technical PDF.
Detailed information on the GOADv2 Enterprise Environment & Vulnerabilities
